In the past years, advances in technology, a growing number of horrifying data breaches, and increasing awareness of the need to protect online personal and corporate accounts have led to growing efforts in creating multi-factor authentication (MFA) technologies. But while the dream of creating authentication mechanisms that don’t rely on just memorizing and typing passwords dates back to many years, never before have we been closer to realizing it.
A big step towards MFA is credited to the involvement of the FIDO Alliance, an open industry association focused on helping to reduce the world’s over-reliance on passwords. The alliance is tasked with creating an authentication standard that can be adopted by all organizations across the world.
FIDO, which stands for Fast Identity Online, was jointly founded by several tech companies including PayPal and Lenovo. In the years that followed, many more companies joined the alliance, including tech giants of the likes of Google, Microsoft, and Amazon. FIDO also counts large hardware manufacturers like Intel and Samsung among its members, as well as several financial institutions such as Visa, MasterCard, and American Express.
Asymmetric Encryption
Over the course of its existence, FIDO has developed several specifications for authentication mechanisms. The specifications can be implemented with a wide variety of technologies such as fingerprint sensors, facial recognition, or hardware tokens.
The fundamental protocol used in all versions of FIDO is asymmetric cryptography. As opposed to symmetric cryptography, where a single key is used for both encryption and decryption, asymmetric cryptography uses separate keys to encrypt and decrypt data.
