While Okta FastPass removes passwords from Okta SSO-compatible apps, it falls short of delivering enterprise-wide passwordless access. This article explores the limitations of the Okta Fastpass approach and how you can protect your Okta investments and eliminate passwords across all IT-managed applications, boosting security and user experience.
What You Will Learn
- What is Okta FastPass?
- What it means to be passwordless
- Why Okta FastPass delivers only partial passwordless coverage
- How to extend the benefits of passwordless authentication enterprise-wide
What is Okta FastPass?
FastPass works with the Okta Verify app to create secure passwordless authentication to apps managed by Okta SSO across supported applications. Users enroll on the Okta Verify app of their device via inline enrollment, using their mobile device to scan a QR code, or if they’re enrolling for the first time from a desktop, using email links, SMS, or if necessary, passwords.
Okta Verify then generates a public/private key pair and sends the public key and metadata to an Okta server. The private key never leaves the device’s Trusted Platform Module (TPM).
This cryptographic pairing achieves “proof of possession” used to verify identity. FastPass also leverages biometrics to reinforce identity verification and support SSO workflows.

Why passwordless authentication?
Security industry analysts, vendors, and regulators across most industries all agree that getting rid of passwords pays big dividends by:
- Achieving phishing resistance
- Upleveling user experience (UX)
- Promoting compliance with best-practice security guidelines published by MITRE, NIST, CISA, and cyber-insurance carriers to chart a path to Zero Trust security maturity
Passwordless authentication takes away hackers’ favorite go-to tool – working employee credentials that unlock access to devices, applications, and data residing on-prem or in the cloud.
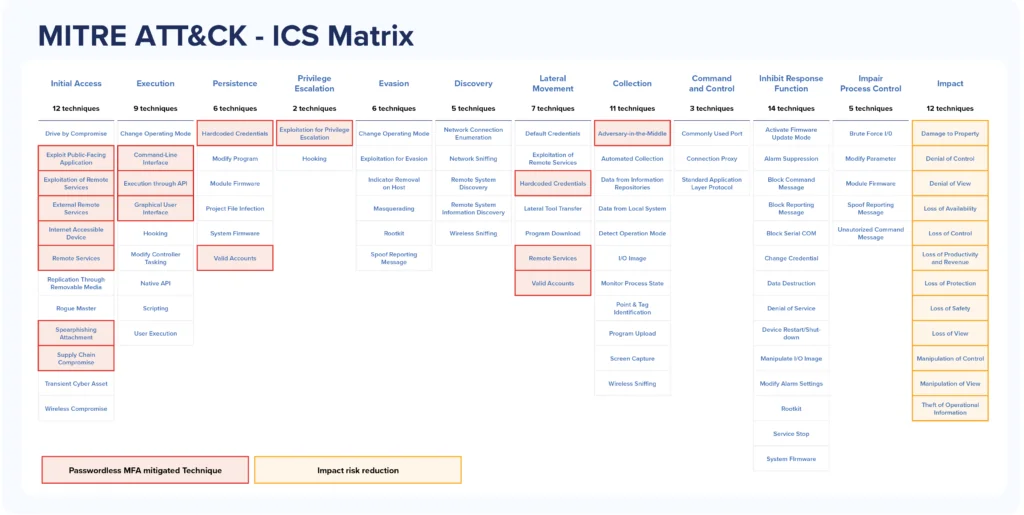
MITRE ATT&CK is the go-to toolkit for modeling the business’s threat exposure. In a single sweep, enterprise-wide passwordless mitigates many attacker techniques. In the ATT&CK Matrix for ICS analysis below, the red boxes highlight the techniques mitigated by passwordless MFA.
What are the limitations of Okta FastPass?
Okta FastPass only works with enterprise apps and services that are compatible with Okta SSO, which are primarily SaaS web apps, typically productivity tools like O365, Jira, SFDC, and HR management platforms like Workday. Obviously, enterprises run on much more than just SaaS apps.
Unfortunately, essential line-of-business on-prem apps, remote access, and legacy password-based systems are left behind by FastPass. As a result of these incompatibilities, workers must continue to remember and type their directory passwords throughout the workday.
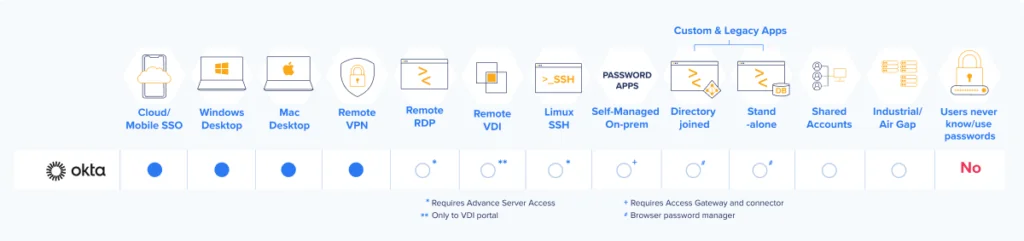
If Okta FastPass only works with SSO, is it passwordless?
The short answer is: no. FastPass gives users a passwordless login experience with Okta SSO-supported apps, but from a user perspective, that does not make the worker passwordless since they continue to use Universal Directory passwords to access other apps.
Another area in which Okta’s passwordless capabilities prove limited is fallback when users’ authenticators (usually a phone with Okta Verify or a FIDO token) is missing or broken. Businesses need to ensure availability for these situations so Okta IAM admins leave password-based login active. Users can use passwords to log in or FastPass, e.g., leaving “PasswordProvider” set in the Windows Credential Provider controls.
In other words, users still have to know their directory passwords so the risks inherent in using passwords persist. Attackers can also log in to these same services by exploiting vulnerable passwords.
Okta isn’t the only partial passwordless solution. Solutions from other leading IAM vendors like Microsoft and Ping include similar limitations.

