Presidential mandate M-22-09 required US government agencies and their suppliers to adopt “phishing resistant” multi-factor authentication (MFA) by 2024, but didn’t say how to go about it. Many regulators and security best practices followed suit, echoing the sentient but failing to define an approach.
CISA strongly urges all organizations to implement phishing-resistant MFA as part of applying Zero Trust principles. While any form of MFA is better than no MFA and will reduce an organization’s attack surface, phishing-resistant MFA is thegold standard and organizations should make migrating to it a high priority effort. CISA
Unfortunately, widespread adoption of MFA has clearly failed to stop phishing and even represents a potential new attack vector.
What you’ll learn
With mandates in place and attacks growing smarter, this timely update on phishing resistant MFA attempts to answer the key questions:
- What is phishing resistant MFA?
- Why most MFA doesn’t make you phishing resistant
- How you can build phishing resistant MFA
- Does phishing resistant have to mean ‘passwordless’?
What is phishing resistant MFA?
As the term itself implies, phishing resistant MFA aims to prevent phishing — scams that deceive workers into revealing their passwords or other sensitive information, or installing malware. Year after year, phishing leads to credential abuse, or the use of legitimate username/password combinations for nefarious purposes, and to account takeover, data breaches, and other serious threats.
MFA’s job is to stop phishing—and it hasn’t worked
Initial attack vectors and root causes
For the 2nd year in a row, phishing and stolen or compromised credentials were the 2 most prevalent attack vectors.
Companies implement multifactor authentication or ‘MFA’ to strengthen security by verifying users’ identity before granting access to company resources. Traditional MFA typically starts with entering passwords as the first step in identity verification and progresses to one or more additional steps like entering one-time passwords (OTPs) sent via text.
Organizations spend millions of dollars to roll out MFA and to train users to spot phishing attempts, yet compromised credentials still play a role in 80% of security breaches. According to the 2024 IBM Cost of a Data Breach Report, phishing still ranks among the top initial vectors for successful attacks. Phishing remains a go-to threat vector because it still works, and generative AI tools like ChatGPT make them harder than ever to detect.
[Check out the blog, How to Avoid MFA Fatigue Attacks.]Why can’t most MFA make you phishing-resistant?
MFA also remains vulnerable to “man in the middle” (MITM) schemes in which adversaries trick users into entering credentials, keys, and one-time passwords (OTPs) into fake login pages. Once they capture this sensitive data—the digital ‘keys to your kingdom’ — imposters use it to access legitimate sites without arousing suspicion. Modern ‘MFA Fatigue’ attacks even leverage users’ frustration with having too many login workflows—too many different MFA steps and processes—to perpetrate attacks.
At the end of the day, for all the friction it causes with users, traditional MFA does not make us phishing resistant because traditional MFA starts with passwords. Secret Double Octopus (SDO), Microsoft and other leading cybersecurity innovators support a critical strategy for strengthening MFA, SSO, and user authentication in general: getting rid of user passwords.

Prior to the rise of ‘work from everywhere,’ Cybersecurity Ventures projected annual spending on security awareness training would reach
$10B by 2027.
That prediction may prove conservative due to the rise of remote work and AI-led social engineering attacks.
Passwordless authentication enables phishing resistance
Federal mandates that prescribe phishing resistance don’t always spell out or specify passwordless authentication but most identity and access management (IAM) experts agree getting rid of user passwords plays a critical role. The question is ‘how,’ but let’s back up a step.
What’s wrong with passwords?
Passwords managed by users verify identity by using something users know — the supposedly secret password that can be exposed, lost, shared, stolen, published, and purchased by threat actors—and used to unlock the company assets. Poor password hygiene, like using the same ones for multiple resources or choosing easy to guess combinations adds to the risk of user credentials falling prey to social engineering. The fact remains:
Any login workflow that still begins with or relies on passwords has the potential to be targeted in phishing attacks.
Eliminate passwords to make MFA phishing-resistant
Passwordless authentication takes “what users know” out of the equation and eliminates the bait used in most phishing attacks, user credentials. A passwordless approach simply eliminates the most vulnerable element of the traditional login process before it gets hijacked by would-be attackers.
