Ninety per cent (90%) of data breaches still start with a phish. And as it should be obvious by now, MFA can’t stop phishing.
The balance of power currently favors adversaries who’ve commercialized email wizards, social engineering savants, and automated man-in-the-middle (MitM) weapons into a lucrative phishing-as-a-service (PHaaS) enterprise—all at the ready to help even novice attackers shift their gaze to your unsuspecting workforce. Phishing is the cheap and proven initial access method that leads to data theft and ransomware. Writing zero-day vulnerability malware takes considerable skill. Paying for PHaaS, not so much.
Did checking the box move the needle?
It is a security insider’s mantra that compliance does not equal security. And MFA compliance is no exception.
Every regulation and cyber insurance checklist calls out MFA, but most need to define the quality or capability required. Unfortunately, they make vague statements similar to the new EU financial services directive, the Digital Operational Resilience Act (DORA) Article 9:
“implement policies and protocols for strong authentication mechanisms, based on relevant standards and dedicated control systems.”
We think that means “industry best practice,” but this isn’t clear.
Or when we look to the proscriptive CIS Critical Security Controls V8 for guidance, as many financial services and other internet-facing enterprises do, you find these instructions:
Where MFA is to be used is outlined in Control 6, Access Control Management:
- 6.3 Require MFA for Externally-Exposed Applications Users
- 6.4 Require MFA for Remote Network Access Users
- 6.5 Require MFA for Administrative Access Users
Internet-facing, remote, and privileged MFA are good starting points. But leave the enterprises exposed to imposters and uninhibited access to computers and on-premises resources.
Stopping phishing is included in Contol 14, Security Awareness and Skills Training:
- 14.2 “Train workforce members to recognize social engineering attacks, such as phishing, pre-texting, and tailgating.”
Phishing awareness has been the enterprise’s primary decades-long defence strategy, unfairly pushing the defender’s responsibilities on your unwitting worker.
As the security leader, you followed the compliance frameworks’ direction to implement MFA and institute phishing awareness training. The box is checked, but is that enough in the age of PHaaS?
Apparently not:
- CISA already declared that MFA as we know it can’t stop phishing, that only a passwordless, phishing-resistant MFA can. Check out CISA Guide: Implementing Phishing-Resistant MFA
- Phishing awareness training only gets you so far, and unfortunately, not far enough.
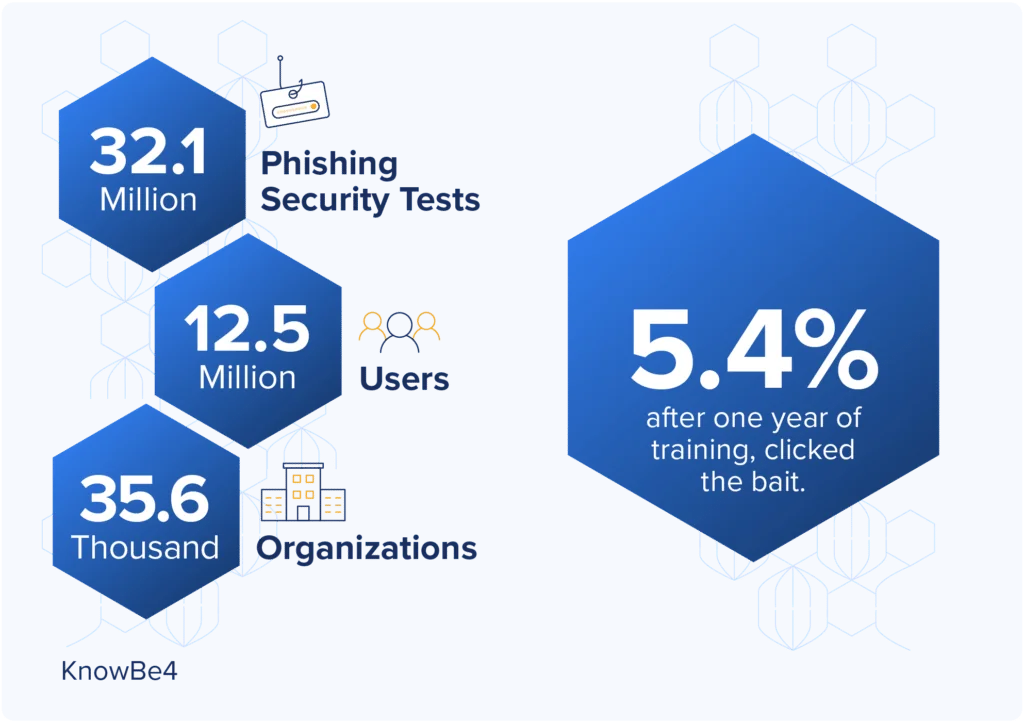
As the annual KnowBe4 report shows year after year, phishing is a numbers game with the advantage going to the attacker. Even the most tech-savvy businesses like Cisco and Uber fall prey to MFA attacks because people are people. They are, by nature, helpful and just looking to get their jobs done.
