Managing identities across an enterprise is one of the bigger challenges facing the world of digital security.
In a company where large numbers of users access multiple applications in a diverse work environment, managers need reliable tools that allow smooth access for workers, while maintaining strong authentication standards.
Making Some Order
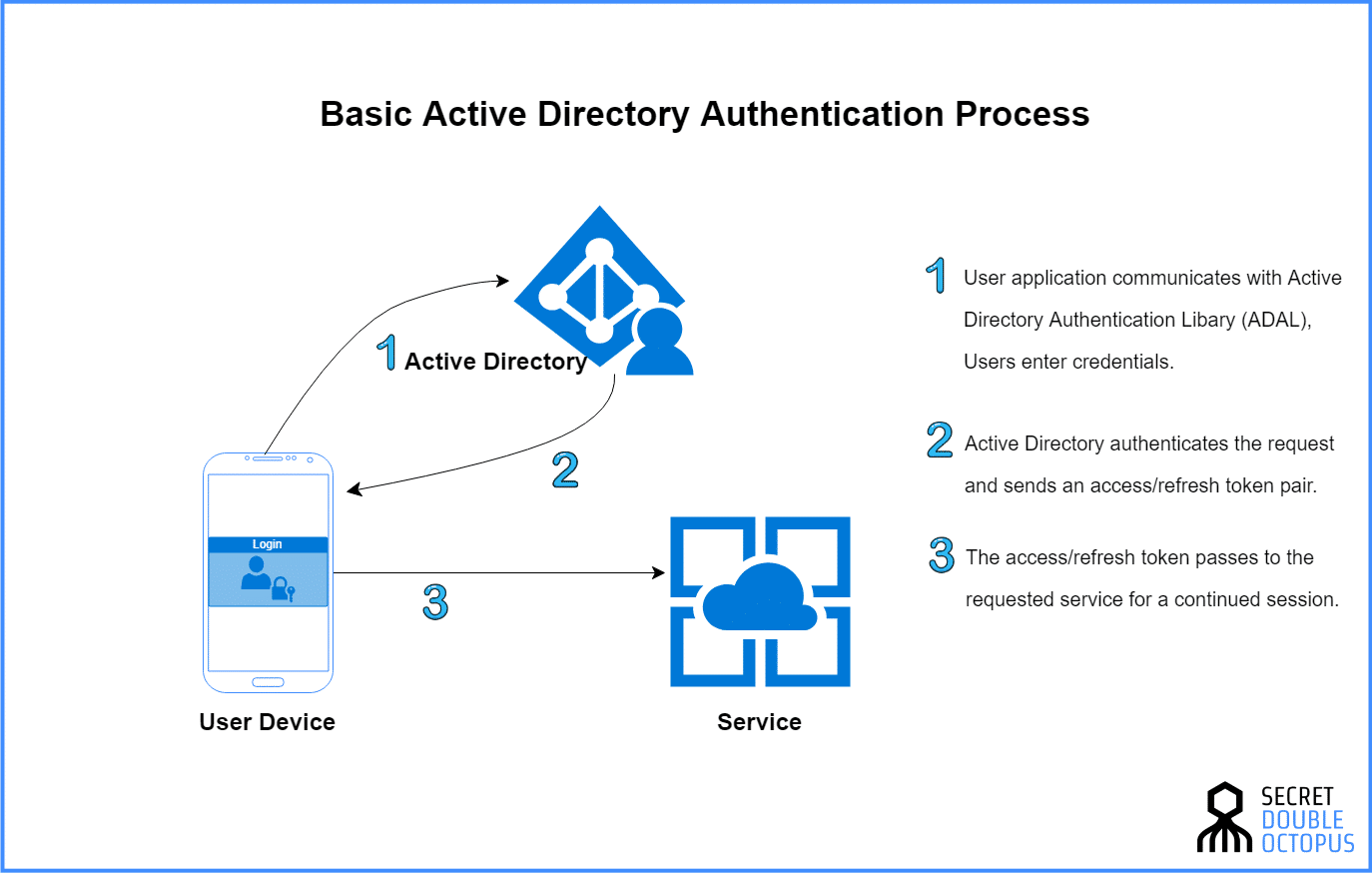
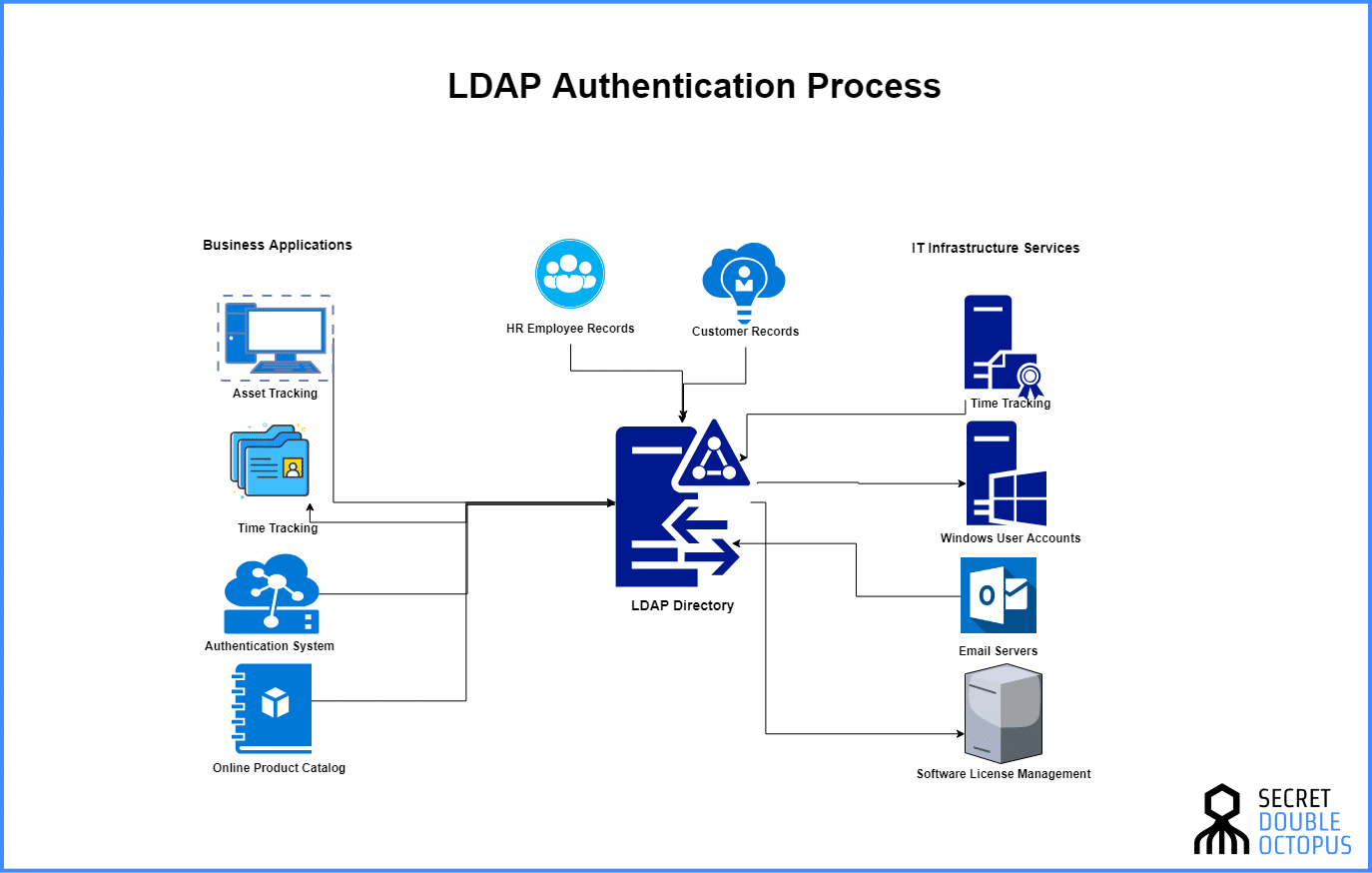
When looking at the most common tools used in enterprise authentication today, there’s a lot of talk regarding these particular two systems: Lightweight Directory Access Protocol or LDAP and Microsoft’s Active Directory (AD).
 Click to enlarge
Click to enlarge
First, it’s worth drawing a critical distinction.
Active Directory is a directory service that provides authentication (in addition to other tools) in a Windows environment. LDAP, on the other hand, is an application protocol for querying and modifying items in directory service providers that support it.
In other words: AD is a database system and LDAP is a way of talking to it.
So the question is not LDAP or AD authentication.
Rather what managers need to ask is how secure is it to integrate LDAP protocols for their AD systems.
The flaw in LDAP’s security relates to how it communicates authentication details. By default, LDAP’s authentication, or “binds,” will pass user ID’s and passwords in clear text between the requester and the server. This means that anyone or anything with access to that communication path can view the details and gain access to sensitive information. This system has been shown to be highly vulnerable to Man in the Middle (MITM) in which hackers can observe the transmission of data unbeknownst to the two communicating parties.
