Proven at Scale, Unmatched Flexibility
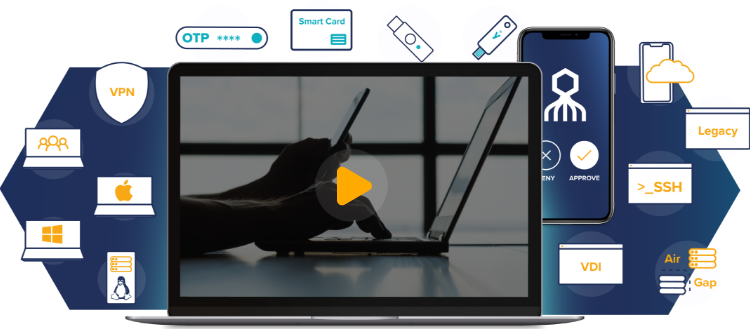


















From defense contractors and financial institutions to government agencies and law firms –
The Octopus Authentication Platform eliminated all employee passwords in enterprises across the globe.
Traditional MFA is built on passwords. Not only is this the biggest source of data breaches and security risk to your organization, but employees are frustrated and resigned to the user experience.
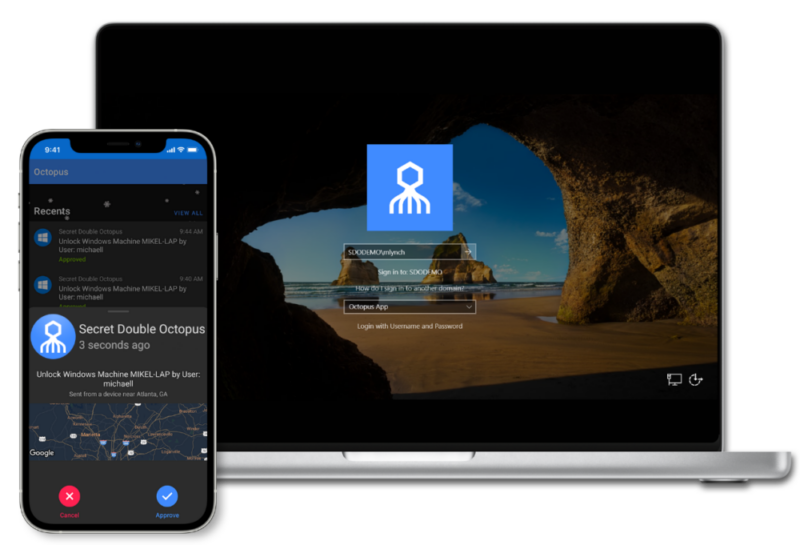

Only SDO offers a non-certificate-based approach to becoming phishing-resistant and meeting regulatory compliance.

The end to multiple MFA methods and endless resets. The Octopus Platform ensures reliable and robust authentication that always delivers – online or offline.

Enable modern MFA for admin use cases to servers and shared accounts, and centralize MFA management for universal coverage

SDO lives by the "no app left behind" motto and offers the richest support for non-SAML enabled legacy application support out-of-the-box.
Today’s automated man-in-the-middle attacks have changed the game for phishing defense. Enjoy state-of-the-art adaptive capabilities that thwart this threat in its tracks.
Meet the Zero Trust era with an industry-leading solution that has been recognized as “Best-in-Class” for enterprise workforce protection. For us, identity is the new perimeter.
Get ready for an enterprise FIDO-based passwordless future today. Whether it be Passkeys or traditional security keys, we leverage the latest in smartphone biometrics and standards to modernize authentication.

FIDO 2 solves many problems with legacy certificates and is backed by internet giants. The Octopus authenticates Window, MAC, and Linux desktop users with self provisioned FIDO2 keys, and includes a certified FIDO2 server for web app authentication out of the box.

Going passwordless doesn’t have to be a risky one shot deal. Our unmatched flexibility allows you to start with a specific use case and go fully passwordless over time.