Asymmetric encryption is the basis for public key infrastructure (PKI), which is used in FIDO authentication technologies. For every user, public and private key pair is generated. The public key is stored on the servers of the service provider and used to verify users’ identities and encrypt their information. The private key is exclusively stored on users’ devices and used to sign in to authentication challenges and validate users’ identities and decrypt their information. PKI makes sure that even if a hacker breaches the servers of the service provider, they won’t be able to hijack user accounts or access the sensitive information they store.
Making sense of the confusing FIDO specifications
Over the years, the FIDO Alliance has developed a number of different standards and specifications, some of which build upon each other. The terminology can be a bit confusing to the uninitiated. Here’s a quick breakdown of what you need to know:
What is FIDO?
The first FIDO specification, published in December 2014, included two components: The Universal Authentication Framework (UAF) and the Universal 2nd Factor (U2F).
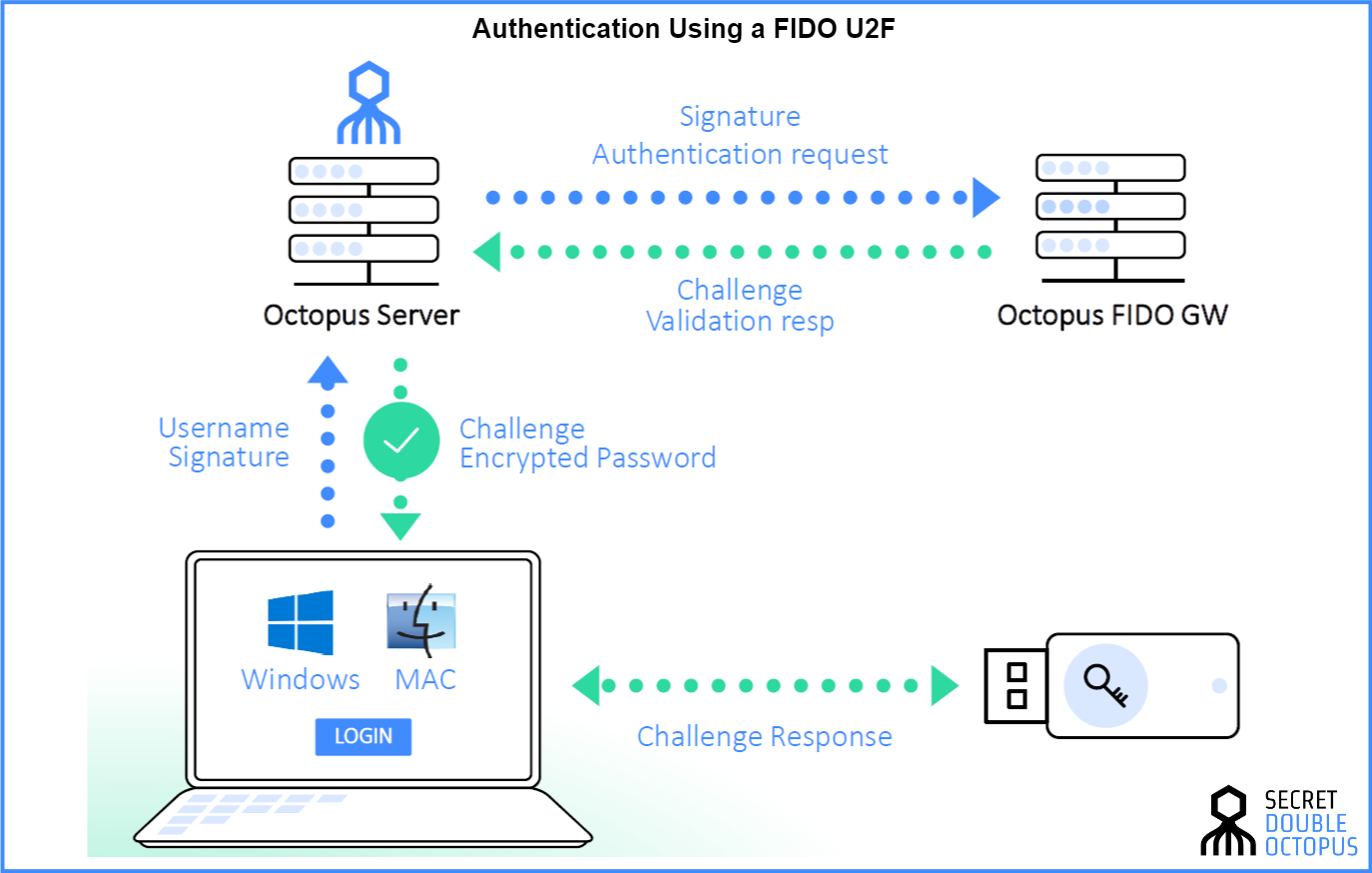
U2F is the standard for physical security keys that act as a second factor (2FA) to the passwords of your online accounts. U2F keys are usually connected to your computer via USB, but there are also near-field communication (NFC) and Bluetooth Low Energy (BLE) models that can be used for mobile devices. U2F devices use the public encryption key scheme to protect your account. The private key is stored exclusively on the U2F device and never leaves it, which makes it much more secure than SMS- and time-based 2FA methods, which can be spoofed by crafty hackers.
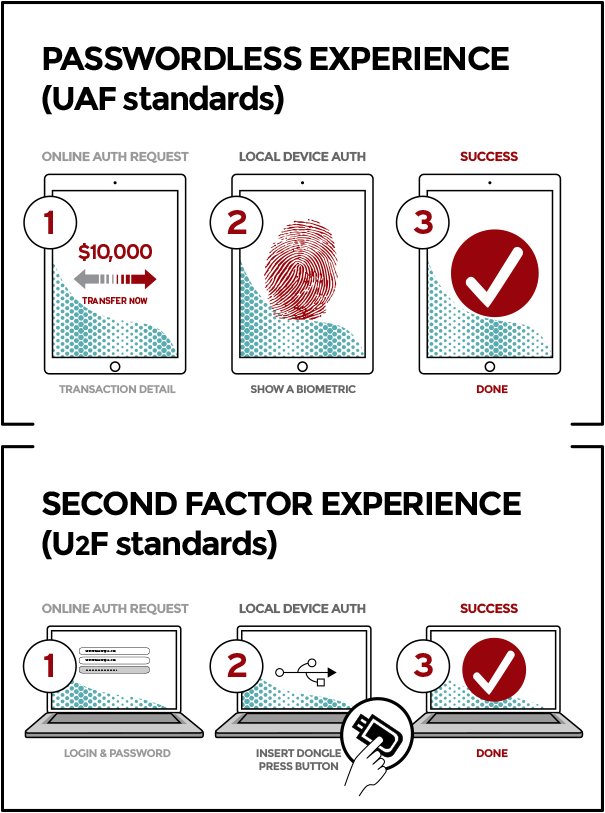
The UAF protocol is a standard that allows services to adopt passwordless and multi-factor security. When creating accounts, users register a device of their choice with the service and specify a local authentication mechanism such as fingerprint scanning, facial or voice recognition, entering a PIN, etc. As U2F, UAF creates a key pair, stores the private key on the device and the public key in the service’s servers.
