In a perfect world, individual workers each get assigned one user identity — a single, secure account and set of credentials or another safe way to access company resources. In reality, workers often need to share accounts — and worse yet credentials — as they collaborate on the job at hand.
Sharing accounts and credentials across multiple team members clearly poses risks to cybersecurity. But as we’ll see here, a new approach to multifactor authentication (MFA) equips IT to secure shared accounts, deliver elite IT support, and more.

What you’ll learn
- How shared accounts work
- The pros and cons of using them
- How passwordless authentication secures and unlocks their untapped potential
What is a shared account?
Shared accounts allow multiple users to access the same machine (PC, Mac, Linux workstation, etc.) or other corporate resources using a single set of credentials. In most cases, that means logging in with the same username and password.
Research shows that, at any given time, most companies maintain an average of 11 different shared accounts that each get accessed by multiple employees on a regular or temporary basis. Now that we’re all hyper-aware of the dangers inherent in using (let alone sharing) passwords, common accounts would not continue to exist if they didn’t offer a business distinct and compelling advantages.
What are the benefits of using a shared account?
Shared accounts facilitate collaboration and reduce the burden and cost of administration. These accounts allow multiple users on different teams or shifts to work together seamlessly without disrupting business operations. When incidents or security events occur, having multiple admins who can log in accelerates triage, investigation, and response.
In most cases, streamlining login workflows also costs less than provisioning new or temporary workers and contractors with multiple accounts and maintaining all their identities in backend directories. Shared accounts avoid excessive provisioning efforts and fees associated with little-used licenses.

What are the use cases for shared accounts?

Scenarios that lend themselves to the use of shared accounts within enterprises fall into three main categories:
Securing Shared Accounts for Frontline Workers
This group includes government and public safety operations, healthcare and hospital settings, and production or factory floors in utility companies or manufacturing operations. Any scenario where many different users come and go quickly throughout the day or on an as-needed basis.
In most cases, streamlining login workflows also costs less than provisioning new or temporary workers and contractors with multiple accounts and maintaining all their identities in backend directories. Shared accounts avoid excessive provisioning efforts and fees associated with little-used licenses.
80% of the Global workforce is deskless: 27B workers.
source:desklessworkforce2018.com

Shared Account Use for Shift Workers
Retail outlets, restaurants, hospitals, and other venues subject to the “the changing of the guards” also tend to see higher employee turnover. Shared accounts make it easier for IT to cope with the churn and allow managers and more experienced workers to jump in and help trainees resolve issues to keep the lines moving.
Managing IT Administration with Shared Accounts
Multiple IT professionals notoriously share ‘System Admin’ privileges and credentials. Shared access helps ensure there’s always an expert available to respond quickly when performance issues and cyber threats first occur.
The transient nature of these three types of use cases adds risk that leads IT teams to manage identity and access for these workers differently than they do for employees sitting in corporate offices.
How do shared accounts add to security risk?
Shared accounts might well be the ‘poster child’ for the tension that exists between speed and security, and between convenience and compliance. Sharing credentials (for privileged system admins in particular) flies in the face of every modern Zero Trust cybersecurity best practice. It makes for atrocious password and identity hygiene and promotes gaps in audit trails needed to document compliance.
Sharing access across multiple individuals and teams also increases the potential for insider attacks and just-plain-bad behavior. Users know that signing in with shared credentials means anything they do on that machine during a session cannot be traced back to them. At least not without security cameras or colleagues being present.
Last but definitely not least, lesser-used credentials associated with shared accounts almost always get written down by users who, not having set them themselves, wouldn’t otherwise remember them when they go to log in.
Regulators defining rules to secure shared accounts
Along with obscuring accountability, sharing credentials creates gaps in visibility that disrupt audit trails and full transparency. Some industry regulators don’t acknowledge the existence of shared accounts or appear to make allowances for their uniqueness. HIPAA, for example, clearly stipulates, “one user, one identity.” No exceptions.