What does it mean to be passwordless?
To achieve zero-trust security and UX goals, passwordless needs to mean no passwords for every worker across the whole enterprise. We use this simple test to define passwordless: Does the user know and use their directory password?
Partial passwordless coverage does not make your enterprise passwordless
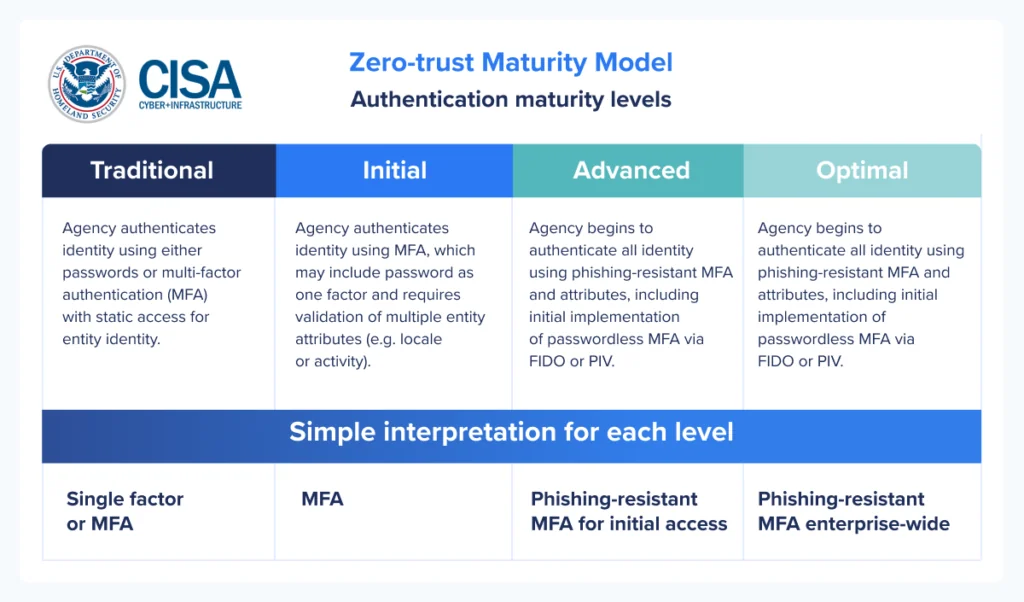
If any workers need to create, remember, enter, or reset passwords to access company resources—ever—you aren’t passwordless, and your enterprise isn’t phishing-resistant and in compliance with important standards like the CISA Zero-trust Maturity Model guidance on authentication where “optimal” is the user phishing-resistant MFA methods on every access enterprise-wide:
Technically speaking — and regulators and insurance companies have been known to get technical — IT can’t check the box for Zero Trust or even passwordless. Worse yet, partial passwordless authentication leaves organizations at partial at risk of falling victim to phishing/vishing/quishing attacks, credential compromise, account takeover (ATO), and the ransomware and data theft that often follow. All the things you need MFA and SSO to prevent.
If any workers need to create, remember, enter, or reset passwords to access company resources—ever—you aren’t passwordless, and your enterprise isn’t phishing-resistant and in compliance with important standards like the CISA Zero-trust Maturity Model guidance on authentication where “optimal” is the user phishing-resistant MFA methods on every access enterprise-wide.