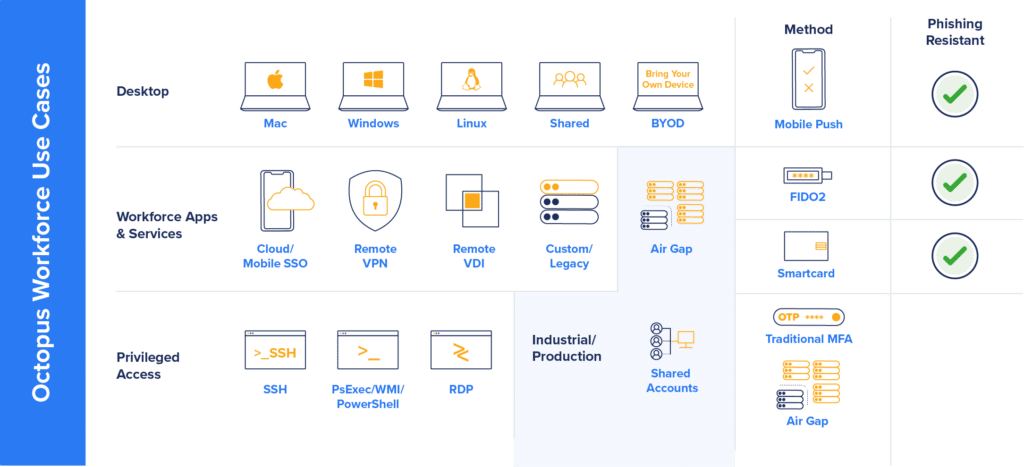
Only passwordless MFA takes the human factor out of the authentication equation by using the stronger “what you have” and “what you are” criteria for verifying identity combined with cryptographic binding the user to the apps. Users prove who they are; no judgments to make, no passwords to remember, or no manipulatable actions to avoid, relieving employees from phishing sentry duties.

“How do we know when MFA is good enough?”
Most standards just say MFA, but not all MFAs are the same. The identity guidance that spells out the requirements for each type of MFA is only found in NIST 800-63 (Digital Identity Guideline). The guide grades MFA assurance levels based on the potential harm a failed authentication might cause to an organization and its stakeholders.
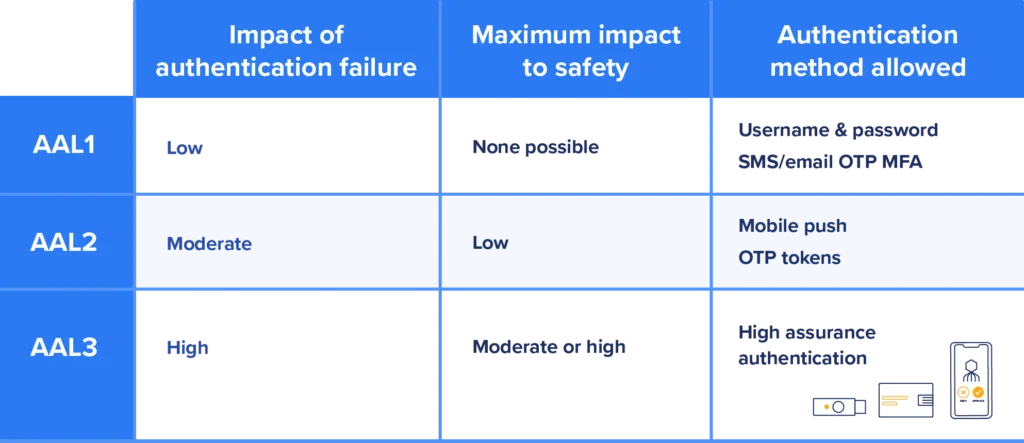
NIST 800-63 directly applies to federal government entities and radiates out to enterprises that do business with the government and those included in regulated industries through NIST 800-171 (Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations).
