The many horror stories that regularly surface on the web make it certain beyond the shadow of a doubt that plain passwords are a cumbersome and bad security practice. A recent survey by Secret Double Octopus found that the outstanding majority of corporate employees are eyeing password-free technologies as their preferred method of authentication, both from a security and an ease-of-use perspective.
Among the most prominent password-free authentication methods are mobile push notifications. Several big tech companies have already provided push notification authentication alternatives for their consumer-facing products. But the bigger corporate industry was still lacking reliable push notification authentication solutions—until recently.
What is push notification authentication?
Push notification authentication validates login attempts by sending access requests to an associated mobile device. When you register your account, you link it to a mobile device you own. Afterward, whenever you try to login to your account, you submit your username or ID. Instead of entering your password, you receive an access request notification on your smartphone, which you can approve or decline.
See a live example of the authentication process to a Windows work station:
What are the Advantages of Push Notification Authentication?
There are several benefits to push notification authentication. The obvious advantage is that users won’t need to memorize and manage passwords. Additionally, notifications provide a seamless and user-friendly experience. Instead of fumbling with their phone to find and open an authenticator app, users can immediately validate their login by having the authentication request come to them. Validating an authentication request is often speedier than entering a complex password.
Google provides a push notification authentication option for its suite of online services and applications such as Gmail, Google Drive, Docs, Calendar, etc. Microsoft has also rolled out a similar service for its Outlook.com services. The setup for both services is easy and users can get started in a matter of minutes.
However, the problem with these solutions is that they only work with the services of their respective companies and the limited applications that integrate with their services. This makes them unavailable to organizations that use enterprise-level and proprietary solutions. Moreover, most of these push notification technologies are offered as secondary authentication methods, and they have workarounds such as SMS and authenticator app one-time passcodes (OTPs), which make them vulnerable to crafty hackers.
Just like SMS, push notifications in and of themselves are not a security feature. Messages travel in the clear through the push provider (Apple and Google) and we have seen Push services compromised in the wild.
How Secured Is Push Notification Authentication?
The security of push authentication depends on the security of the application receiving the push notification and the device on which it is running. Security, therefore, varies by implementation and security posture of the host device.
The advantage of push notification is that it leverages the security infrastructure of tech giants (Google, Apple), which are considered the most secured infrastructure in the market
Is Mobile Push More Secured Than Software One Time Passwords (OTP)?
Software OTP codes can be compromised by using social engineering techniques. Mobile push requires an attacker to gain possession of the mobile device receiving the notification or cause the owner of the device to authorize a fraudulent authentication request in real-time, which is a lot harder to do than stealing OTP codes via phishing and other social engineering techniques.
Is SMS More Secured The Push Notification?
The US National Institute of Standards and Technology (NIST) updated guidelines stating that SMS-based OOB Authentication should be deprecated because of the risk that SMS messages may be intercepted or redirected (as happened with the Reddit Hack). Push notifications, when implemented properly, are resistant to interception or redirection and are, therefore, more secure than SMS.
Enterprise Push Notification Authentication – Access Control at its finest
For all these reasons, Push Notification is expected to be the fastest growing authentication factor in the workspace. According to Gartner, 50% of enterprises using mobile authentication will by 2020 adopt OOB mobile push as a mainstay of authentication, compared to just the 10% who are using it today.
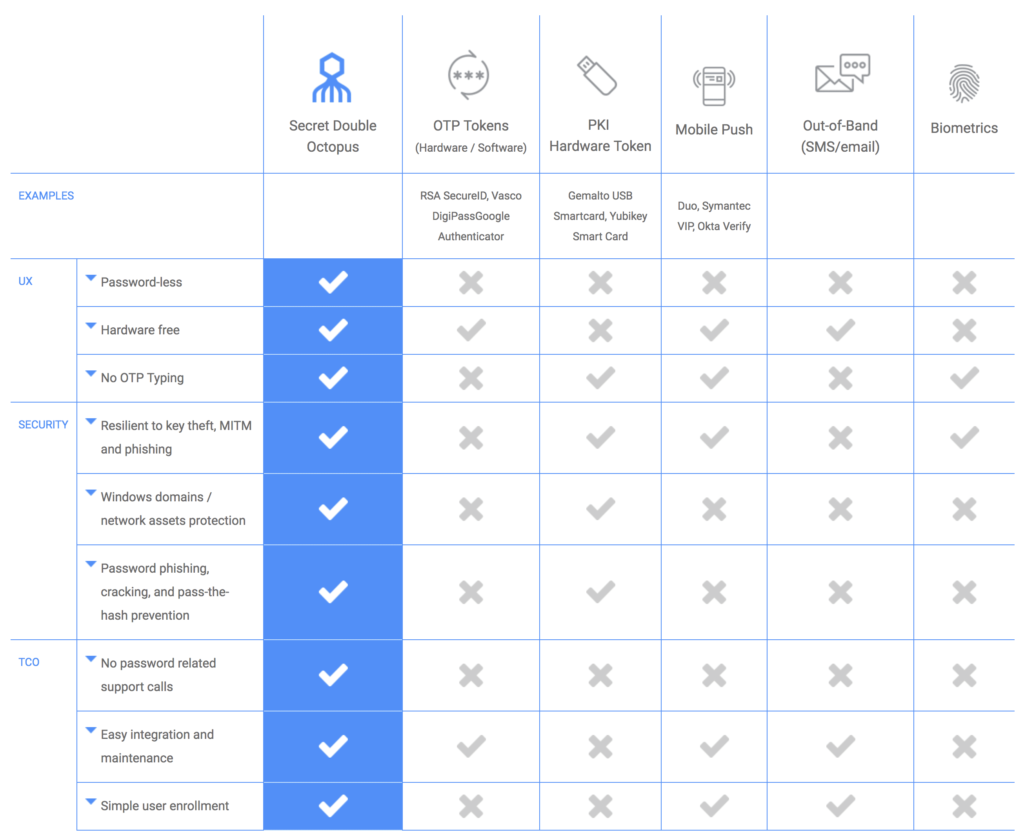
Secret Double Octopus has developed an enterprise-grade security solution providing flexible, secure and easy-to-use push notification authentication for various applications. Secret Double Octopus succeeds where COTS solutions fail by removing bottlenecks and vulnerabilities that hackers can exploit.
To address the security limitations of Push, Secret Double Octopus has introduced a unique approach of multi route authentication. Based on the quantum-safe secret sharing scheme, this patent-pending technology prevents a single point of failure for the user identity.
The solution comes with an authentication server application that can be integrated into any application, including large enterprise platforms such as Microsoft Active Directory (AD). Every time a login attempt is made on an employee account, an access request notification is sent to the employee’s mobile device.
Secret Double Octopus neither stores nor exchanges secrets, making it immune to man in the middle attacks. The Octopus Authenticator uses multi-channel security and secret sharing to avoid exposing any single point of failure to hackers. Moreover, it integrates with biometric authentication technology already present on mobile devices for good measure.