On the Octopus Blog, we’ve dedicated ourselves to tracking the evolution of credential-targeting threats endangering networks today.
One of the more nefarious pieces of malware to be identified in recent time highlights both the risks posed to systems from Password-based authentication, as well as exemplifying why the industry’s approach to defense is misdirected.
Enter The Great Duke of Hell
Recently, analysts from the Microsoft Defender Advanced Threat Protection Research Team issued a warning about a credential-stealing malware targeting Windows users.
The trojan program that gathers user credentials was initially discovered in 2017 and named Astaroth, the “the Great Duke of Hell”.
According to Microsoft’s telemetry, the most recent campaign commenced on May 19 and carried on into mid-June, with at least four significant spikes inactivity. The two biggest surges by far took place between May 26 and June 1, and then again for a five day streak beginning on June 2. The typical attack process would begin with a spear-phishing email containing a link that if clicked installs the Trojan.
Fileless Malware – The invisible Man
What makes this malware so dangerous is that it uses an “invisible man” technique, which means that the attack chain uses only legitimate system tools.
Astroth is part of the broader ‘fileless’ family of malware. Unlike attacks carried out using traditional malware, fileless malware attacks don’t require attackers to install software on a victim’s machine. Instead, tools that are built-in to the operating system are hijacked by adversaries and used to carry out attacks. Essentially, the operating system is turned against itself. This means that there’s no signature for antivirus software to detect, which greatly decreased the effectiveness of these programs in routing out fileless malware attacks. Some next-generation security products claim to detect fileless attacks by honing in on suspicious activity patterns using advanced diagnostics. The reality is however, that discovering fileless malware attacks remains very challenging.
In the words of Microsoft analysts, Astaroth “lives off the land”, as it only runs innate system tools throughout its complex attack chain. In fact, the attack involves multiple steps that all use various fileless techniques. Throughout the attack, the compromised computer is programmed to execute malicious commands on itself. This allows the Duke of Hell to hide in plain sight, slipping through most malware detection systems.
The Evolving Threat to Credentials
Astaroth is what’s known as an Advanced Persistent Threat or ATP. Unlike other breaches which are more like one-time hit-and-runs, ATPs are designed to surveil systems or extract data from them over time. This is a preferred method when it comes to stealing passwords and other authentication data. The longer hackers can drag their net through a system, the more likely they’ll acquire the high-value identities they seek.
Sophisticated methods that target vulnerable passwords are being developed at an increasingly fast rate–and their availability increasing. Use of credential dumping programs such as Mimikatz, and attacks such as credential stuffing, are now almost commonplace.
In its own way, Astaroth marks a milestone in the development of credential-targeting cyber threats. Astaroth malware targets password installed techniques, which means the malware does not have to download files to be stored in persistent memory – it is installed within the RAM of the computer itself.
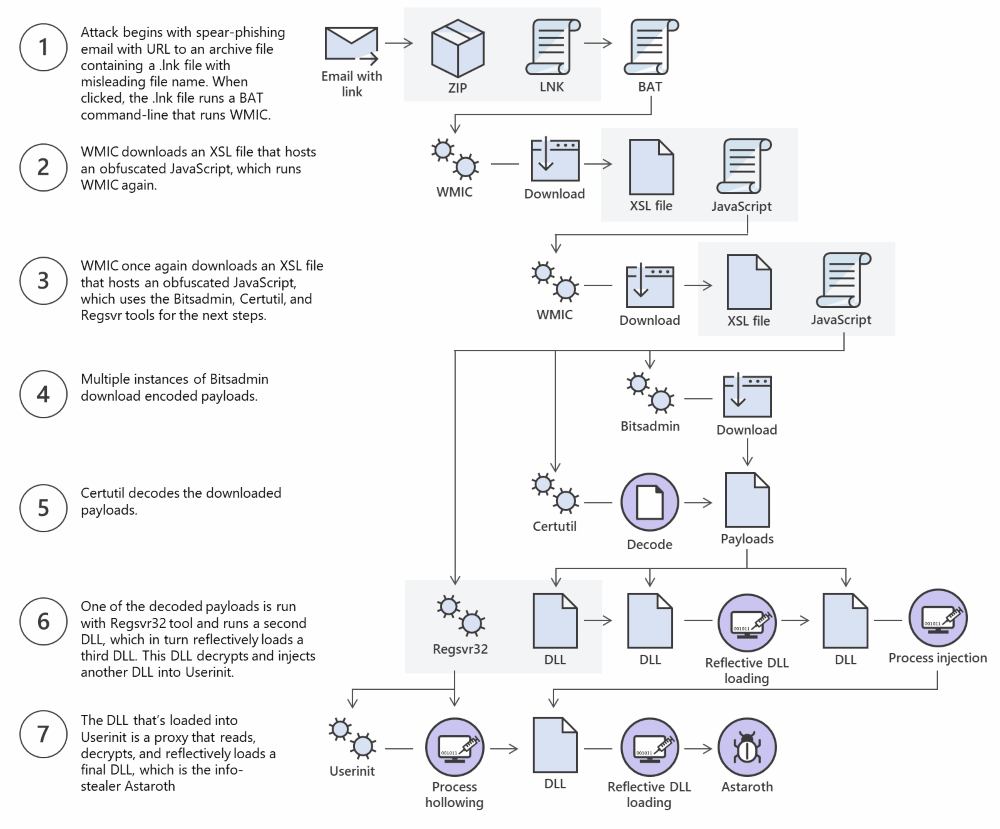
Image source: ZDnet
Duke of Hell provides another example for why existing protection methods seem to always be a step behind the attack.
Despite their outdated and outmoded nature, passwords remain the staple for most authentication platforms in use today. Recognizing the extremely sensitive nature of passwords, the industry has built digital ‘walls’ and other complex ways of protecting them. But what Astaroth and other attacks have shown, is that as long as there is are credentials to steal, hackers will find a way to get around the defenses.
This is where Secret Double Octopus’s approach comes in.
Defending the Castle by Throwing Away the Key
Instead of scrambling to protect passwords, the Octopus Authenticator dispenses with them completely and in legacy systems automates password management at the backend while providing a passwordless UX, allowing administrators to simply circumvent the wide array of threats passwords present to the network.