Whenever users want to log in to a UAF service, instead of typing a password, they just need to repeat the UAF method they had signed up with, such as running a fingerprint scan on their device.
What is FIDO2?
In April 2018, the alliance launched FIDO2, the updated and upgraded version of its original specifications. FIDO2 was meant to pave the way for easier adoption of secure, passwordless authentication for a wide range of online services and user devices.
The main component of FIDO2 is Web Authentication (WebAuthn), developed in collaboration with the World Wide Web Consortium (W3C). WebAuthn is a set of standards and web application programming interfaces (APIs) that can add FIDO-based authentication to supported browsers and platforms. This means users will be able to log in to their favorite mobile and web applications using biometrics, mobile apps or FIDO keys.
WebAuthn was meant to make FIDO authentication more accessible to users that use a variety of technologies. The standard is supported by all popular browsers, including Chrome, Firefox, Edge and Safari. Windows 10 and Android also provide native support for WebAuthn, the alliance provides a status page that follows the implementation of the WebAuthn in popular browsers.
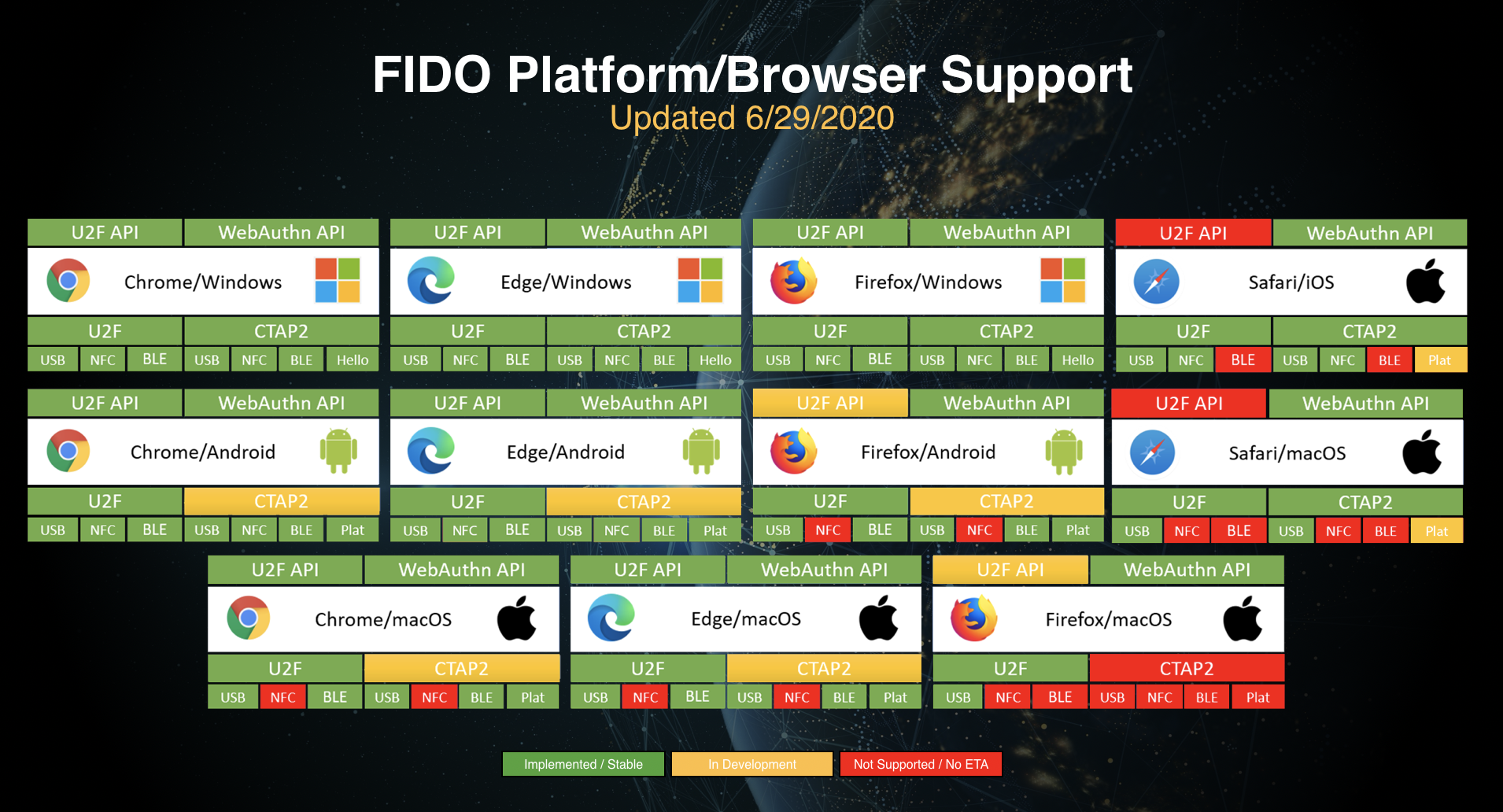
Current WebAuthn and CTAP support status – see here for updates
With the advent of FIDO2, the alliance retained the U2F standard but relabeled it as Client to Authenticator Protocol (CTAP1).
In the same release, FIDO also introduced CTAP2, which is basically the same as U2F but relaxes its requirements to also include mobile devices as acceptable external authenticators.
Key features
- FIDO 1.0:
- U2F/CTAP1: Standard specifications for physical two-factor authentication (2FA) keys
- UAF: Standard specifications for passwordless authentication technologies