How passwordless MFA works
Instead of piling additional steps on top of entering passwords, a passwordless MFA approach replaces secrets with multiple, more reliable identity verification methods. That often means requiring workers to demonstrate possession of the registered smartphone, smart card, or physical token – something users have instead of something they know – and biometric proof through voice recognition, thumbprint, or facial scanning.
Two options for implementing passwordless
After the Office of Management and Budget (OMB) memorandum 22-09 debuted in the US, CISA published its Implementing Phishing-Resistant MFA guidelines specifying two options for implementing phishing-resistant MFA:
- FIDO/WebAuthn authentication
- Public key infrastructure (PKI)-based
While the guidelines don’t use the exact words, FIDO and PKI inherently enable and leverage passwordless authentication to bolster security.

The pros and cons of FIDO authentication
Based on specifications developed by the FIDO Alliance, a consortium of industry-leading security and IT vendors, FIDO-based authentication found rapid traction among leading browsers, mobile devices, and OSs. Instead of, or along with passwords, the WebAuthn protocol defined within the FIDO2 standard use physical tokens, biometrics, and/or PINs to verify user identity and complete authentication.
Solutions like Windows Hello for Business (WHfB) and Okta FastPass typically use FIDO technology and single sign-on (SSO) to achieve passwordless authentication that does away with phishable credentials. Popular FIDO-based approaches prove relatively easy to implement but all have one major drawback: they only work with FIDO-enabled SaaS applications and services—a fraction of the overall use cases for MFA.
The pros and cons of PKI
Public key infrastructure, or ‘PKI’ defines processes for using cryptographic public keys and digital certificates to encrypt digital communications and authenticate those seeking access. Also commonly known as X.509 certificates, PKI uses a pair of public and private passkeys to pin and authenticate communications between user devices and servers via browsers and between other systems within an organization.
PKI offers broader use case coverage than FIDO but can be exponentially harder and more costly to implement. Rolling out passwordless authentication and phishing-resistant MFA based on PKI usually means significant rearchitecting of applications and existing identity infrastructures.
At a minimum, PKI requires:
- A certificate authority (CA), a trusted entity that issues, stores, and signs digital certificates with private keys and then publishes the public keys that get accessed by users upon request
- A registration authority (RA) that verifies the identity of users requesting the digital certificates
- Certificate databases and management systems used to validate and deliver certificates
- Central directories that manage and store cryptographic keys
Converting every in your enterprise to “speak” PKI can take up to a year — to get the first app up and running — and weeks or months to onboard every subsequent app or service. Companies facing mandates to implement phishing-resistant MFA, and those just looking to stop phishing and protect users and data, don’t have that kind of time.
PKI also costs a lot. Aside from being built into $100 smart cards with embedded signed certificates (used mainly within the government), client-side X.509 PKI has yet to be widely adopted.
Passwordless authentication benefits go beyond phishing resistance
Passwordless MFA also reduces user friction by making logins simpler. And, by SDO’s calculations, passwordless MFA saves the average enterprise up to $2M per year on Help Desk calls and lost productivity alone. In other words, not including the money you save by avoiding data breaches and protecting your organization’s reputation.

Partial passwordless solutions miss the mark for phishing resistance
100% passwordless coverage includes:
• Windows, Mac, Linux
• Legacy and custom apps
• Network services
• Apps/data housed on-prem
• Air gaps in manufacturing environments
• Shared accounts
All MFA and SSO workflows need to be phishing-resistant—for every user, location, app, service, and device—before you check that box.
Unfortunately, WHfB, Okta FastPass, and other offering only eliminate passwords from Windows login and SSO-compatible apps. User still user their directory passwords for everything else. Only the Octopus Passwordless Authentication platform works with everything in the enterprise, including with password-base apps and network services. A complete, qualifying phishing-resistant MFA must:
- Take passwords out of the user authentication process for every user and application – zero passwords, 100% use case coverage
- Be compatible with all authenticators, SSO services, and directories out of the box – zero passwords with zero change
- Disrupt modern man-in-the-middle (MITM) attacks
- Support FIDO2 today
Is phishing resistant MFA essential for Zero Trust?
The simple answer is yes. The CISA Zero-trust Maturity Model (and other nations’ zero-trust security frameworks) call out phishing-resistant MFA as a requirement. In its ‘optimal’ category, the CISA model calls for increasing use of phishing-resistant MFA beginning with initial authentication granting and then growing to cover subsequent logins and prevent lateral movement.
