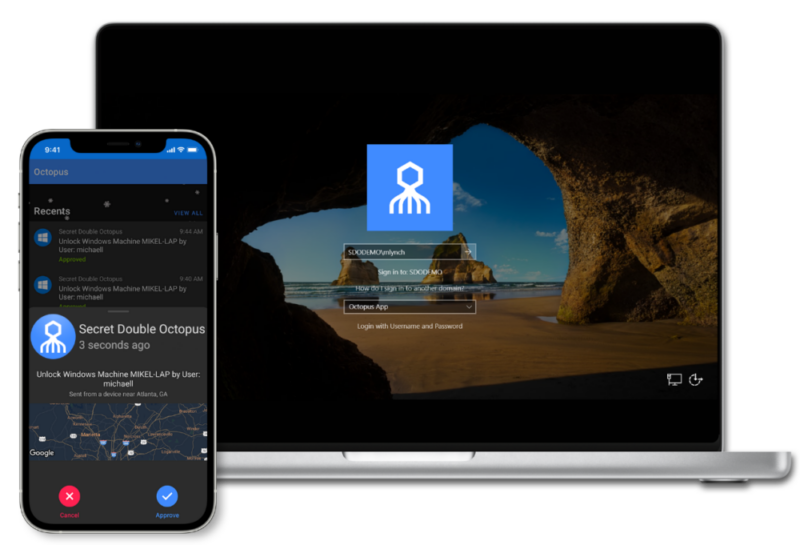
Octopus is a complete MFA platform with the industry’s broadest passwordless authentication coverage across desktop, web and corporate apps, and privileged access. Users love the streamlined workflow of passwordless MFA, and admins thrive on the security and control it gives them.
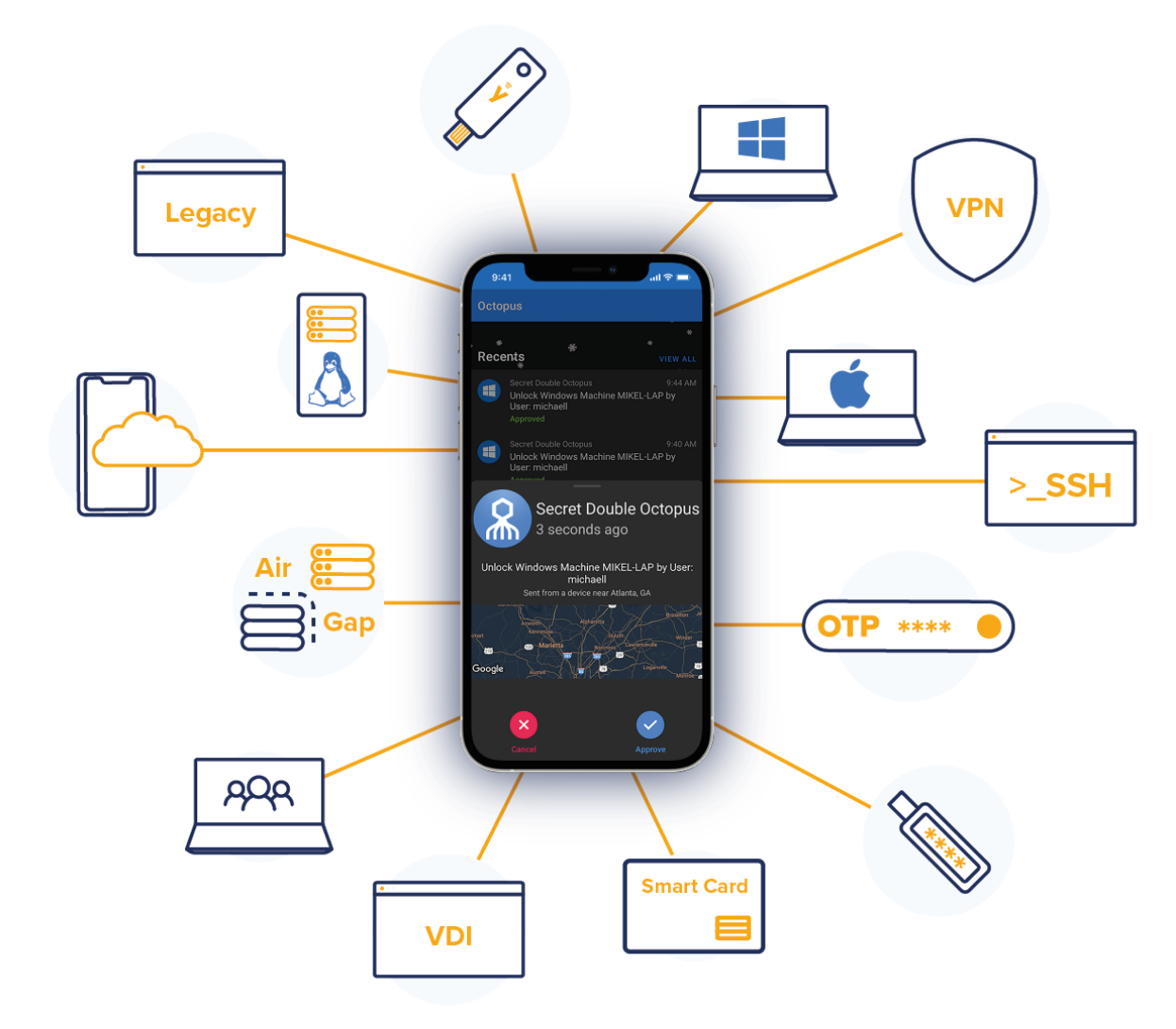
Less risk, less work, less friction, more business returns. IT leaders eliminate the attacker ability to exploit passwords or phish users– without the time, expense, and risks of recoding applications or rearchitecting identity infrastructure that is the hub of business. The Octopus works with modern FIDO2 and SAML apps, and with applications, services, and infrastructure that requires a password.
Less risk, less work, less friction, more business returns. Roll out Octopus Cloud SaaS and start onboarding users in an hour.
LEARN MORE
Passwordless MFA helps the university bolster security and stop phishing, with a better student and faculty experience.
DOWNLOAD CASE STUDY
Put an end to the “MFA fatigue” that comes from creating, remembering, and typing passwords plus OTPs. Give users a simple, streamlined, time-saving phishing-resistant login workflow that matches their needs:

Modernize authentication fast without user secret-sharing coordination, buying down security risk and delighting the workforce:
Unlike partial offerings that only work with web apps, Octopus protects your corporate apps too, including VPN, privileged accesses, and custom business services.
READ MORE
