Well before the COVID-19 pandemic, the headlines were dominated once again by the notion of state-sponsored cyberwarfare. Due to the surge in tensions between Iran and the U.S., and in the wake of the strike that killed top Iranian commander Qassem Soleimani, the Department of Homeland Security issued a warning of a potential retaliatory cyberattack by Iran or its proxies.
But the ‘shadow war’ raging in the cybersphere between Iran and the U.S. is nothing new, and dates back more than a decade. And if the past is any indication, Iranian-backed cyberattacks will largely target the commercial and private sectors. However, Iranian threat actors have also been linked to cyber strikes on government agencies, infrastructure and universities, and this is likely to continue as well.
In September 2019, cybersecurity company Secureworks released a detailed report about a widespread phishing campaign by hackers linked to the Iranian government. According to Secureworks, the hackers had targeted more than 60 universities in Australia, the United States, the United Kingdom, Canada, Hong Kong, and Switzerland, stealing intellectual property that could either be exploited or sold for profit.
A researcher from Secureworks described the so-called COBALT DICKENS campaign as “a direct response to sanctions [imposed on Iran] and an exodus of academic talent from Iran to countries where they are able to participate in and benefit from open and collaborative academic research.”
This report was built upon similar findings by the cybersecurity firm in 2018, when it discovered Iran-based phishing attacks against hundreds of universities in 14 countries.
Against the backdrop of such a tenuous situation, any organization could essentially become the next victim of a nation-state actor. Here’s what you need to know about past Iranian phishing campaigns and how you can protect your own organization against similar attacks, regardless of your sector or industry
How hackers breached university networks
Like many online security incidents, the attacks against the universities began with phishing emails containing links to malicious websites. The COBALT DICKENS threat group used compromised accounts to send emails to members of each targeted university, urging them to renew their library subscription.
The hackers took care to craft their fraudulent messages in a way that incited the recipient to take a specific action, instructing them to click on a link contained in the email in order to purportedly renew their library subscription before it expired.
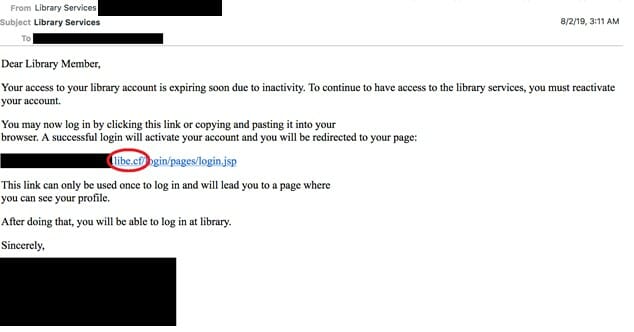
Phishing email fraudulently urges recipients to click on a malicious link to renew their subscription before it expires (Source: SecureWorks)
Since the email came from a seemingly legitimate source, many recipients trusted it and clicked on the link, believing they would be taken to the login page of their university library. Instead, they stepped into a well-crafted man-in-the-middle (MitM) trap that covertly redirected them to a webpage that looked identical to their respective library’s, but was actually controlled by the hackers. To make these malicious websites look legitimate and to avoid triggering alarms by browsers, the hackers had also taken care to register 20 domains and valid SSL certificates for the campaign.
After the recipients entered their login credentials to the masquerading page, the hackers stored a copy of that information. The hackers then redirected the targets to the actual library page, where they would continue to work without noticing that they had just given away their username and password to dangerous nation-state actors.
From there, the hackers could secretly access the accounts and steal valuable information without alerting the account holders or network administrators.
How hackers are leveraging password weakness for attacks
Even after Secureworks first discovered and disclosed the COBALT DICKENS phishing campaigns in 2018, the hackers continued to target universities into 2019 without changing their modus operandi. So far, the hackers have been able to compromise 380 universities in 30 countries.
The main reason for the success of these phishing campaigns was that most of the targeted universities used only passwords to secure their user accounts. As long as organizations rely on single passwords to prevent unauthorized access to user accounts, it’s only a matter of time before some hacker manages to trick a user into compromising their credentials and giving away access to valuable and often confidential resources.
Secureworks researchers recommended organizations implement multi-factor authentication (MFA) to protect their valuable assets from similar attacks. “While implementing additional security controls like MFA could seem burdensome in environments that value user flexibility and innovation, single-password accounts are insecure. CTU researchers recommend that all organizations protect Internet-facing resources with MFA to mitigate credential-focused threats,” the researchers noted in their report.
MFA requires users to present an extra token to prove ownership when signing in to their accounts. This includes using a USB security key or confirming an access request in an authenticator app on a mobile device associated with the account. MFA ensures that even if a careless user accidentally types their credentials in a phishing webpage, the hacker on the other end won’t be able to hijack the account.
Unfortunately, despite wide coverage and constant warnings by various cybersecurity firms and experts in the aftermath of the COBALT DICKENS phishing campaigns, very few of the targeted universities have implemented MFA. In several cases, many users have refrained from activating MFA because they found the extra sign-in steps too irritating. Even more troubling is the fact that this remains true when faculty members and students across the world are almost completely reliant on remote access, and thus are much more susceptible to phishing and other attacks.
The option that offers the best of both worlds
Fortunately, universities have an option that combines convenience and security. Passwordless MFA enables organizations to implement authentication mechanisms that are easy to use while also protecting their users from phishing and man-in-the-middle attacks that lead to account takeovers.
Passwordless authentication removes the very thing that has enabled hackers to hijack so many accounts: passwords. Without storing or exchanging passwords during the identity verification process, organizations leave nothing for cybercriminals to steal.
Universities should move fast to adopt advanced authentication solutions that integrate easier than ever before with all popular operating systems and existing technologies that most organizations already employ (such as VPN or RDP). This reduces the technical and financial barriers for the adoption of passwordless authentication, which are common worries for government-funded institutions and those that have limited financial resources.
With cybersecurity playing an increasingly vital role in conflicts between nation-states, government-backed hackers are setting their eyes on the most valuable and vulnerable organizations. It’s time that universities take the security of their user accounts more seriously.