Among the elements of cybersecurity, the human factor in data security continues to be the most difficult to control–and cybercriminals know it.
Of all the areas of a network vulnerable to human error, remote access channels are probably most susceptible to attack and a likely route for hackers trying to breach an organization.
Common remote access solutions targeted by hackers include Virtual Private Networks (VPN), the Microsoft developed Remote Desktop Protocol (RDP) and other Virtual Desktop Infrastructure (VDI) solutions.
While remote access solutions offer certain security benefits, as highlighted on the Octopus Blog numerous times, the gains in security are easily forfeited if access is not properly gated with a high-assurance user authentication solution. On this blog, we discuss the threats to remote access from several angles and attempt to aggregate the most essential points on this vital topic.
For an in-depth discussion of the different challenges associated with remote access, be sure to check out the following blogs::
- VPN MFA
- Remote Desktop Authentication
- The Case for Securing Remote Access Protocols Through 2FA
- Why your corporate VPN needs two factor authentication
Threats to remote access
Remote access comes with a security cost. Allowing users to access local resources from a remote location makes it very difficult to detect when an attacker is attempting to access through the same channel.
Phishing Campaigns
Phishing continues to be one of the most widely used attack methods in cybercrime today. Recent data indicates that 85 percent of enterprises have been victimized by a phishing campaign. As demonstrated by a string of recent of attacks, from the eosGAS Scam to a RAT Trojan campaign targeting the financial industry in the U.S. and Britain, hackers are regularly utilizing phishing methods to gain control of remote access channels.
Password Theft
Stealing credentials is especially problematic when remote access channels are available, as it allows a hacker to access an organization’s internal network assuming an identity of an authorized user. Year after year, incidents of password theft show the vulnerabilities of password-based authentication.
Brute Force Attacks
If attackers can’t steal a password, they can use dictionary attacks and other automated tools to guess weak ones. These tools have been at the disposal of cybercriminals for years, and their sophistication and efficiency has only increased over the years. The incident that likely carries the strongest reminder of this fact was the 2016 attack on the Alibaba-owned e-commerce site TaoBao. In February of that year, as many as 21 million accounts were compromised when hackers ran a database of tens of millions of passwords through Alibaba’s cloud service.
Exploiting out of date devices and applications
A large part of cybersecurity is the perpetual race taking place between hackers and developers. Cybercriminals seek to find flaws in operating systems and applications that they can capitalize on, while IT companies work to identify and patch those flaws before the hackers. With attackers constantly developing exploits for new software vulnerabilities discovered and users neglecting to patch vulnerable software, even after a vulnerability is known, users are left exposed to attack. Some of the most high profile breaches in history–the Equifax breach of 2017 being an excellent example–were made possible because victims were using outdated versions of critical software.
Remote Desktop Protocol (RDP) security threats
“Many businesses use Remote Desktop to enable remote for employees. But by granting such access, these businesses have made it much more likely they’ll be targeted and hacked”.
Microsoft’s RDP is a useful tool for remote access, allowing users to access files and applications from any location via a remote channel. For example, an employee can access all of their work computer’s programs, files and network resources from their home computer and tech support personnel can remotely access workstations that need repair. Unfortunately, RDP also has a major pitfall, as users will often unknowingly leave RDP client ports open to the Internet, leaving themselves vulnerable to attackers. In September, U.S. researchers identified the Phorpiex Worm designed to scan the web for Internet-facing Remote Desktop ports that were left open. Once identified, these endpoints can be targeted using brute-force attacks.
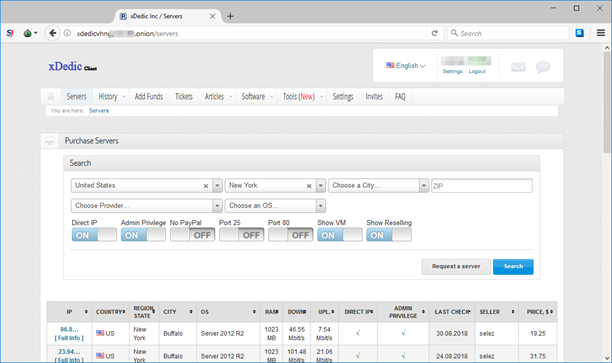
Cybersecurity outlet Welivesecurity has shown how easy it is to buy remote access to a breached server:
“What you are buying here is remote access to a system that belongs to someone else, in other words, unauthorized access, very likely obtained illegally,” […] “The operators of this market disclaim any responsibility for what you do with your purchases; however, it is clear that the market is populated by sellers who have hacked the remote access credentials of their victims’ systems.” Stephan Cobb, Senior Security Researcher
Buying remote access on the Darkweb, source: Welivesecurity
Protecting Remote Access
More and more employees are relying on remote channels to access company data. While remote access systems have logistical and economic benefits, without appropriate controls they become a potential security threat. This is due to the fact that systems such as RDP and VPNs provide outside access to a business network and resources which is typically gated by the ability of the user to present a valid credential. When those credentials are easy to steal, then remote access quickly turns into a vulnerability.
What to look for in a user authentication solution for remote access?
Agent or agentless
Server performance monitoring solutions are designed to measure and log the activity of users on company servers and desktops. Broadly speaking, there are two types of monitoring solutions. Agent-based platforms require a software program to be installed on each computer to be monitored. Agent-less platforms do not employ any software agent, but rather use a gateway server, or capture data as it flows between a machine and the servers they are accessing. Agent-less platforms have the upside of not requiring installation and maintenance for every individual machine, saving IT and administrators time and resources.
Password or passwordless?
Upgrading a remote access solution while leaving authentication password-based leaves users and managers with all the security and logistical burdens of maintaining passwords. These include the risks of password cracking and theft discussed above, requiring employees to remember and store their passwords, as well as the high costs of password related help desk calls.
Learn more about Passwordless authentication
One solution to secure access for all platforms
When choosing the authentication platforms, managers should be looking for a solution that will cater to all of their remote access tools from VPN, to VDI, to RDP.
Combining Multi-Factor Authentication (MFA) and Single sign-on (SSO)
Authentication platforms that provide Single Sign-On (SSO) capabilities require fewer logins from your employees. By combining MFA and SSO companies can bolster security while simplifying the authentication process for employees.
Secret Double Octopus Remote Access Authentication Solution
- Supports all secured access needs for all tools and platforms
- Passwordless, which means seamless, unfettered authentication with no risk to workflow from lost or stolen passwords
- Agentless, requiring no additional in-house installation work on devices
- High assurance, using the mathematically unbreakable Secret Sharing authentication scheme
- No hardware tokens or additional devices to carry and safeguard
Schedule a demo to see how Secret Double Octopus can help you secure remote access