Is it possible to extend Okta passwordless coverage beyond SSO?
So, while popular office productivity apps like Office 365, Salesforce.com, and Workday convert easily to Okta FastPass, another 50% or so do not (e.g., on-prem and legacy apps). Leaving these heavily targeted assets exposed is a bit like locking all the doors in the building but leaving the windows wide open.
To convert these applications to comply and work with Okta FastPass involves significant skills and retooling, which begs the question:
“Whose job is that?”
In a word: yours. The heavy lifting needed to modernize an identity infrastructure to meet Okta’s technological requirements usually falls to the enterprise IT team or a third-party solution provider. Even with tools from Okta like Access Gateway and Server Access, the conversion process involves a steep, ongoing development effort and cost.
The scope of the project might include replacing entire systems, reconfiguring directories, and recoding apps to work with Okta’s identity provider (IDP). Or, companies might use client-side authentication based on certificates. Either way, rollouts of MFA or SSO usually unfold on an application-by-application basis with each one taking 3-5 weeks or longer.
Real-world Challenges of Updating Apps
Here are two IT leaders recounting their challenges. Perhaps you are in the same situation and need less disruptive options:
Automotive Manufacturer
An automotive IT leader discussed the challenges of upgrading more than two thousand applications accumulated from decades of M&As and through organic growth in building their one-of-a-kind business. A dedicated development team sets aside an average of five days per app for SSO compatibility updates. Five days sounds fast, but at that rate, it will be 40 years before all the apps are SSO-compatible. In other words, it will never happen since the world will be different in 40 years.
Insurance industry
In another conversation, an insurance IT leader talked about how they spent the last few years converting their apps to Okta SSO. At this point, they have successfully converted one-third of all the apps, a big accomplishment. The next two-thirds will likely be more challenging to convert and will take longer than 2x the last few years.
‘Okta + Octopus’ delivers 100% passwordless workforce coverage
The passwordless MFA platform from Secret Double Octopus (SDO) achieves 100% passwordless MFA coverage by working in conjunction with Okta Verify or the Octopus app. SDO fills the use case coverage gaps left by these solutions to extend investments in Okta enterprise-wide.
You’ll achieve passwordless authentication for your entire workforce quickly, making the day-to-day lives of users and IT easier without disrupting systems.

Octopus works for — and with — any workforce application
The Octopus platform delivers 100% coverage across Windows, Linux, Mac, custom, and legacy or password-centric applications by:
- Replacing directory password fields with machine-generated ephemeral tokens that users don’t know exist
- Separating user login from backend directory management
We’re uniquely able to do this — faster and more completely than any other provider — because of our fundamentally different and more secure approach. The Octopus Authentication Platform uses a patented technique we call Invisible Secret Rotation that replaces Okta Universal Directory password entries with Octopus-managed tokens.
Workers authenticate and prove their identities to Octopus using stronger passwordless mechanisms, including Okta Verify with biometrics, FIDO2 tokens, or X.509 smartcards. The platform then acts as a passwordless IDP to orchestrate access to user desktops.
Okta customers can continue to use FastPass, Okta Verify, and Okta Universal Directory native capabilities while achieving high-assurance (AAL3-compliant) passwordless coverage for every IT-managed application or service.
Octopus with Okta Verify UX demos
Here are three demo videos to show you the Octopus passwordless user experience with Okta Verify and Okta Universal Directory (click each icon):
Enterprise-wide passwordless pays big dividends
A passwordless login slashes the attack surface and makes businesses more compliant with Zero Trust identity standards — a big plus during audits and cyber insurance renewals. Combining Okta and the Octopus platform to create a full solution creates a powerful force-multiplier:
- Users stop spending up to 5% of their day logging in and out of apps and services
- IT avoids the 40% of all Help Desk calls that involve credentials – and the exorbitant future effort to convert apps to IAM and MFA solutions based on FIDO or public key infrastructure (PKI) technology
- Companies achieve high-assurance, AAL3-compliant authentication enterprise-wide that finally stops the phishing
Calculate your ROI potential for enterprise-wide passwordless with the Octopus ROI calculator.

Learn more about the winning combination.
For more insight on how Okta + Octopus = 100% passwordless coverage, check out the ebook, Okta Didn’t Make You Passwordless. Now What? Or schedule a demo with one of our passwordless experts.
Key takeaways
- Passwordless slashes the attack surface, delights the workforce, and pays quantifiable business dividends once you completely eliminate them.
- Okta FastPass works with SSO, but enterprises are so much more than web apps supported on SSO.
- By adding Octopus to your Okta investments, users get the same Okta experience but are now passwordless enterprise-wide.
Related Resouces