Nowhere is the absolute assurance of the user’s identity more important than when privileged admins log into remote servers using the remote server protocol (RDP). The stakes can be doubly high for heavily regulated industries like financial services, healthcare, and other critical infrastructure industries.
One global financial services firm specializing in insurance wanted to harden security by equipping admins to use FIDO — the gold standard for high-assurance authentication — to access servers running RDP anywhere in the world. Because FIDO and RDP don’t usually deploy together, the firm explored SDO’s innovative approach to bridge the gap.
FIDO Authentication for RDP Make Remote Server Login Doubly Secure
For server rooms in the same building, administrators can walk down the hall and plug their FIDO keys into USB ports on the server to authenticate. But what about machines running at other locations?
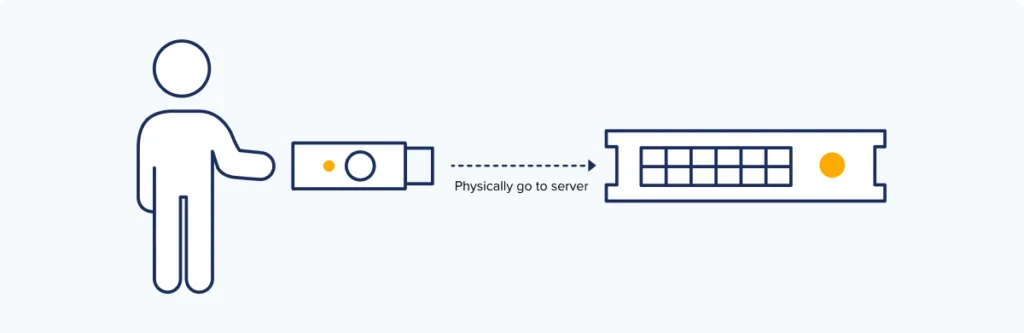
For years, the US-based global conglomerate with more than 120K employees worldwide used a partially homegrown multifactor authentication (MFA) tool to secure server logins. But as the solution reached end of life, the management team feared it might fail to support ongoing server upgrades.
BYOD and Phishing-resistance Drive the Search
The company’s CISO was clear about one thing: wanting the new server access solution to be phishing-resistant. Like most, the security team considered FIDO the best proven approach for building phishing-resistant passwordless authentication.
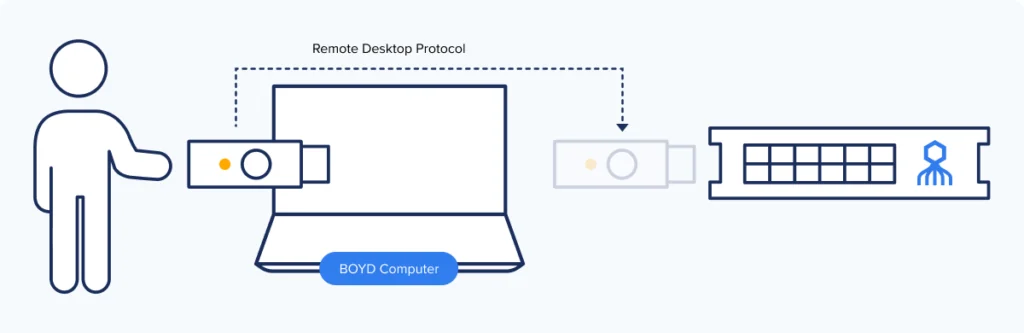
But: servers require users to plug FIDO keys directly into the machines they’re asking to access — a pivotal step that cannot be completed with RDP when servers sit at remote location.s The financial services provider already used identity and access management (IAM) technology from Okta but its existing solution did not support FIDO for RDP to remote servers.
In addition to seeking a new high-assurance RDP access method , the company wished to stop issuing company-owned phones to workers. As a global company, they faced the added challenge of not being able to require bring-your-own-device (BYOD) users in certain countries to download specific apps — like authenticators — onto their personal devices.
The multi-faceted search led the security team to call in Secret Double Octopus (SDO) and put an innovative solution for enabling FIDO-based authentication for RDP access to servers worldwide.

Octopus Extends the Reach of FIDO to RDP Authentication
SDO’s Octopus Passwordless Authentication platform solves the problem by allowing admins to plug their FIDO keys into whatever computer they’re using to update remote servers from, instead of the servers themselves. With the Octopus approach, no agents are required on the local host to verify identity locally then communicate via secure tunnels with an Octopus agent running on the main servers.
Agents installed on the common servers support secure FIDO-based access by employees connected to the network anywhere in the world. Down the road, the Octopus solution has implications for achieving new levels of security and scalability for accessing cloud-based servers hosted by public cloud providers like Google and Amazon Web Services (AWS) and filling the gaps left by Privileged Access Management (PAM) solutions.
But for now, this ‘only Octopus’ approach gives large global companies a scalable, easy to install and manage option for building strong remote authentication that secures thousands of servers — and tens of thousands of admins — worldwide.
FAQ
What is RDP?
RDP is a network protocol offered by Microsoft. It allows a graphical connection to another computer or server over a network instead of a text-based command line interface (CLI). RDP is commonly used to connect to jump servers in cloud environments. Linux equivalent are Remote Desktop Server (RDS) and Virtual Network Computing (VNC).
How do you secure RDP?
RDP securely enables authorized users to access remote systems using the Windows GUI. However, RDP security is not infallible, as vulnerable passwords typically protect it, and many MFA systems don’t support RDP coverage. High-assurance passwordless MFA provides a level of “beyond a shadow of a doubt” identity proofing for these privileged remote accesses.
Who uses RDP
RDP is available for all Windows users, but IT admins mostly use it to repair, configure, and upgrade remote servers across geographically distributed enterprises.