 Click to enlarge
Click to enlarge
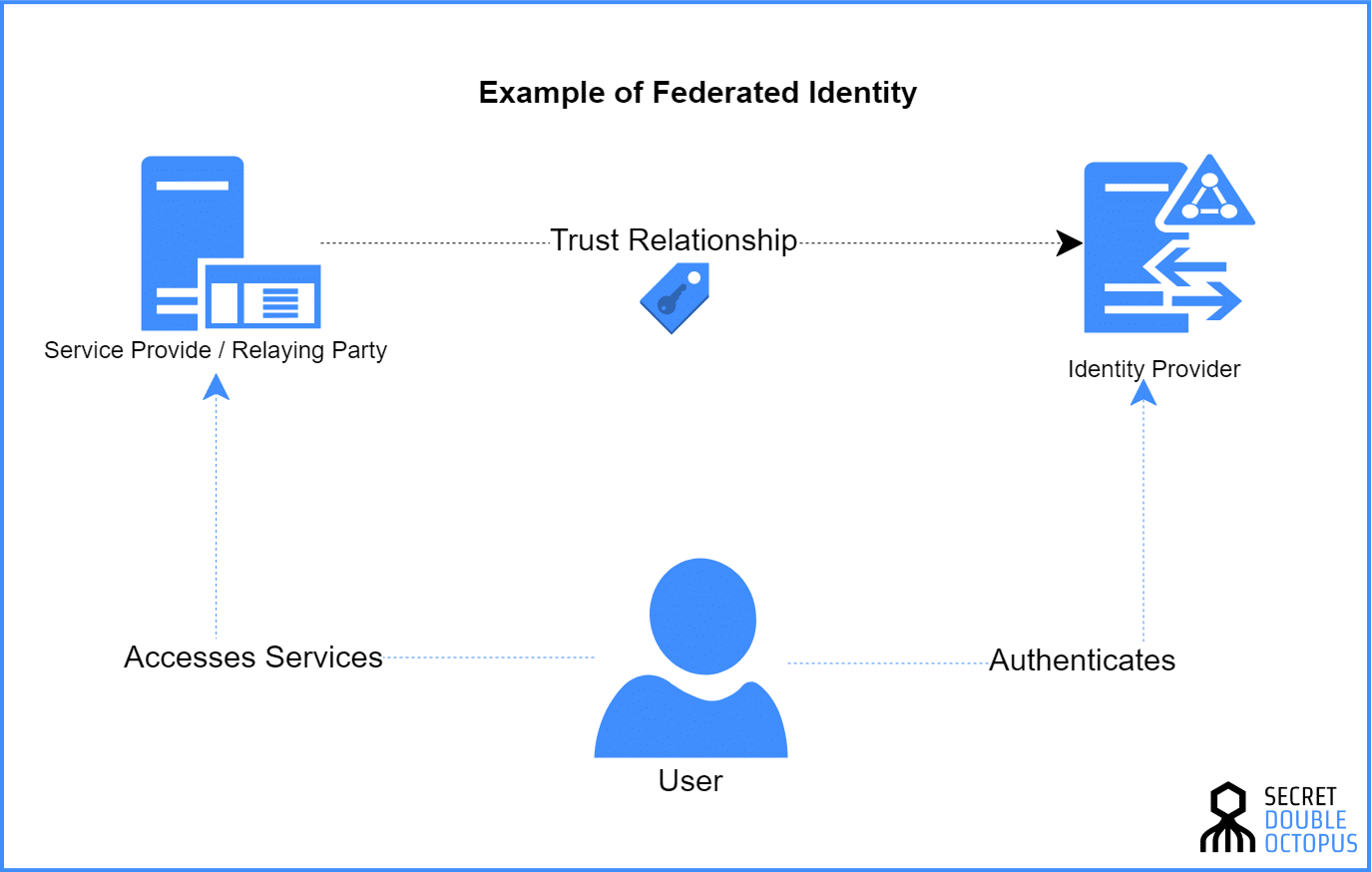
So What’s Active Directory Federation Services (AD FS)?
Active Directory Federation Services (AD FS) is a part of Active Directory (AD), an identity directory service for users, workstations, and applications that is a part of Windows domain services, owned by Microsoft. AD FS provides AD users with the ability to access off-domain resources (i.e. web-based services or another domain) using their AD domain credentials. AD FS uses the concept of identity federation to allow users on one domain to access another domain without needing to authenticate separately to the other domain.
To enable identity federation, a trust relationship is established between two domains – the one where AD FS is running and an external resource/domain. Once trust is established, AD FS can provide attestations about the authenticated identities of users to the external domain instead of requiring users to authenticate separately.
 Click to enlarge
Click to enlarge
Active Directory Federation: Is it worth it?
Federated Identity Management (FIM) was a huge leap forward for digital identities. FIM set up agreements and standards that enable the portability of identities across numerous applications, and even across multiple enterprises. What this meant for users is that one set of login credentials could be used to access the full spectrum of a network’s data and applications.
What FIM meant for applications, Active Directory Federation Services (ADFS) did for individual AD systems. This is an incredibly useful tool for companies using an existing on-premise Active Directory service and then integrating an Office 365 service. Such an organization now has two Active Directories to worry about. Instead of demanding users log in to each AD separately–one to open company files, and the other to access 365 resources–AD FS allows users to sign in once and achieve access to both. The benefits to this integration include:
- All data is centralized across the network in a single synchronized entity
- Users can intuitively view and find data that they have access to and locate data shared by colleagues
- Applications and services on the cloud-based Azure can be accessed from the initial login
However, there are drawbacks to implementing ADFS.
In terms of infrastructure, ADFS requires at least two separate servers and the set up of a “server farm” to integrate these machines and or clouds, in order to support authentication. Furthermore, additional servers in one scheme mean more points of failure and a higher risk of the system shutting down due to technical malfunctions.