For many organizations, Microsoft’s Active Directory is the meat-and-potatoes of their digital infrastructure. One of the greatest advantages of Active Directory is that it gives organizations a platform to manage everything, including authentication, access to digital assets, applications, administrative functions and possibly anything an employee can do a corporate network.
Among directory services, AD is one of the easiest to deploy and its environment is very much familiar and easy to use for most users. For normal users, the Active Directory experience is no different than logging in to any Windows machine. The rest is taken care of by the AD administrator.
AD is also scalable, making it a suitable option for small organizations with a single facility and a few dozen members as well as large enterprises spanning across hundreds of geographical locations and thousands of employees.
But the same thing that makes Active Directory an attractive option for network administrators can also make it vulnerable to cyber attacks and data breaches.
The weaknesses of plain passwords
For many organizations using Active Directory, the only thing protecting user accounts is a simple password. Yet, as history has shown time and again, plain passwords are not enough to protect user accounts. There are many ways that password-protected systems can become hacked.
Unless a company sets strict password complexity and expiration policies, nothing will prevent users from setting easy-to-guess passwords on their accounts. And hackers can stage brute-force or dictionary attacks to find users’ passwords and get access to their accounts.
Even if a user chooses a complex password, there are still ways that hackers can get access to it. For instance, if the user uses the same password as their AD account in other services, a data breach at any of those companies can enable hackers to access the user’s account.
Also, if the user falls victim to a phishing or spear-phishing scam, not even the most complex password will protect them from hackers.
Another threat is that of man-in-the-middle attacks (MITM). Many organizations open access to their Active Directory services from the internet because their employees log in to their servers from different geographical locations. With enough resources and planning, hackers will be able to intercept users’ passwords when they’re logging in to their account.
Two-factor authentication for Active Directory
In order to enhance the security of user accounts, Active Directory supports two-factor and multi-factor authentication (2FA/MFA). In a nutshell, 2FA requires users to present something in addition to their password when logging in to their account. This prevents password theft from giving hackers access to AD accounts.
Smart cards are devices that users must carry with them and insert into their computers when logging in to their Active Directory accounts. Smart cards generate a unique cryptographic hash every time users log in to their account and send it to the AD server after users enter their account’s password. The cryptographic hash can only be generated by the smart card and can’t be spoofed.
However, smart cards have their own caveats. First, organizations incur additional IT costs for procurement and support of smart cards for their Active Directory users. Also, there’s very limited support for smart cards on mobile devices. For their part, users must make sure that their smart cards don’t get lost or stolen.
Software tokens come in different flavors, but the general idea is that, in addition to their password, every time users log in to their Active Directory account they have to enter a verification code. The verification code, which is constantly changing, is sent to a device that is associated with the account, usually a mobile phone.
The advantage of software tokens is their low costs. Organizations don’t need to purchase additional hardware and can use whatever mobile device their users have as their Active Directory 2FA device. However, from the user’s perspective, software 2FA is more difficult to use and the additional step it adds to the authentication process isn’t very intuitive. Moreover, from a security perspective, depending on their implementation, software tokens can be compromised. For instance, if verification codes are sent as an SMS message to the user’s phone, hackers will be able to forward the user’s text messages to another number and receive a copy of the verification code at the same time. Other types of 2FA that send the code to the mobile device can become the target of MITM attacks.
Secret Double Octopus 2FA for Active Directory
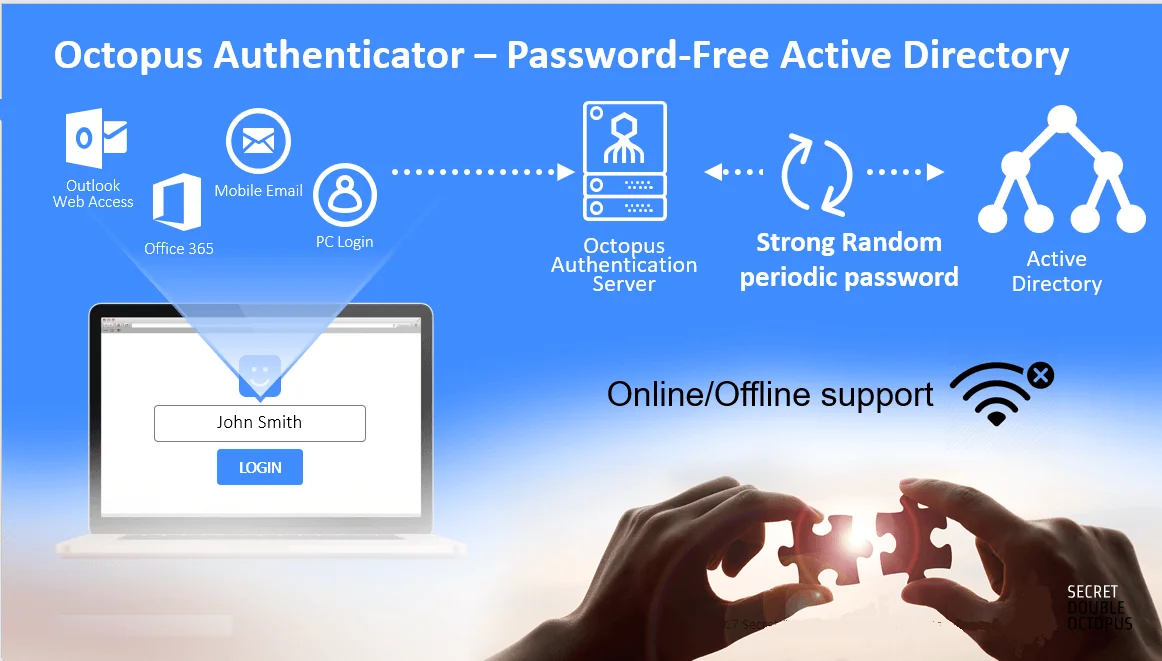
Secret Double Octopus provides a unique authentication solution that minimizes the costs, provides optimal user experience and maximizes security for organizations that want to set up two-factor authentication for Active Directory.
Secret Double Octopus is a password-less authentication technology, which means integrating it with Active Directory will remove the biggest weakness of user account protection, which is the sharing and storage of secrets.
Moreover, Secret Double Octopus provides superior MFA for Active Directory (AD) replacing the need for passwords altogether, using a proprietary mobile app, the Authenticator, for 2FA, which means it doesn’t require organizations to spend extra funds on acquiring new hardware. Meanwhile, the technology remedies the failures of other software 2FA solutions by using a unique multi-channel authentication mechanism that makes MITM attacks virtually impossible. The minimum interaction required by the verified party leads to a better user experience: Instead of typing in verification codes, they receive an access request on their mobile device every time they log in to their Active Directory account, and they only need to tap it to approve it.
Long story short, Secret Double Octopus brings together the best features of different 2FA mechanisms for Active Directory, satisfying users, IT and security teams.