Spear phishing.
It’s one of the more vicious methods used by today’s cyber criminals to compromise networks.
Phishing related attacks have been a favorite of the hackers tool kit for years. And these kinds of attacks are becoming more common and more sophisticated over time.
What is Spear Phishing?
In its most basic definition, phishing is an attempt to illicitly obtain account credentials such as usernames and password by disguising a communication as coming from a trustworthy entity.
Phishing comes in many different varieties.
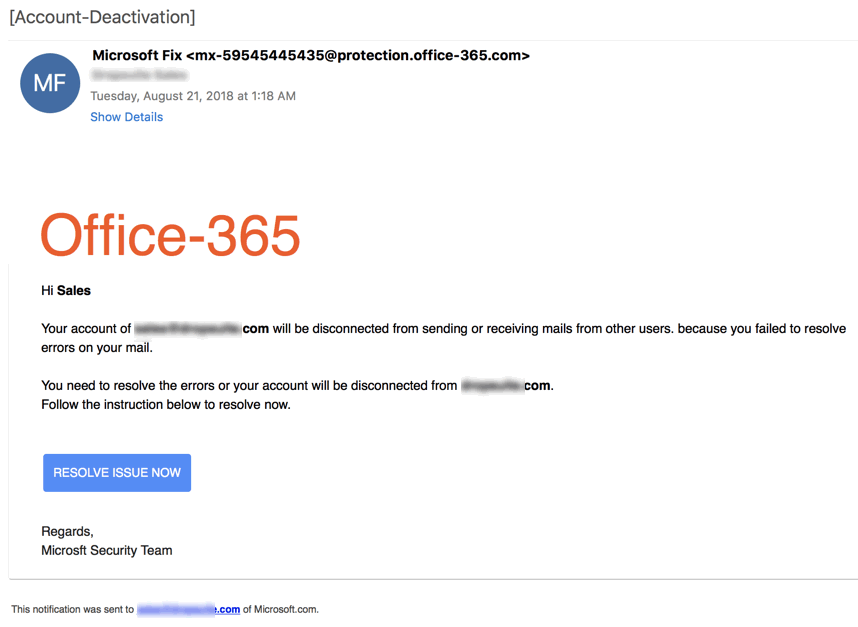
In the most common phishing technique, the same email is sent to millions of users with a request to fill in personal details. Any details obtained are then used by the phishers for their illegal activities.
A slightly more sophisticated method called Content Injection involves changing a component of a reliable website. Visitors who engage with the compromised feature are taken to a page outside the site where they’re instructed to fill in credentials.
Then there’s Spear Phishing. While traditional phishing uses a ‘spray and pray’ approach, the mass sending of emails to as many people as possible, spear phishing is a targeted attack. Messages are tailored to the potential victim to convince him or her the communication is legit. This usually means hackers have collected at least of minimum of information on their target, such their place of employment, names of friends and associates, and sites they frequent, with any or all of these details helping to make the scam more believable.
One particularly devious form of phishing targets leading company officials. A ‘whaling’ attack is when fraudsters try to harpoon an executive whose credential’s grant special access privileges to the organization’s network.
Phishing Attacks have Doubled Over 2018
Recently, the industry has seen a sharp rise in instances of phishing. According to research published earlier this month by Kaspersky Labs, phishing attacks doubled over 2018.
More than merely increasing in commonality, attacks are also evolving, as hackers produce new techniques to perfect their phishing campaigns. Take the recent scheme identified by researchers at Akamai, in which hackers used a fake Google Translate URL to disguise a malicious site. That closely followed the much publicized Apple Phishing scam where criminals carefully designed messages that mimicked those from Apple’s App Store.
Hackers conducting phishing campaigns don’t only go after individuals. Very often the victim is an entire corporation. In 2013, hackers managed to penetrate the systems of U.S. retail giant Target after a successful phishing attack on a third party vendor that had trusted access to Target’s servers. The infamous shutdown of the Ukrainian national power grid in 2015 is another stark example. According to expert investigations into the incident, hackers were able to penetrate the grid with powerful malware by targeting Ukrainian grid workers with a phishing campaign.
Considering the threat posed by phishing, it’s no wonder administrators are scrambling to find answers to this highly effective social engineering scheme.
The problem is, traditional solutions to secure networks from phishing are all providing a band-aid approach. Most experts suggest various methods for employees to identify fraudulent emails. Some have presented complex solutions such as applying artificial intelligence to flag suspicious communications.
But all of these solutions fall short for one simple reason: they don’t address the basic vulnerability every phishing campaign capitalizes on–the password.
No Credentials = Nothing to Phish
The Octopus solution: replace traditional credentials with high assurance, out-of-band authentication.
The very existence of passwords means that there will always be a target for phishers. But removing passwords from the picture means eliminating the threat of phishing at its root.