What Is Passwordless Authentication–and Why Does the Workforce Need It?
Passwordless authentication is a type of MFA that verifies user identity without relying on passwords or other memorized secrets. Passwordless generally means a form of multi-factor authentication or MFA, though simpler forms of passwordless authentication exist such as email-delivered magic links.
Instead of using passwords, identity can be verified based on a “possession factor.” For example, possession of an object that uniquely identifies the user because no other user would be expected to have the object (e.g. a registered mobile device or an issued hardware token). Identity can also be confirmed using “inherent factors” such as a person’s biometric signature (e.g. fingerprint, voice, face or retinal scan).
Why is it needed?
There are three types of factors that can be used in an MFA solution – something you are (biometric authentication), something you know (password), or something you have (mobile device). An authentication method based on secrets the user knows (such as a password, passphrase, or PIN code) remains susceptible to theft, sharing, and reuse by users, and requires constant management and handling by both IT and your workforce.
Even with added factors, traditional MFA falls into this category. In eliminating “what users know” from the login workflow, nearly all passwordless MFA solutions stipulate at least one factor based on ‘something users own or have’ to strengthen authentication, and many add elements of ‘something users are,’ typically verified with biometrics. The end-of-the-day reason the modern workforce needs passwordless MFA is, in a word, phishing. Traditional MFA remains vulnerable to phishing–as evidenced by the fact that 80% of breaches still start with compromised credentials–and modern man-in-the-middle (MITM) and MFA Fatigue attacks. (Learn more about phishing-resistance in our other blog).
How Does Passwordless Authentication Work?
One framework that guides most journeys towards passwordless authentication comes from FIDO, a group consisting of tech giants that got together to define specifications for how online security should work. Ultimately, the expectation is that most if not all methods will also support or be built on Public Key Infrastructure or PKI architectures.
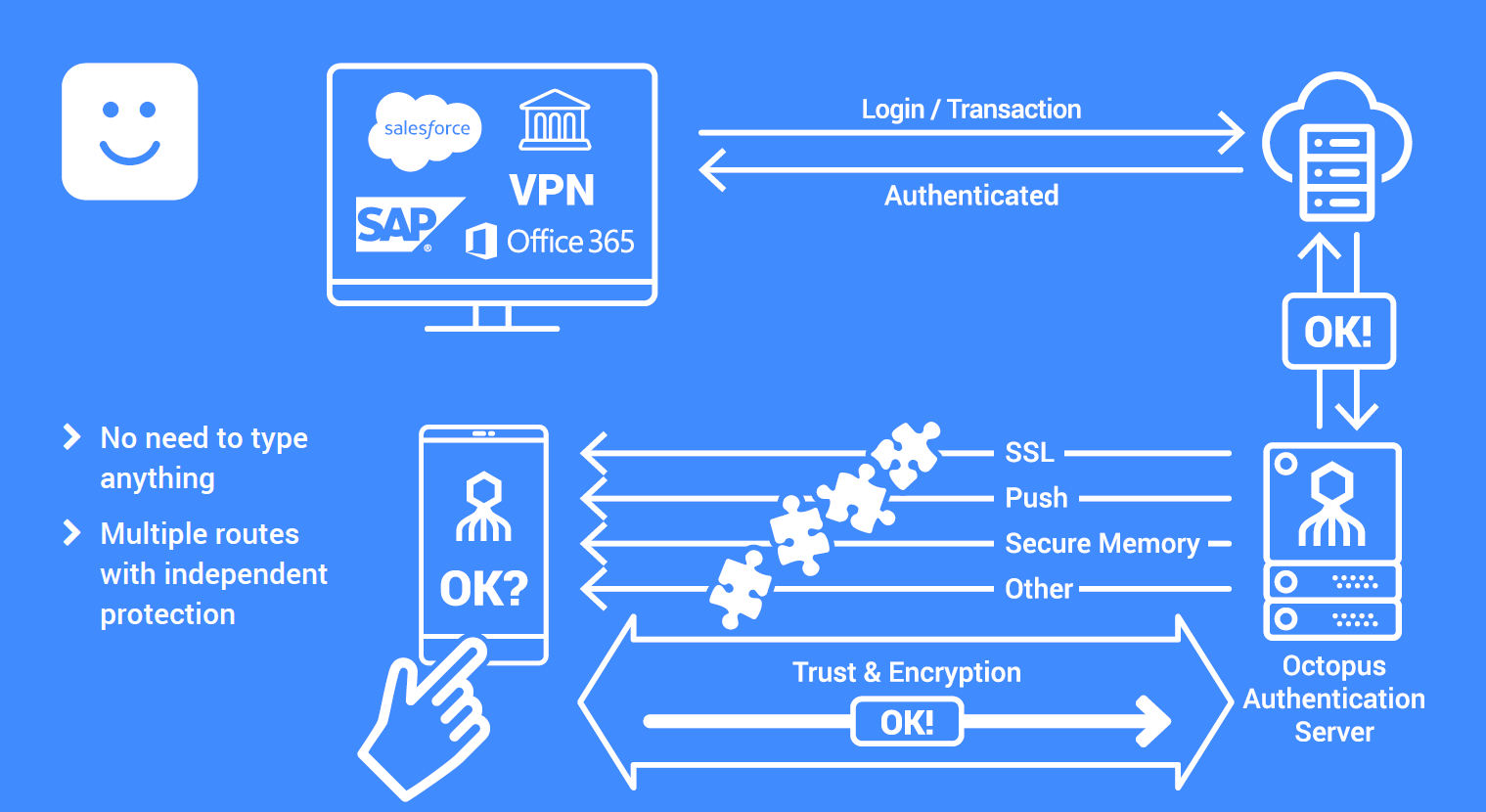
Benefits of Passwordless Authentication
AuthN and AuthZ, or authentication and authorization, are the two steps taken to provide users access to classified information and privileged assets. With traditional password-based authentication, user experience dictates that a user only needs to log in once with a password to authorize their credentials, since entering a password multiple times can be cumbersome.
With passwordless, users can authenticate multiple times per session to ensure they are authorized to view the information they’re trying to access. Other benefits of a passwordless approach can be broken into two main categories: business and technical.
Business:
- User Experience (UX): Passwordless authentication means no more user-memorized secrets; this streamlines the authentication process.
- ROI: Passwords are expensive, and they require constant maintenance from your IT staff. Removing them reduces support tickets and frees IT to deal with real problems, all while contributing to your ROI.
