In the run-up to the 2016 U.S. presidential elections, Democratic candidate Hillary Clinton received a serious blow from a series of leaks coming from the email account of her campaign chairman John Podesta. Hackers were able to access the contents of Podesta’s account by staging a successful phishing attack and stealing his credentials.pass
Podesta is one of the millions of people whose passwords get stolen as a result of social engineering attacks or data breaches every year. A recent research by security firm 4iQ found a 41-gigabyte file being sold on the dark web, which contained 1.4 billion usernames and passwords.
It is now evident more than ever that passwords are not enough to protect online accounts. With each of us managing dozens of online accounts, keeping every password unique is becoming increasingly burdensome. That’s why we often reuse passwords, which can lead to chain attacks when one password is revealed to hackers. As computers grow faster, stronger and more affordable, we’re forced to create more complex passwords to protect our accounts against brute-force attacks. And as quantum computing gradually turns from myth to reality, no amount of complexity will protect us against hackers. And finally, as long as our passwords are stored somewhere in servers, a hacker can always get a hold of them by breaking into those servers.
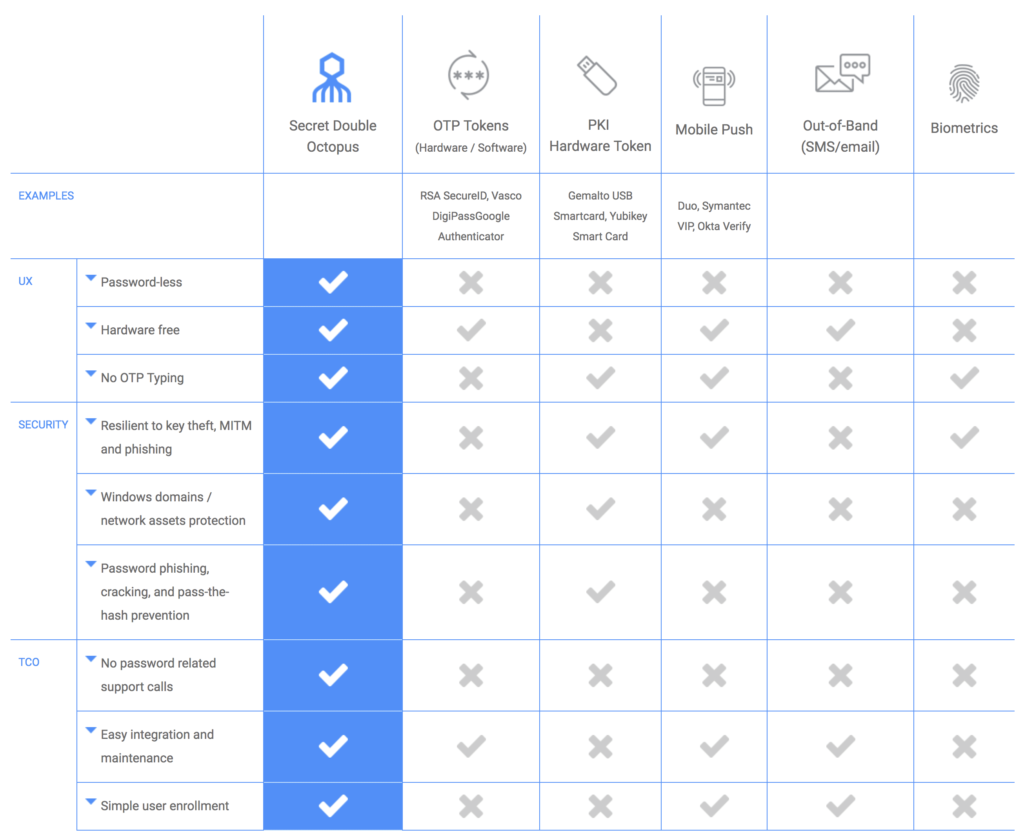
Compare Authentication Methods
The Role of MFA in Protecting Online Accounts
Some businesses have tried to move toward two-factor and multi-factor authentication (MFA) to make up for the flaws of passwords. Multi-factor authentication implies using two or more varying methods to authenticate users when they try to access sensitive accounts and digital assets. MFA removes the single point of failure imposed by passwords. This means hackers who gain access to online account passwords through phishing attacks or data breaches still won’t be able to access those accounts because they won’t be able to produce the second factor.
Older generations of multi-factor authentication involved using passwords and a second token. For instance, this could be a password and an SMS code sent to a phone associated with the account, or a time-based passcode generated by a mobile app. However, these methods had two fundamental problems:
- Unfriendly experience: Most users find it bothersome to go through an extra step to verify their identity each time they want to access their accounts. This consequently pushed users to deactivate 2FA on accounts or frequently used devices, which opens the way for new types of attacks and account takeovers.
- Insecure methods: Although traditional two-factor authentication (2FA) is more secure than plain passwords, it’s not uncompromisable. It still involves the use of passwords, which have very distinct vulnerabilities, and the secondary factors often have their own security holes. A crafty hacker will be able to intercept, replicate or deactivate 2FA codes with enough effort.
What the Future Holds for MFA
The next generation of multi-factor authentication (MFA) mechanisms will combine impregnable security and ease of use, ensuring that users have a frictionless experience while preventing hackers from finding and exploiting loopholes.
Passwords will most likely disappear and give way to more reliable and user-friendly methods. A recent survey conducted by Secret Double Octopus found that most company employees find passwords unwieldy and burdensome, and would prefer biometric authentication as the main method for securing their online accounts.
“There is no doubt that over time, people are going to rely less and less on passwords,” adding that passwords “just don’t meet the challenge for anything you really want to secure.” Bill Gates
Biometrics were previously expensive and inaccurate, but recent years have seen precise and affordable fingerprint, iris and face scanners integrated into a large number of consumer devices. Companies will be able to leverage these technologies to replace passwords a Bring Your Own Device (BYOD) approach to authentication.
An example of modern multi-factor authentication is Secret Double Octopus’s passwordless identity verification solution. Secret Double Octopus obviates the need for storing any form of secrets, be it passwords or security keys. Moreover, every authentication attempt is performed over multiple channels, each using a separate security method. Meanwhile, the user experience is seamless and frictionless, requiring only a tap or a fingerprint verification on the Octopus Authenticator app.
As hackers become more sophisticated in their methods to take over sensitive accounts and steal critical information, enterprises must also improve their defenses. The next generation of multi-factor authentication technologies will make sure you’re ready to face the security challenges that lie ahead.
Compare Authentication Factors