In the realm on protecting digital information, a man-in-the-middle (MITM) attack is one of the worst things that can happen to an individual or organization. MITM attacks happen when an unauthorized actor manages to intercept and decipher communications between two parties and monitors or manipulates the exchanged information for malicious purposes. And while the term has been a staple in cybersecurity circles, new and sophisticated versions are continuously appearing, able to hurt the heart of corporate IT systems.
For instance, hackers can stage MITM attacks to steal sensitive data, such as account credentials or credit card information, or they can use them to deliver malware-inflicted files and applications while posing as legitimate sources.
During an MITM attack, each of the legitimate parties, say Alice and Bob, think they are communicating with each other. But in reality, their exchanges are going through Eve, the eavesdropper, who stands between them, posing as Alice to Bob and as Bob to Alice. Eve can decide to change the information before passing it on from Alice to Bob, or she can just sit there and silently record their exchanges for future use.
Man-in-the-middle attacks come in different forms. Conceptually, they’re similar, but technically, they’re different and they leverage various vulnerabilities in security practices. Here’s a breakdown of different types of MITM attacks and how you can protect yourself against them.
IP spoofing
Every computer in a network is identified with an internet protocol (IP) address, which it uses to communicate with other devices on the same network. IP addresses come in different forms, the more common form, known as IPv4, gives each computer a 32bit identifier (e.g. 192.168.34.12).
On some networks, security of digital assets and applications is maintained by specifying which IP addresses can access which resources. An IP spoofing attack happens when a malicious actor masks their identity by presenting themselves with the IP address of a legitimate device to gain access to resources that would otherwise be beyond their reach.
For instance, access to a server might be limited to a specific set or range of IP addresses. A hacker manipulates its network packets so that the sender’s address reads as that of a legitimate computer. By doing this, the attacker tricks the server into thinking the packets are coming from an authorized device.
Hackers use IP spoofing in a number of different ways, including staging DDoS attacks, in which attackers drain the resources of a server by flooding it with bogus network traffic. IP spoofing can also be used in man-in-the-middle attacks. In this case, the attacker stands in between two communicating parties, spoofing each of their addresses to the other. This way, each of the victims sends their network packets to the attacker instead of directly sending it to its real destination.
The biggest defense against MITM attacks conducted through IP spoofing is to use encrypted communications. When the information between two parties is encrypted with a key that only they hold, it will make sure that even if a malicious party manages to intercept the traffic, they won’t be able to read or manipulate its contents. Authenticating user identities also prevents hackers from gaining unauthorized access to network resources by simply spoofing their IP address.
Read about the “Security Benefits of Passwordless”
Download Whitepaper

DNS spoofing
Domain name system (DNS) is the technology that translates domain names (e.g. doubleoctopus.com) to the IP address of the server it corresponds to. DNS is one of the most important infrastructural protocols of the internet and it is meant, among other purposes, to ease communications and stop people from needing to memorizing the IP address of every server they communicate with. When you type in the address of a domain in your browser, a name resolution request is sent to a DNS server, which then looks up the domain name in its directory and returns the IP address of the corresponding server.
DNS spoofing is a type of attack in which a malicious actor intercepts DNS request and returns the address that leads to its own server instead of the real address. Hackers can use DNS spoofing to launch a man-in-the-middle attack and direct the victim to a bogus site that looks like the real one, or they can simply relay the traffic to the real website and silently steal the information.
For instance, a victim wants to visit a banking website (https://choicebank.com). The attacker intercepts the victim’s browser request and instead of returning the IP address of the real Choice Bank web server, he returns the IP address of a malicious web server. The server will serve a login page that looks similar to that of the authentica website, but as soon as the victims types in their username and password, the information will be sent to the servers of the attacker.
Detecting and blocking DNS spoofing is an intricate process. There are several measures that can protect you from MITM attacks through DNS spoofing.
DNS spoofing requires the attacker to have access to your local network, so the first and most important measure is to set up a good perimeter security and prevent unauthorized access to your local network. If you’re using WiFi at your organization, you can setup WPA-enterprise security, which requires every connecting user to have a username and password instead of giving a global password for the entire network.
Another protection against DNS spoofing is the use of encrypted communications. Malicious actors can easily spoof unencrypted websites. But on HTTPS communications, it is very difficult, because even though malicious actors might stage a DNS spoofing attack on the website, they won’t be able to spoof the certificate, the digital document that verifies the encryption keys of the website. So a user who has been the target of DNS spoofing on an encrypted website will see a warning in their browser, telling them that the certificate of the website they’re visiting can’t be verified. That’s the telltale sign of a MITM attack.