Others, like ISO 27001 and PCI, acknowledge the inevitability of shared access and attempt to outline preventative controls for safely authenticating users. These standards set the bar for compliance high, particularly the stipulation within PCI that every action taken be attributable to an individual user – a near impossibility when everyone logs in using the same credentials.
The good news here is that, once enterprises and regulators deem shared accounts a ‘necessary evil,’ the challenge of securing them becomes more straightforward.


Securing shared accounts with Passwordless MFA
Once you decide to go passwordless, the question becomes, “Which solution should we choose?” The Octopus Passwordless Authentication Platform delivers four unique advantages and satisfies many more use cases than competing solutions:
As with all modern approaches to MFA and single sign-on (SSO), making the login process passwordless makes for a great first step to Zero Trust identity hygiene. Users can’t write down, lose, or accidentally reveal passwords that don’t even exist.
- Works with any preferred method of authentication – FIDO, smart cards, tokens, push notifications, biometrics – whatever IT and users prefer
- Provides 100% enterprise use case coverage and a unified login experience for Windows, Macs, Linux, legacy, and custom apps onsite, online, or in the cloud
- Replaces passwords with ephemeral machine-generated tokens that users never know exist
- Compatible with existing password-based apps and systems without redesign
- Provides complete phishing resistance with no change required by IT, such as recoding applications or rebuilding of directories required
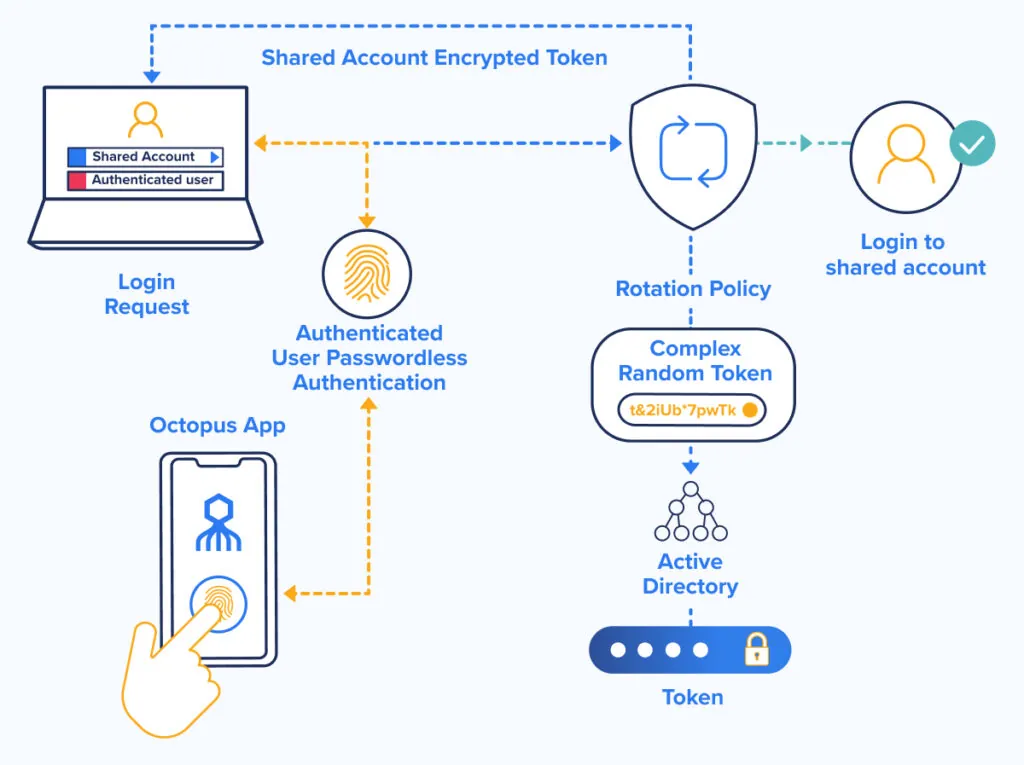
How Double Octopus Safeguards Shared Accounts
The SDO platform inserts a transparent layer of identity verification into the process of authenticating into shared accounts. Workers and contractors follow the same steps to log in as they do for everything else. Behind the scenes, the Octopus verifies that the individual is indeed authorized by IT to access the shared resource, then the Octopus uses the ephemeral token to complete authentication in the backend.
