Cybercrime and cybersecurity remain locked in an endless game of ‘one-ups-man-ship.’ Security engineers, service providers, and vendors no sooner invest in new controls than attackers find ways to steal the keys and combinations — or sneak around defenses altogether.
Such is the case with multi-factor authentication (MFA) and the terrifying threat technique known as SIM swapping. With the rise in 2FA/MFA, that nagging fear that your credentials might leak out gets compounded by a new, more acute source of angst:
What if your phone falls into the wrong hands?
That’s effectively what happens with SIM swapping when crafty attackers take control of your mobile phone number and intercept 2FA/MFA requests to access assets and accounts — without ever laying hands on the phone itself.
This blog will detail how this technique works, and ways to educate and insulate workforce users against it.

How SIM swapping works
While not the ultimate target, social media accounts factor into many SIM swap attacks. Attackers troll the likes of Facebook and Instagram for bits and pieces of personal history they can use to guess answers to security questions.
From there, they try tricking mobile providers into thinking they’re legitimate users and tell the carrier to transfer the phone number to a new SIM card that they control. This often takes place remotely, sometimes at night, so that texts from the carrier confirming the swap go unnoticed.
SIM Swap Attacks Going Mainstream
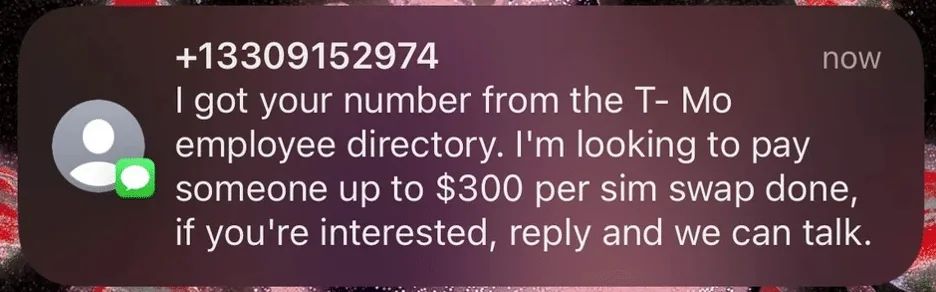
Source: LowkyRep
Or, it might take place from within the retail portion of buying a new phone and switching over user data, apps, etc. Not a pleasant thought.
What happens when SIM swapping succeeds?
Once the attacker has control of the number, they can start changing online account passwords to lock the real user out of their banking profiles, transfer funds, sell crypto, and compromise social media accounts, healthcare records, and other privileged data.

Who’s at risk for SIM swap attacks?
Just about everybody. Surveillance, or at least due diligence, may be best suited to targeted attacks on individuals, but in some cases, large-scale attacks on up to 5,000 people have succeeded.
Most attacks are financially motivated but some can be “just to prove we can,” like an attack perpetrated against Twitter founder Jack Dorsey back in 2019. Hackers gained access to his accounts and began making incendiary posts attempting to harm his reputation.
Even carriers themselves fall victim. Following a breach of T-Mobile, criminals made off with millions of phone numbers and relevant personal data that allowed them to orchestrate mass SIM swapping and begin compromising MFA.
SIM swapping weaponizes MFA
Most 2FA and MFA deployments involve the use of one-time passcodes (OTPs) texted to a user’s mobile phone, or sent via email, which may run on the phone as well as on desktop PCs. SMS-based verification adds a strong second dimension to traditional passwords, adding something users have — the right phone or email account — on top of “something users know” that can be lost, leaked, or stolen.
Adding “something users have,” like a phone, tablet, or hardware security token, on top of passwords strengthens authentication considerably. But SIM swapping compromises the “something users have” pillar of identity verification by reassigning the phone number to another device that is not within enterprise IT’s control.
Sometimes known as simjacking or hijacking, SIM swapping intercepts and compromises MFA designed to protect privileged assets. Instead of adding new layers of protection, 2FA/MFA becomes a tool or threat vector. Adding a third pillar of identity, “something users are” as verified by a voice, face, or iris scan can help, but doing so adds to cost and complexity.
Phishing adds a dangerous dimension
Phishing can also lead to SIM swapping as scammers trick users into revealing credentials and/or personal data, then use that to con carriers into transferring phone numbers to new identity modules. Game on. After years and even decades of investing to educate users to spot phishing scams, too many workers still take the bait. So much so that phishing remains one of the leading attack vectors that evolve into malware, ransomware, DDoS, command and control (C2) and other popular, often devastating attacks.
How to detect SIM swapping — and what you can do about it
Most victims only discover they’ve been compromised when their phones stop working. Because the device itself no longer connects to their provider’s network, the real users stop getting calls, texts, directions, and access to games and online account apps.
Another clue happens when users do receive texts from a mobile carrier saying their SIM card or phone number is being reassigned to a new device. Or, they might notice strange activity on social media and other online accounts. That’s the time to get busy calling banks, card issuers, and other providers to put a freeze on assets and move accounts to a brand-new email account.
When the smoke clears — or better yet before the fire gets started — users should check with their mobile providers to see what sorts of alerts they offer before making changes to your account.
Last but not least, change or replace device and account passwords altogether.
An ounce of prevention: 3 ways to guard against SIM swapping
1. Strengthen MFA
One option is to go the traditional route and layer additional verification factors into MFA. Helpful tips include:
- Rotate passwords and make them complicated
- Use an authenticator app that links verification to your device versus your phone number
- Add biometrics such as fingerprint, retinal, or voice scanners
- Purchase physical authenticator tokens such as FIDO keys
- Use a password manager to encrypt and protect your various passwords
- Buy a dedicated SIM card you don’t use anywhere else
2. Stop the phishing
Continue to invest in user education and . . .
3. Get rid of passwords
The third and by far optimal route to stopping SIM swap attacks is to do away with “what users know” and with SMS-based OTPs altogether.
A “push” toward smarter passwordless MFA
The vulnerability of MFA to SIM swapping stems from the broad use of SMS-based text messages. SMS communication takes place over SS7, a UDP-based protocol, and is tied, as we’ve said, to a phone number instead of a phone.
By comparison, MFA apps that use push notifications instead of texts get loaded onto the phone itself. Registration of the app and user info takes place over the Internet using TCP and HTTPS which cannot be spoofed the same way SMS can. The authenticator app gets linked to the device’s unique hardware security module (HSM).
Once user account details get registered with the MFA application, push notifications that appear to function the same way as SMS-based texts can be sent to complete authentication. The user experience is equally simple, if not simpler — the push notification might be just a box to check — but attackers have no way to insert themselves in the process without possessing the device or cryptographic keys that bind the app to the account or service.

Why passwordless MFA?
Taking user passwords out of the user authentication equation does two powerful things:
- Eliminates or replaces “what users know” as a factor in verifying identity
- Makes MFA phishing-resistant (when done right)
If the solution in question also allows IT to continue using passwords behind the scenes, and the entire directory infrastructure does not need to be retooled to support PKI right away, Octopus passwordless MFA also supports broad or complete enterprise use case coverage. This last point is extremely important in allowing passwordless MFA to be rolled out across an organization quickly, without overburdening IT teams or requiring premature upgrades.