- FIDO 2.0:
- WebAuthn: A standard set of web APIs to allow passwordless authentication in browsers
- CTAP2: Specification for the usage of physical keys and mobile authenticator apps to implement 2FA and passwordless authentication
Out-of-band (OOB) security tokens
One of the key ideas that make FIDO authentication secure is using out-of-band (OOB) methods to authenticate user identities. OOB authentication is especially resilient against smash-and-grab data breaches, in which hackers compromise a server and gain access to many user accounts.
FIDO authentication can be performed in hardware or software. Some hardware FIDO keys include a trusted platform module (TPM) to handle user identities. A TPM is a piece of hardware that can store sensitive information such as private encryption keys and is resilient against physical tampering. FIDO keys such as Yubico’s Yubikey product line all contain secure modules to protect users’ private keys.
FIDO can also be implemented in software through mobile applications as a software token, leveraging the mobile enclave and biometric capabilities of smartphones. Mobile authenticators leverage hardware and security modules that exist on the user’s device, such as facial recognition and fingerprint scanners, to protect the user’s security key.

How does FIDO authentication work?
FIDO uses public-key cryptography to provide secure and convenient authentication technologies. For every online account that uses FIDO, there is a public and private key that enables services to validate the identity of users.
How does the FIDO enrollment process work?
When the user signs up with a FIDO-enabled service, the following happens:
- After users fill the registration form, the service asks them to choose a FIDO authenticator of their choice. This can be a FIDO-compliant authenticator app or a security key or a TPM.