- Better security: User-controlled passwords are a major vulnerability because employees reuse passwords and are able to share them with others. Passwords are one of the biggest cyberattack vectors and have been responsible for 81% of breaches (According to Verizon DBIR). They also lead to attacks such as credential stuffing, corporate account takeover (CATO), password spraying, and brute force attacks.
- Invalidates already compromised credentials: Companies may have compromised credentials floating around on the dark web and not even know it. Going passwordless invalidates all these.
Technical:
- Supported on a variety of systems: Passwordless does a good job of integrating with whatever platform you’re already using.
- Decentralized: Because passwordless doesn’t require a master list of passwords or a password manager, it’s decentralized, meaning a breach doesn’t compromise the security of your entire system.
- Advances Zero Trust security posture: Zero Trust is exactly what it sounds like – never trust any user at any time. Maximum security is achieved by constantly authenticating, all without the user even knowing it.
What Is the Difference Between Passwordless and “Regular” MFA?
Passwordless is a form of MFA, but traditional MFA is significantly less secure. So, how exactly do they stack up against each other?
As we said earlier, when someone talks about MFA, they usually mean a traditional authentication solution that includes “something you have” (e.g. a mobile phone that receives one-time verification codes. You can enter to complete authentication). The problem lies, however, in the first authentication factor – the user password that can be easily compromised leading to bad actors gaining access to information they shouldn’t have – which traditional solutions still contain.
A passwordless login solves problems traditional MFA may cause (or at least not fix), from a choppy user experience and “MFA fatigue” to serious problems like compromised credentials showing up on the dark web.
Why Secret Double Octopus for Passwordless?
Secret Double Octopus is the industry leader for workforce passwordless authentication having won numerous awards for our proven enterprise-level solutions. More than 150K users authenticate with the Octopus platform with no compromising data breaches having occurred.
Our passwordless solution is a complete one, known as “full passwordless.” Some companies sell passwordless solutions that are not truly passwordless as they require passwords behind the scenes, or when using single sign-on (SSO).
The Octopus platform offers the broadest enterprise use case coverage and is ideal for industries such as higher education and critical infrastructure. Mandates from the Biden administration and other governments call for critical infrastructures and other industries to move toward Zero Trust security postures and phishing-resistant MFA.
Passwordless MFA represents the best approach for phishing-resistance but making the transition can be a big job. SDO offers the ability to slowly transition from password-based to passwordless, with milestones along the way to becoming a fully passwordless organization. We focus on adding passwordless to your existing infrastructure, instead of forcing you to restructure to make our solution fit.