Proving your identity in order to authenticate yourself and gain access to some kind of system is more of a challenge than most people realize. This process has to be designed so that on one hand it’s as easy as possible for the user of the system to gain access, while on the other it’s as difficult as possible for someone who isn’t authorized to gain access. We’ll look at how tokens fit into the authentication process, as well as the different types of tokens – including hard tokens, soft tokens, and everything in between.
MFA basics
A simple password doesn’t cut it for most systems, especially ones with higher risks or sensitivity attached to them. One of the most effective ways of ensuring authentication is with “Multi-Factor Authentication”, or MFA.
There are 3 independent factors classes for authentication:
1) Something you “know”: a password or PIN, or an answer to a question
2) Something you “have”: a token, credit card or mobile device
3) Something you “are”: biometric data, such as fingerprints, or behavioral data such as keystrokes
With multi-factor authentication, a user must prove at least 2 of these independent factors.
This introduces the concept of a token; something that is used to prove 1 of the 2 independent factors required above. Authentication tokens are generally divided into 2 groups: a Hard token, and a Soft token. Hard tokens (Hardware token = Hard Token) are physical devices used to gain access to an electronically restricted resource. Soft tokens (Software token = Soft token) are just that; authentication tokens that are not physically tangible, but exist as software on common devices (for example computers or phones).
Hard Tokens Have Done Their Bit
When it comes to security tokens, most people think of hardware tokens – such as smart cards, Bluetooth tokens, one-time password (OTP) keyfobs, or USB keys. The most common one, RSA SecureID, has been in the market since 2002 (yes, that’s already 15 years) a new contender in this field are Universal 2nd Factors (U2F), utilizing a new standard in authentication Fast Identity On-Line (FIDO)
Hard tokens have a number of challenges: They’re relatively expensive, easy to lose, and their administration and maintenance often take a heavy toll on IT departments. They’re also vulnerable to theft, breach of codes, and man-in-the-middle attacks.
Soft Tokens: Where UX meets TCO
Software tokens have a number of advantages over hardware tokens. They can’t be lost, they can be automatically updated, the incremental cost for each additional token is negligible, and they can be distributed to users instantly, anywhere in the world.
Nowadays, instead of carrying around an extra piece of hardware, and given the fact that everyone these days has smartphone, soft tokens have been incorporated into smartphones (usually in the form of an app).
In multiple recent reviews Gartner addressed the increased use of phone-as-a-token methods, noting in their Technology Insight for Phone-as-a-Token Authentication report that “authentication methods that co-opt users’ mobile phones as tokens are widely adopted”, and “by the end of 2019, 50% of enterprises using phone-as-a-token authentication will use mobile push in preference to other modes, compared with less than 10% today.” Gartner’s “Phone-as-a-Token: category relates to all kinds of mobile-based authentication, including soft tokens, OTP and push notification.
Interestingly, the report also warns that “security and risk management leaders must carefully evaluate them against trust and user experience needs, especially when the phone itself is the endpoint device.”
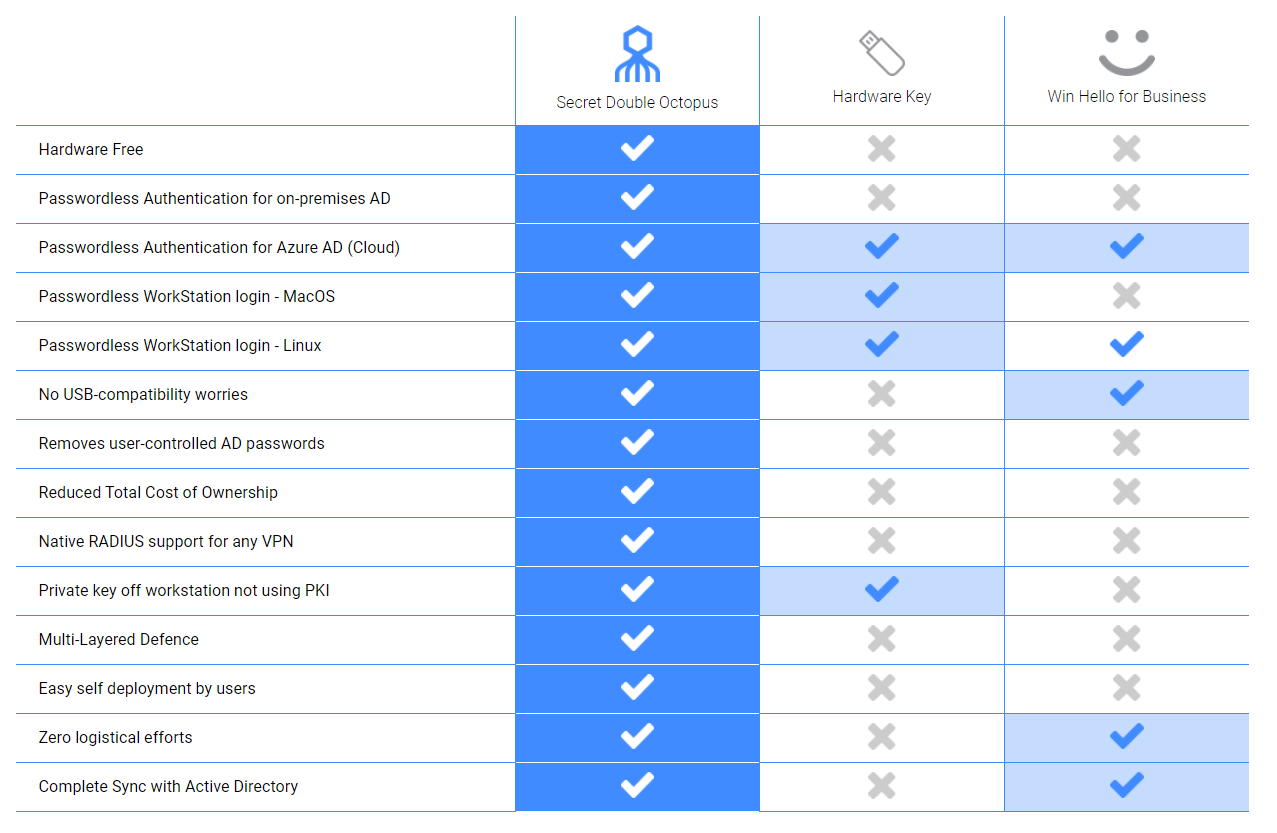
The Right Authentication Solution For You
Over the next 5 years, Gartner sees a move away from hard tokens, with some of the reasons for this move outlined above. Soft tokens, especially when incorporated into smartphones, are certainly where the industry is heading, but have their drawbacks especially from a security perspective.
For the highest levels of both ease and security, Secret Double Octopus offers its Password-free Authentication, Multi-Factor Authentication (MFA) through its mobile-based Octopus Authenticator, which leverages the power of secret sharing to enable authentication within enterprises that gives high assurance and is password-free.
Secret Double Octopus removes the nuisance of authentication – One-time-Password (OTP), SMS, and authentication tokens, while offering increased security – with no additional hardware involved.
Octopus Authenticator is the industry’s only solution to overcome the challenges inherent in the soft tokens available on the market today. With multi-route security made possible by the secret sharing scheme, Secret Double Octopus’ Octopus Authenticator offers an unobtrusive and frictionless user experience and the best level of security.