But as we’ll see in the next section, even HTTPS websites can become the target of MITM attacks.
HTTPS spoofing
Basically, HTTPS websites can’t be spoofed. But that doesn’t mean hackers can’t create websites whose domains look very similar to that of the targeted website. HTTPS spoofing, also known as homograph attacks, replace characters in the targeted site’s domain with other non-ASCII characters that are very similar in appearance. The attack exploits a feature called Punycode, a standard that enables the registration of hostnames that contain non-ASCII characters.
To stage homographic attacks, hackers register a domain name that is similar to the target website, and they also register its SSL certificate to make it look legitimate and secure. Then they send a link to their intended victim. Since most browsers support the display of punycode hostnames in their address bar, when the user browses to the address, they won’t notice that it is a bogus version of the site they expect to visit. Their browser even shows that the website’s certificate is legitimate and secure, further making it difficult to detect the attack.
From there, while the user thinks they are interacting with a legitimate encrypted website, they have in fact fallen victim to a man-in-the-middle attack and are giving away their information to a malicious actor. Security researcher Xudong Zheng showed a proof-of-concept of this attack last year, in which he spoofed the HTTPS website of apple.com.
One of the ways to prevent HTTPS spoofing is to disable punycode display support in your browser. This will make sure that the real, encoded domain name in the address bar and warn you if you’re visiting a non-authentic website. For instance, when you visit the address in the proof-of-concept mentioned above, you’ll “see https://www.xn--80ak6aa92e.com” in your address bar instead of seeing “apple” with a Cyrillic “a.”
Another protection against homographic attacks is to use a password manager. Password managers will automatically fill in the username and address boxes of websites when you’re visiting the legitimate domain. They’re not fooled by the looks of punycode representations.
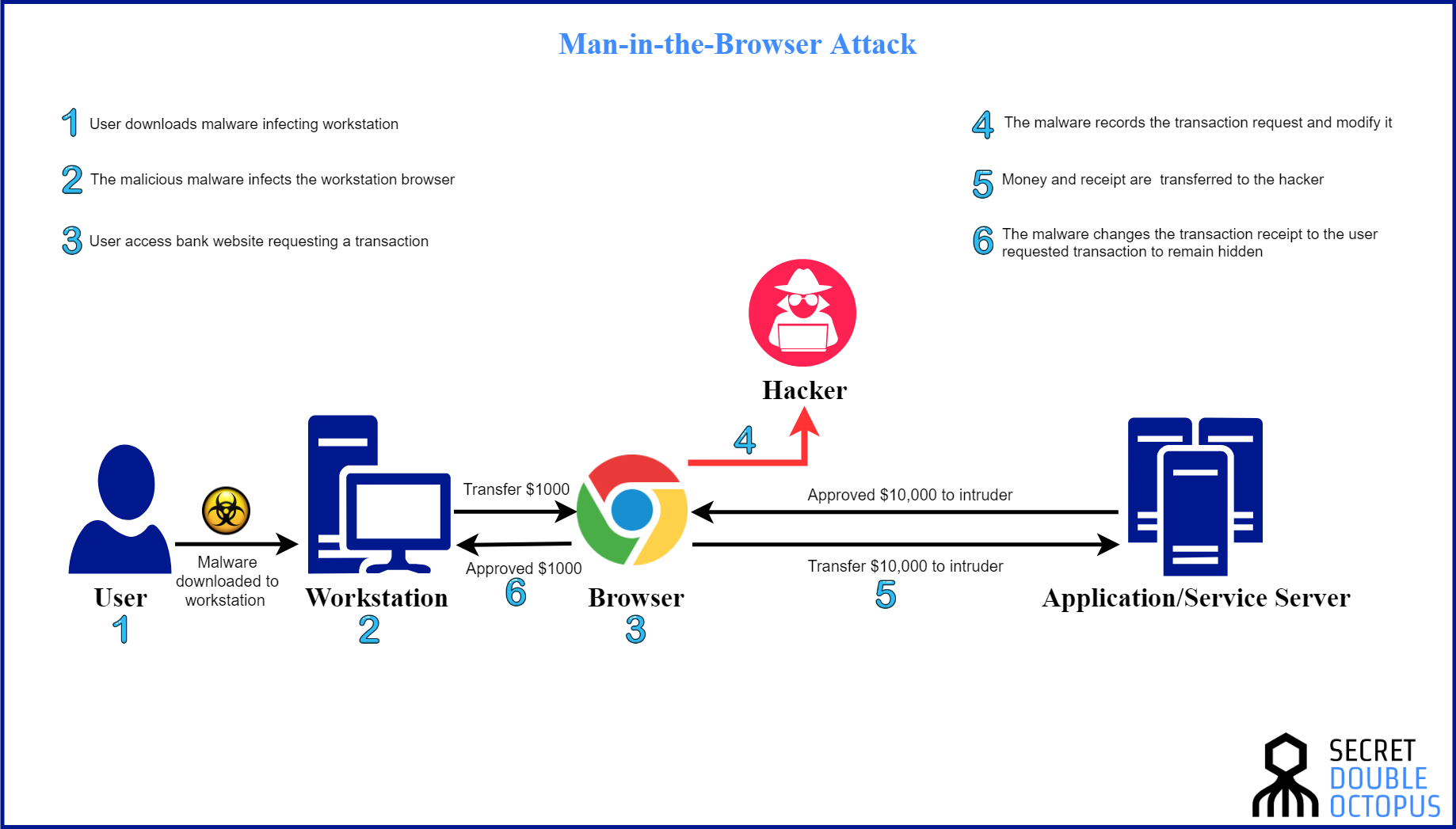
Man in the Browser (MITB)
Man-in-the-browser is a form of man-in-the-middle attack where an attacker is able to insert himself into the communications channel between two trusting parties by compromising a Web browser used by one of the parties, for the purpose of eavesdropping, data theft and/or session tampering.
Man-in-the-browser is often used by attackers to carry out various forms of financial fraud, typically by manipulating Internet Banking Services.
In order to compromise the browser, adversaries can take advantage of security vulnerabilities and/or manipulate inherent browser functionality to change content, modify behavior, and intercept information. Various forms of malware, most typically malware referred to as a Trojan horse, can be used to carry out the attack.
SSL stripping