Safety becomes an extra consideration for CISOs in manufacturing, healthcare, and resource production industries for “Did I do enough.” Even a moderate risk to human safety leads to a need for high-assurance MFA.
So, did you do enough?
PHaaS has to be faced and dealt with today, and passwordless MFA is an available technology today. Traditional MFA no longer qualifies as a “best practice” unless it refers to gold-standard passwordless, phishing-resistant MFA.
Consider PCI DSS. If you pass every Qualified Security Assessor (QSA) official Report on Compliance (ROC) and then have a CHD security incident, you are officially out of compliance. Penalties track the degree of security due diligence applied.
Defending the highest assurance MFA method was applied is a reasonable defense. What comes after best? And you will have closed the door on the attacker’s ability to exploit passwords or phish users. They must move on to another target or pull out much more expensive weapons.
Better, faster, and cheaper? The paradox of high-assurance MFA
AAL3 is higher assurance than AAL1/2. By implication, enterprises resist the move to high assurance, assuming it must be more expensive and incompatible with their infrastructure. That assumption is usually based on past experience with deploying X.509 certificate smartcards:
- Hardware tokens are expensive
- Applications and directory infrastructure built for passwords don’t work with tokens
However, in the case of Octopus’s passwordless MFA, very little work is required by IT to upgrade the workforce to high assurance, and. doing so can be achieved with or without hardware tokens. Octopus provides AAL3 mobile push methods and supports hardware tokens so your workforce can choose which methods make sense for their job.
For example, some work areas don’t allow smartphones, and some workers are unwilling to use their personal phones. No problem. Why not let these workers expense a low-cost self-service device-bound passkey token from Amazon? However, research shows that most people (73%) prefer mobile push over other authentication methods.
Then, there is the higher ROI that passwordless MFA delivers for the business. Passwordless MFA pays for itself in the first year as:
- The workforce saves time without passwords to remember (a BBC study indicates up to 22 minutes, or 5% of a typical workday, per day)
- IT saves time without having to field password lockout Help Desk calls and by eliminating the all-hands-on-deck quarterly password rotation cycles
- IT buys down millions of dollars of security risk by taking away attackers’ ability to exploit passwords or phish your users
See the Octopus Passwordless ROI Calculator for the details.
And that’s not all . . .
All these benefits can be realized without changing the IT infrastructure driving operations today. Octopus works with modern authentication methods like SSO, FIDO2 passkeys, and X.509 certificates and with existing password applications and directories. So, no recoding apps or rearchitecting directory infrastructure.
Learn more about flexible, highest-assurance MFA
Get a demo or check out “Got Phished? How to Get MFA Right the First Time”, to see how Octopus goes beyond checking the box for MFA to deliver flexible, ultra-high-assurance MFA for heavily regulated industries at high risk for cyberattack:
- Improves compliance
- NIST AAL3 desktop MFA: cryptographic and proximity assurance that binds the user, desktop, and the authenticator. Mobile push or passkey token
- Phishing-resistant MFA with Octopus mobile push or passkey token for web apps, remote access, and on-premise specialed and legacy apps.
- Unified MFA for heterogeneous cloud and on-premises app and directory infrastructure (e.g., Okta, Ping, Azure, Active Directory)
- Users begin onboarding in an hour, and rollouts finish in days–versus months for other solutions–achieving enterprise-wide coverage with a fraction of the effort in a fraction of the time.