Octopus verifies, tracks, and logs access activity by individuals to ensure visibility and traceability to satisfy compliance mandates. This allows enterprises to safely extend their use of shared accounts to more use cases where it makes good business sense.
Demo: secure shared account login for frontline workers
In this demonstration, three production floor workers attempt to log into a shared Windows workstation. Two have been authorized, JKimberly and Fred, while one, Austin, has not. Each worker presents their phishing-resistant FIDO badge card to the workstation for access.
Secure shared accounts unlock IT innovations
Once a shared account is made secure and auditable, interesting and innovative new user cases can be developed. Here is one example of how Octopus helped a NY law firm enable secure White Glove IT services to maintain millions of dollars in revenues when ‘top dollar’ professionals needed IT support and computer software provisioning (read the full story).
Securing Shared Accounts for White Glove IT Support
Unless they’re related, no IT professional relishes the thought of sitting with the CEO while they configure or troubleshoot the boss’s computer. IT teams face similar pressure not to tie up professionals whose time gets billed at high rates, like attorneys, accountants, and investment brokers who command $500-1000 per hour.
Shared accounts – and specifically secure share accounts – enable an elite caliber of “White Glove” IT support that doesn’t require a service client to be present or on the phone in order for IT support professionals to complete configuration, updates, and repairs.
Instead of needing the user to be present to simply enter their passwords and admit the IT professional, Octopus allows the IT person to log in as the user, a unique and practical use for securing shared accounts. The safe, temporary use of shared accounts streamlines the processes of onboarding users, setting up computers, and troubleshooting performance issues.
The process usually goes faster without involving and inconveniencing users, delivering a clear and quantifiable benefit for IT and the whole company. Users can make phone calls, go to meetings, or grab a latte and return to find IT gone and their computers ready to go.

SDO vs. PAM: Key Differences in Securing Shared Accounts
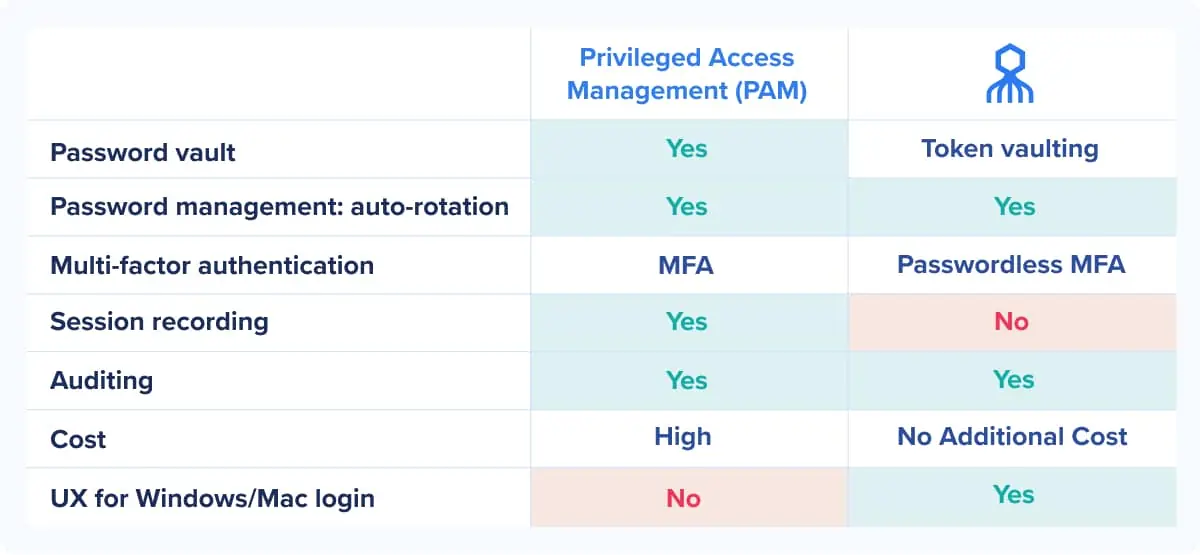
We are asked frequently by companies “Is Octopus a privileged access management (PAM)?” The short answer is no, it is not a PAM.