- Once the user specifies her authenticator, the FIDO device generates a cryptographic key pair.
- The device sends the public key to the service, which registers it in its user’s database and associates it with the user’s account.
- The private key and other sensitive information such as fingerprint scans and facial data never leave the user’s device.
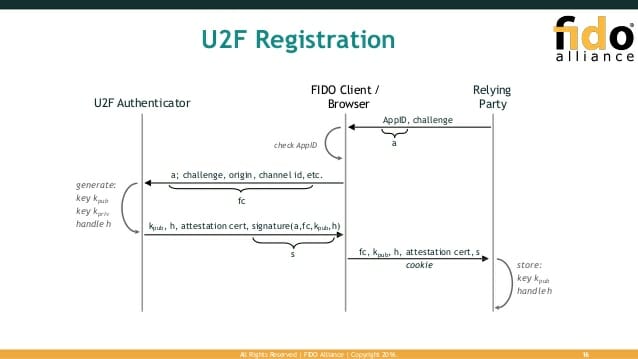
How does the FIDO Authentication Process work?
When users want to log in to a FIDO-enabled service, the following happens:
- The user presents herself by providing a username or email.
- The service presents a cryptographic challenge.
- The user uses her FIDO authenticator app or key to sign the challenge.
- After signing the challenge, the user sends the signed challenge back to the server.
- The server verifies the response with the user’s corresponding public key, and if successful, gives the user access to the account.
The interesting fact in the FIDO authentication process is that the server and client exchange no secrets. The main secret information, which is the user’s private key, remains on the device all the time.
How Does FIDO Certification Work?
FIDO has a certification program that determines the compliance and level of security of different services and applications. This is important because it ensures interoperability across different applications and services and also provides important criteria to communicate the level of reliability that each service offers.
Product vendors that become certified by FIDO receive a badge that confirms the integrity and interoperability of their products with FIDO’s specifications. For instance, a FIDO2-certified server will be able to operate with any FIDO2-certified authenticator, even if the two products have been developed by different companies.
FIDO has different certification programs that conform to various levels of involvement in creating authentication servers, applications, and hardware.
The Functional Certification program is an end-to-end process that allows organizations to validate the compatibility and interoperability of their products and services with FIDO specifications. The process involves self-testing tools and verification by FIDO experts. After going through the process and getting their products approved, organizations can file to receive a certified logo, which they can print on their packaging and publish on their websites. Authenticator vendors can also register the metadata of their products on FIDO’s servers to facilitate interoperability with other FIDO-enabled products.