Practically speaking, eliminating passwords completely from the user experience goes a long way toward satisfying the intent of Zero Trust strategies (and mandates) for becoming phishing-resistant.
| Function | Traditional | Advance | Optimal |
| Authentication | Agency authenticates identity using MFA, which may include passwords as one factor and requires validation of multiple entity attributes (e.g., locale or activity). | Agency begins to authenticate all identity using phishing-resistant MFA and attributes, including initial implementation of passwordless MFA via FIDO or PIV. | Agency continuously validates identity with phishing-resistant MFA, not just when access is initially granted. |
Octopus passwordless authentication adds a more practical option
Phishing resistance derives from pre-pinning user devices or identities to destination sites or applications to validate identity and establish trust. The SDO approach accomplishes this while overcoming the drawbacks of FIDO – incomplete use case coverage—and PKI; namely, high cost and lengthy, complex technical upgrades and implementations.
SDO uses FIDO and Octopus mobile push desktop-to-app signed pinning to enable phishing-resistant passwordless MFA today, with password directories or FIDO servers on the back end. The Octopus platform decouples user login workflows and backend identity infrastructures and replaces vulnerable passwords with ephemeral tokens users never know exist.
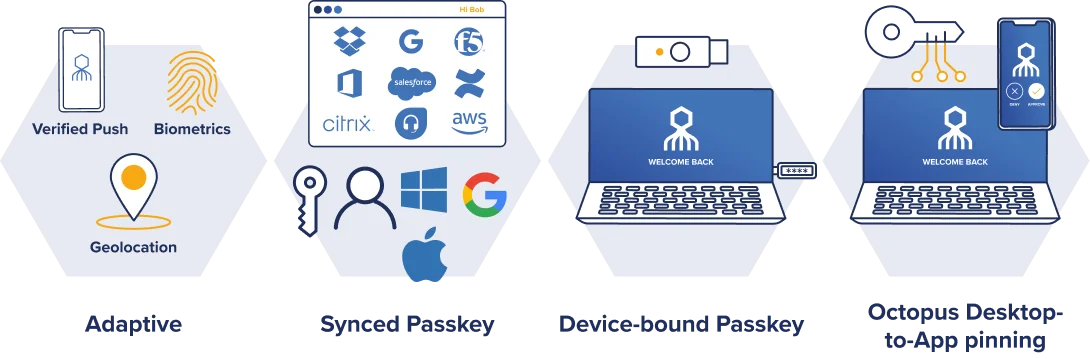
The Octopus catches more phish
Octopus extends phishing-resistant, passwordless MFA compatibility to every enterprise application out of the box, providing full support for FIDO and a practical path to a PKI. Enterprises achieve phishing resistance by eliminating passwords, use of cryptographic key pair binding, and meet your goals for reducing friction, MFA fatigue, Help Desk calls and operational complexity.
Along with FIDO2 key pairing, SDO’s proven phishing-resistant enhancements include desktop-to-app pinning and other MFA resilience capabilities that deflect MITM attacks, push bombing, SIM card swapping, and other attacks [LK TO ADD LINKS].
SDO’s ‘zero passwords’ approach delivers the fastest, broadest evolution toward phishing-resistant MFA: zero passwords, zero apps left behind, and zero change required to your backend infrastructure.
Frequently Asked Questions
1. How much does phishing cost businesses every year?
Credential abuse still factors into 80% of security breaches (80+% still involve a human element). Breaches, according to the IBM report referenced above, cost $4.88 million on average, reflecting a 10% increase from the previous year.
2. Are investments in phishing awareness training worth the money?
Phishing awareness training helps but represents a partial solution—at best—that does not go far enough. Research summarized by TechRadar found, “The number of workers clicking on phishing links saw a major increase in 2024, putting businesses of all sizes at risk of compromise.” Annual research from Knowbe4, a phishing training provider, reveals 4.6% of workers will still take the bait tangled in a phishing scam after a full year of extensive training.
3. How have phishing attacks changed over the years?
Phishing attacks have expanded beyond targeting email to include attacks on voicemail (vishing), QR codes (quishing), search engines (through SEO poisoning), and popular sites running referrals in comments or malicious ads.