Virtually every enterprise IT team we talk to asks if SDO can extend passwordless authentication to Linux hosts. [Spoiler alert: we do.] Why do they ask about Linux when most breaches involving credentials start with end users divulging the secrets they’re sworn to protect?
Because it’s crucial for a passwordless MFA solution to address the broadest range of workforce use cases out of the box in order to reduce risk. You’re not really passwordless, or even phishing-resistant, if 10-20% of your users still use passwords to log in ten times a day.

Linux MFA really matters
Modern businesses and IT departments run heterogeneous computing environments. Windows dominates among remote workers, web and creative gurus still cling to their MACs, and senior execs use what they want when they want.
But Linux hosts still dominate in the infrastructure. You might even say most company’s “crown jewels” live within Linux systems, which makes them a prime target for attack, even though devices may reside within the network perimeter.
Attackers, being developers and engineers at heart themselves, know only too well that aspects of your layered security defenses do not extend across backend infrastructure. Strong authentication for Linux endpoints, for example, remains virtually absent from conventional—let alone passwordless—authentication.
Most passwordless MFA vendors don’t even extend FIDO2 support, which CISA lists as one of only two ways to achieve phishing-resistance, to Linux hosts. So, what are we doing to change this?
Extending support to passwordless MFA for Linux
Everyone agrees passwords need to be banished from user authentication completely so the industry is ginning up solutions. Today, most environments join their UNIX or Linux systems to Active Directory (AD) to utilize network-based credentials from their identity store. This configuration can be used to push the passwordless experience to the remainder of the environment, or more precisely, to any device that can be configured for Radius authentication.
But, IT then needs to maintain local accounts for individual Linux devices. This approach lacks scale, especially when you have hundreds of Linux admins who may have 5 or more accounts in the environment, all of which IT needs to manage.
An easier, more inclusive approach to Linux MFA
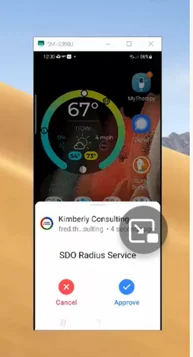
SDO delivers a more secure and streamlined approach to monitoring privileged users. The Octopus passwordless authentication platform proxies Radius authentication with workforce authentication directories like on-premises AD, Azure AD, and Cloud services like Okta’s universal directory to simplify Linux user identity administration.
RADIUS proxying eliminates the need for IT administrators to manage multiple local host accounts used to login to each network appliance server individually. System admins simply use a single AD account issued by identity providers to deliver passwordless MFA across Linux devices. IT can easily disable individual credentials, for example, when a Linux admin leaves the company, through this single account in AD.
“If passwordless MFA is so great, how come we’re all not doing it?”
Two reasons:
- Most passwordless MFA solutions do not address all or most workforce uses cases which somewhat defeats the purpose
- Change is hard (particularly when it involves backend user devices and the backend infrastructure), and IT still has its hands full
But it’s happening. Zero Trust mandates, cyber insurance premiums, and risk itself are combining to make passwordless MFA a real thing sooner rather than later.
The SDO platform was architected by IT for IT, to automate credential management and make passwordless MFA more secure, scalable, and best of all simpler. For users, C-level execs, and IT.
Octopus lets admins centrally manage ALL workforce credentials across, potentially, all workforce platforms out of the gate, extending the passwordless experience across the environment without, in the case of Linux, managing hundreds or even thousands of local accounts.
IT easily controls elevated privileges; users simply see what they’re allowed to do and access upon logging in. Along with Linux, SDO’s Radius authentication extends passwordless MFA to Layer 3 network switches and other infrastructure devices using the same simple approach.
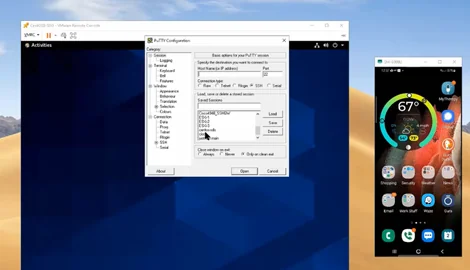
Watch a quick demo
We built a testbed and created a short video demonstrating a simple, step-by-step passwordless login. Sales Engineer (SE) John Kimberly shows how users authenticate directly into Linux hosts using PuTTY (public key authentication based on SSH keys), push notifications—“something users have”—and fingerprints—“something they are”—instead of passwords.
The demo takes minutes, the whole process takes seconds. Check it and Watch Now