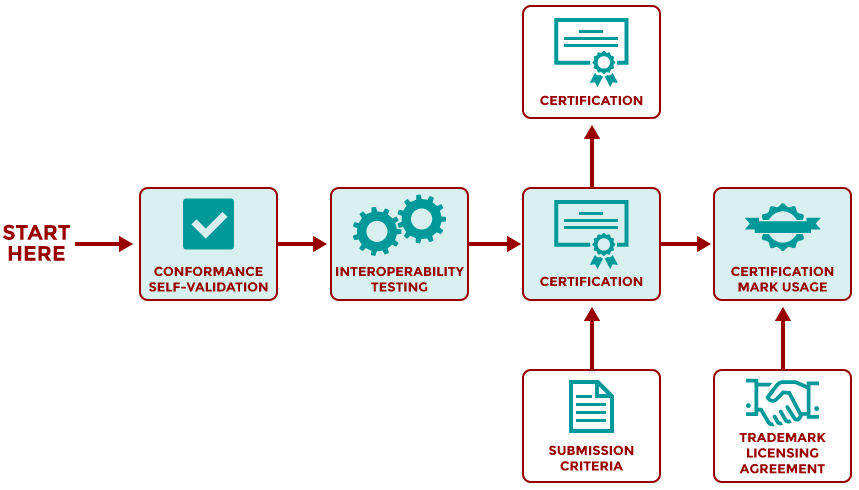
FIDO Authenticator Certification
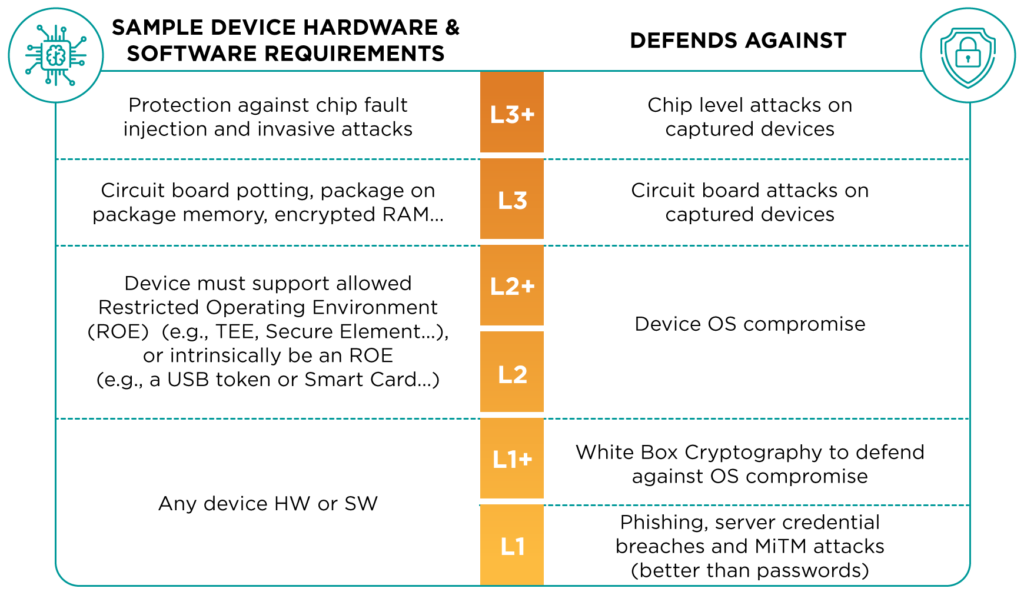
Certified FIDO authenticators are classified on different levels, which specifies their level of security:
- Level 1: This includes all software and hardware authenticators that implement the FIDO2, UAF, or U2F specification. This is the most basic implementation of FIDO authenticator and protects users against phishing, server breaches, and man-in-the-middle (MitM) attacks.
- Level 2: Level 2–certified authenticators must have extra security measures that protect security keys against more advanced attacks. Level 2 authenticators are resilient to malware that might want to extract information by gaining access to the device’s operating system.
- Level 3: Level 3 FIDO authenticators protect the user’s keys against basic hardware attacks. The device should be resistant against physical tampering or at least show clear signs if a hacker manipulates the device’s hardware.
- Level 3+: This is the most secure type of FIDO authenticator. Level 3 authenticators must store their keys in a TPM, preventing any type of physical tampering or data extraction methods.
Biometric Authentication Certification
With biometric authentication becoming a convenient, secure, and affordable option on many devices, vendors are becoming more inclined to offer it to their clients. However, the sensitivities of implementing biometric authentication and handling biometric data have created complexities in the verification of vendors’ products.
FIDO’s biometric authentication certification program is meant to provide a baseline to verify the security and reliability of biometric authentication technologies. FIDO’s Biometric Certification is a requirement for any FIDO authenticator that has a biometric component. But biometric authenticator vendors that don’t apply for a FIDO Authenticator Certification can still have their technology evaluated and certified for FIDO’s Biometric Certification.
Closing thoughts
Since its official launch, the FIDO Alliance has been able to rally some of the biggest names in tech and finance industries to help bring more secure and convenient authentication to the applications users employ every day. Today we’re much closer to a passwordless internet than we have ever been. As the efforts of the Alliance pick up steam, we can hope that passwords might soon become a thing of the past.
See how Secret Double Octopus works with FIDO2