Another form of man-in-the-middle attack happens when a hacker manages to stage an SSL stripping scheme against the victim. As we mentioned previously, hackers can’t break into legitimate HTTPS traffic between a client and a server even if they manage to intercept and relay the communications.
In the case of SSL stripping, the attackers downgrade the communications between the client and server into unencrypted format to be able to stage a MITM attack.
When a victim wants to connect to a server, the attacker intercepts the request and creates an independent, legitimate connection to the server through HTTPS protocol. When attackers receive the server’s response, they relay it to the victim in unencrypted format, posing as the server. Thinking they’re communicating with the legitimate party, the victim will continue to send information to the attacker, who will then relay it to the server in HTTPS.
To give an example, say the banking website mentioned earlier receives several complaints of man-in-the-middle attacks and hijacked accounts and decides to roll out a secure version of its website (https://choicebank.com). A hacker monitoring a potential victim sees the target trying to visit the HTTPS version of website and intercepts the request. From there the attacker sends a request to the login page of the website and returns the unencrypted response to the victim. When the victim types in their username and password and clicks the login button, the hacker steals the login information before sending it to the server.
Wary users will notice that they’ve been targeted by an SSL stripping attack if they look in their browser’s address bar and see that they’re connected through the unencrypted HTTP protocol. You can also install HTTPS Everywhere, a browser extension that enforces HTTPS communication wherever possible. HTTPS Everywhere will prevent an uninvited party from downgrading your communications to HTTP.
Another measure to protect against SSL stripping is to make sure your local network is secure and unauthorized parties don’t have access to it. SSL hijacking requires access to your local network. At the corporate level, setting up strong firewalls will also prevent outside parties from gaining access to your local network and moving laterally to stage MITM attacks.
Email hijacking
Email hijacking is another form of man-in-the-middle attack, in which the hacker compromises and gains access to a target’s email account. The attacker then silently monitors the communications between the client and the provider and uses the information for malicious purposes.
For instance, at an opportune moment, the attacker might send a message from the victim’s account to their bank and instruct them to transfer funds to the attacker’s bank account. They might also use the email to take over other online accounts tied to the email account.
Email hijacking is usually staged through phishing and other social engineering scams. Attackers deceive victims into revealing their credentials by directing them to bogus login pages or tricking them into installing a keylogger malware, which records the victim’s keystrokes and sends it to a remote server that the attacker owns.