PAM solutions are commonly used for sharing admin credentials to access privileged systems. PAM systems provide mechanisms to track which IT Admin checked out and checked in credentials and a recording of the session activity. Alternatively, Octopus provides high-assurance MFA that delivers some of the similar outcomes of securely accessing shared accounts, but Octopus does it in a different manor and is not a PAM.
Octopus: Comprehensive Passwordless MFA for Shared Accounts
The Octopus provides the industry’s only enterprise-wide passwordless MFA use case coverage. Unlike other partial passwordless solutions that only work with SSO and Windows machines, Octopus eliminates vulnerable passwords from every access in the enterprise, including shared accounts.
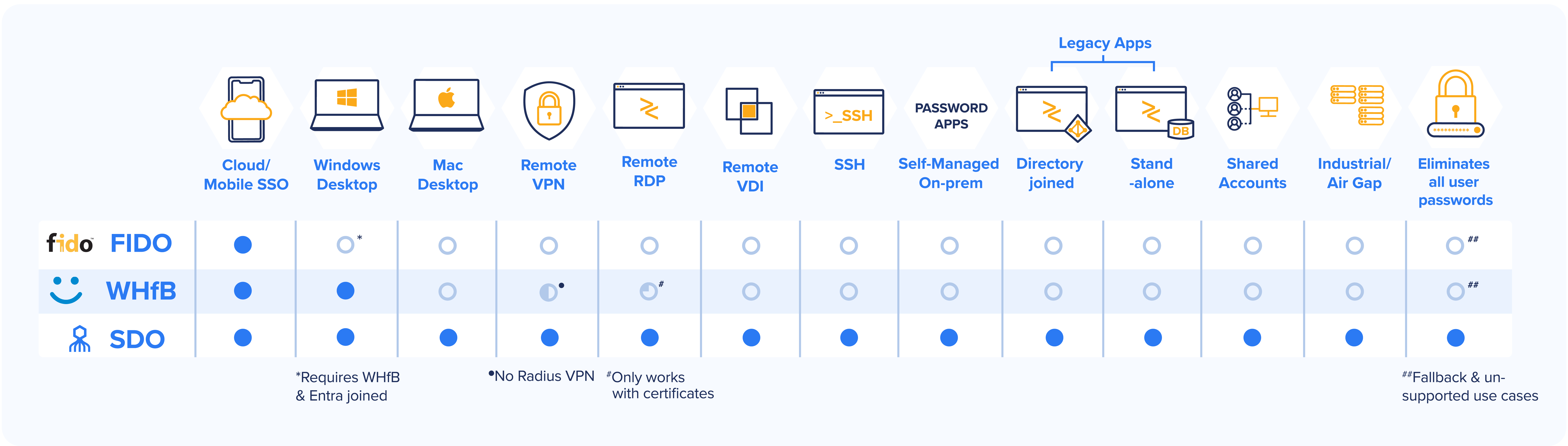
The Octopus platform makes the use of shared accounts simpler, safer, and more extensible, without IT having to redesign applications or rearchitect directories. Octopus enables secure shared accounts that:
- Maintain business continuity and maximize worker collaboration
- Provide phishing-resistant, high-assurance authentication
- Extends the same simple user experience across all systems
- Maximizes visibility and control to document who has access and when they logged into shared resources
For more information read the securing shared accounts solution brief or watch our on-demand webinar.
