It should come as no surprise that the global market for multi-factor authentication (MFA) technology is expected to grow fourfold by 2025. On the one hand, software continues to eat the world and online services are becoming increasingly important in every aspect of daily life, business, health care, politics, military, etc. On the other hand, data breaches are also rising in size and frequency. Consumers and organizations are becoming more aware of the need to protect their digital identities and assets, and naturally, MFA is one of the most important steps toward achieving that goal.
According to Transparency Market Research, “The global multifactor authentication market is expected to rise to US$20,444.9 million by 2025 from US$ 4,829.2 million in 2016. Over the forecast duration of 2017 and 2025, the global multifactor authentication market is prognosticated to expand at 17.7% CAGR.”
But with the MFA landscape being so diverse, the question is, which technique will grab the lion’s share of the market? There’s a reason to believe push authentication will lead the charge, especially since it enjoys support from standards bodies such as NIST, is in line with industry standards such as PCI DSS, and is compliant with regulatory requirements such as HIPAA and GDPR.
In case you’re not familiar with push authentication, it’s basically a technology that verifies the identity of users by sending a push notification to a mobile device associated with their account during the login process. We’ve previously covered the benefits of push authentication. In a nutshell, these are the main strengths of push authentication:
- It’s cost effective in terms of implementation and maintenance
- It’s more secure than other forms of MFA
- It’s easy to use and doesn’t introduce complexity to the user experience
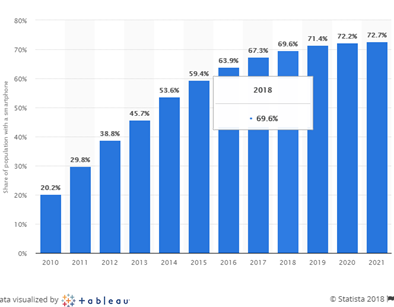
According to Statista, smartphone adoption rate will continue to rise in the next few years, which means authenticator apps and phone-as-a-token MFA will likely continue to become more popular. Meanwhile, it is expectable to see SMS and software OTPs slowly becoming obsolete because they’re less secure and setting them up and employing them is more complex for users.
In its most recent Digital Identity Guidelines, the NIST retracts its support for SMS-based MFA, recommending that “implementers of new systems SHOULD carefully consider alternative authenticators” and explicitly stating that “OOB using SMS is deprecated, and may no longer be allowed in future releases of this guidance.”
In the past few years, most vendors of authentication technologies have improved their solutions to support push authentication. Some of the companies that provide push authentication as an option include RSA Security, SecureAuth Corporation, Microsoft Corporation, CA Technologies, Symantec Corporation, Vasco Data Security International Inc., Okta Inc., Ping Identity, Gemalto, Entrust Datacard Corporation and HID Global Corporation.
With the market for push authentication carving a niche of its own in the broader authentication landscape, how can you decide which solution is best for the needs of your organization? We’ve put together a few questions that you should ask when evaluating a solution.
Will you be ditching passwords?
There are basically two ways you can use push authentication. The band-aid approach most services use for authentication is based on push notifications as a complement to your password login, which means after users enter their username and password, they’ll receive a notification on their mobile device, which they have to confirm to complete the login cycle.
A more innovative approach is using push with a second non-password factor to achieve passwordless authentication. A user log into an account by entering a username and completing a push authentication challenge without the need to enter passwords. If your goal is to ditch passwords, then you’ll have to make sure the service you choose supports the latter feature.
What type of data does the push notification include?
MFA solutions are out-of-band (OOB), which means they take place outside of the channel where passwords are exchanged and thus make the authentication process more secure. But MFA processes themselves can become the target of man-in-the-middle (MITM) attacks. MITM is a type of cyberattack in which a malicious actor intercepts the communications channel between two parties to steal or manipulate information.
When choosing a push authentication technology, it is important that you know what type of information is contained within the notification sent to the user device and what measures have been taken to protect it. There’s always the possibility that someone is eavesdropping on the user’s smartphone and will be monitoring everything they receive.
The most secure types of push authentication are those that use zero-knowledge proof, which means no sensitive information is exchanged between the server and client. A challenge is sent to the user which can only be solved with data held in their device. This means that even if a hacker manages to intercept the data contained in the notification, they won’t be able to use it to impersonate the user and hijack their account.
Is the push solution compatible with your organization’s IT and cloud infrastructure?
Depending on the size and geographical expansion of your organization, you might be using various types of network and directory services. You might use Active Directory to manage the user account of your employees. You might be using a corporate VPN to allow users to connect to their accounts from different networks and geographical locations. You might be using RADIUS to connect and consolidate different networks.
The push authentication solution you choose must be flexible to adapt to your organization’s network and server requirements. For some organizations, a solution that implements the SAML standard will be enough to tie in with all their services. Others will require support for more advanced protocols, such as RADIUS. Make sure you raise and discuss this with your vendor.
How easy will it be to implement your push authentication of choice?
When considering a push authentication solution, you’ll have to consider some of the costs and steps you’ll incur if you want to integrate it into your service. Does it adhere with the authentication standards that your application supports? Is the process well-documented? Does the vendor provide support in the integration process? Do you have the in-house coding talent to implement the solution?
Also worth considering is whether the solution is cloud-based, on-premise or hybrid? Some solutions will give you the ability to deploy a local installation of their solution on your own corporate servers, while others require that you exclusively authenticate your users through their servers. This can be a deal-breaker for organizations that require full ownership of the authentication process.
Will the solution improve the user experience (UX)?
One of the most important factors that will determine how successful your push for MFA will be the user experience. If you introduce additional challenges to the authentication process, users will likely become disenchanted with your push authentication solution and disable it (if they can), compromising their—and your organization’s—security in the process.
Fortunately, for the most part, push authentication solutions are easy to use. But you also have to make sure they’re easy to set up and maintain for your users and provide good fallback support in case users lose or change their devices. Also, it is preferable to enable users to use passwordless push authentication and leverage biometric 2FA if it is supported by the solution.
What level of assurance your solution of choice provides?
There’s no one-size-fits-all recipe that will fulfill the security requirements of every organization. The best way to verify whether a solution is suitable for your organization or not is to adopt a risk-based approach (RBA) to evaluate what level of assurance you need. RBA involves doing research of the potential risks to your business from different perspectives and checking whether a security solution you want to adopt will drive your overall risk factor lower or higher.
A passwordless push authentication solution will provide better user experience and lower your risks of suffering password related breaches. This means that your IT staff will have to deal with less overhead of account restoration and password reset and can focus on more critical tasks. utilizing a bring your own device approach (BYOD) will also reduce the authentication solution implementation cost. However, you have to make sure that the solution itself is secure and does not introduce your organization to new vulnerabilities.
Closing thoughts
Given its overall strengths, push authentication is an innovative and reliable approach to securing online identities. However, every organization must make their own assessment of authentication solutions and make sure that it fulfills their needs.
That said, Secret Double Octopus passwordless push authentication solution provides maximum security at the lowest cost. Secret Double Octopus uses Shamir’s Secret Sharing, utilizing multiple channels to authenticate users to provide extra security against different types of attacks, which means it is immune to man-in-the-middle attacks.
A true authentication process can only take place between a real server and user device and can’t be spoofed by a third party.
The secured push authentication leverages on-device biometric or PIN to make it a complete MFA solution without the need for passwords.
Secret Double Octopus has also been designed to integrate into various types of networks structures and server technologies to make sure it can fulfill the needs of all corporations.