In 2016, hackers managed to hijack the email account of John Podesta, the chairman of the campaign of U.S. presidential nominee Hillary Clinton, through a phishing attack. From there, the hackers stole and leaked thousands of emails, which many believe dealt a huge blow to Clinton’s campaign.
While there are many guidelines and practices that can reduce the risk of phishing and email hijacking, the best way to prevent a malicious actor from taking over your email accounts is to strengthen your authentication. One solution is to use two-factor authentication, which requires users to have a secondary token (such as a mobile device or a physical key) in addition to the password when signing into the account. An even stronger solution is the use of passwordless authentication technologies, which totally obliviate the need for passwords and make it impossible for hackers to gain access to accounts through phishing.
Wi-Fi eavesdropping
Also known as an “evil twin” attack, hackers perform Wi-Fi eavesdropping is a type of man-in-the-middle attack that tricks unsuspecting victims into connecting to a malicious Wi-Fi network. To perform Wi-Fi eavesdropping, a hacker sets up a Wi-Fi hotspot near a location where people usually connect to a public Wi-Fi network. This can be a hotel, a restaurant or your local Starbucks. The hacker then names the hotspot after the actual public network that people use in that location (thus the name “evil twin”).
Since people usually set their devices to remember and automatically reconnect to known Wi-Fi networks, as soon as they come in the vicinity of the malicious hotspot, they automatically connect to it. The user will then think they have been connected to the legitimate network.
Since they are acting as the gatekeeper to the internet, the attackers can now perform a number of man-in-the-middle techniques. For instance, they can perform SSL stripping attacks to force users to go through the unencrypted versions of their favorite websites, or they can stage DNS hijacking to redirect users to bogus versions of the websites they’re trying to connect to.
For instance, say a victim usually uses the Wi-Fi network of a Starbucks where she eats breakfast. A hacker who wants to stage a man-in-the-middle attack on the victim goes to the same Starbucks and picks up the ID and password of its Wi-Fi network. Then, the attacker sets up his own Wi-Fi network with the same name and password using a router or a laptop computer. Now, devices of users who have previously connected to the Starbucks network (including the victim) will automatically connect to the evil twin when they come within its network range. The attacker can then use the connection to stage man-in-the-middle attacks.
Because of this and other threats, public Wi-Fi networks are considered extremely unsafe, and most security experts will recommend not using them for any sensitive task such as banking or connecting to social media accounts. However, if you absolutely have to use a public Wi-Fi network, there are a couple of things you can do to make sure you don’t fall victim to Wi-Fi eavesdropping.
One of the most important measures is to disable automatic Wi-Fi connections and make sure you manually select which networks you want to use. It will be a little less convenient, but at least you’ll have a greater chance of avoiding evil twins and MITM attacks.
Another very important protective measure to prevent MITM through Wi-Fi eavesdropping is to use a virtual private network (VPN). VPNs create a secure channel for all your internet traffic, encrypting everything and sending them through an intermediate server. When using a VPN, even if a hacker manages to intercept your communications, all they will see is a stream of encrypted data, and they won’t be able to make sense of it. They won’t even be able to figure out which sites you’re browsing to, so they won’t be able to redirect you to their own malicious copies of the websites.
Session hijacking
Session hijacking, also known as cookie side-jacking, is another form of man-in-the-middle attack that will give a hacker full access to an online account. When you sign into an online account such as Facebook or Twitter, the application returns a “session cookie,” a piece of data that identifies the user to the server and gives them access to their account. As long as the user’s device holds on to that session token, the server will enable them to use the application.
When a user signs out of an application, the server invalidates the session token and all further access to the account requires the user to re enter their login credentials.
In a session hijacking attack, the hacker steals the user’s session token and uses it to access the user’s account. There are several ways that an attacker can stage a session hijacking attack, such as inflicting the user’s device with a malware that monitors and steals session data. Another method is the use of cross-site scripting attacks, in which an attacker uploads a programming script into a webpage that the user frequently visits and forces the user’s computer to send the session cookie data to the server. Other methods of session hijacking leverage flaws in the application’s programming to guess or reveal session cookie information.
Protection against session hijacking mostly lays on the shoulders of app developers, who will have to make sure their programming practices are secure. Users can protect themselves against hijacking attacks by using encrypted communications (via HTTPS and VPN). They can also minimize the attacks of potential session hijacking attacks by frequently signing out of their accounts to invalidate their session cookies.