MFA as we know it can’t protect CI
Industrial manufacturers and providers of critical infrastructure (CI) – utilities, education, healthcare, government, industrial manufacturing – all face massive risk from cyberattacks and mounting pressure to implement Zero Trust security postures. Experts agree a Zero Trust strategy should start with identity, and that stronger identity and access management (IAM) for remote access to critical infrastructure starts with multifactor authentication (MFA) – but most MFA falls short.

MFA as we know it proves easy to intercept, impersonate, and most of all, phish. This blog explains:
- The inherent flaw in most MFA
- CI’s unique challenges
- How IT leaders can avoid the mistakes made by early MFA adopters
- How to implement a solution that achieves less risk in less time
How big is the problem?

What makes CI so popular with attackers?
For years now, manufacturers and other CI providers have been interconnecting operational technology (OT) and IT infrastructures together and connecting OT systems to the Internet for the first time. Attackers take advantage by targeting OT devices that were not designed with security in mind and may not even support the use of passwords to verify identity.
IAM leaders’ challenge gets compounded by attackers’ ability to exploit:
- A lack of centralization, visibility, and cyber skills
- Outdated systems, software, and operating systems (often with unpatched vulnerabilities)
- Overreliance on outsourcing security
- Third-party supply chains exposure to foreign and nation-state attacks
Compromised credentials pave the way for security breaches
In one high-profile breach at a US water treatment plant, hackers used compromised passwords to access dormant or under-protected systems. The attacker used stolen employee credentials to enter the plant’s network remotely and began manipulating systems used to control water quality. Sadly (and as is all too common), the same password also granted the hacker access to multiple systems.

CI’s urgent challenge: a push to secure remote access
Like OT/IT convergence, remote access boosts productivity and speeds resolution times (fewer centralized techs being dispatched to remote sites). But increased digitalization creates a fluid, fast-growing attack surface that increasingly gets accessed by remote workers and supplier technicians.
Without strong authentication and authorization controls, remote access compounds risk, but making login workflows overly complex leads technicians to devise dangerous workarounds that contribute to shadow IT (and shadow OT). MFA needs to go everywhere remote workers, vendors, and suppliers go, and offer 100% assurance that those attempting to access shop floors, public utility infrastructures, and other air-gapped industrial environments are who they say they are.
Digital solutions don’t work in air gap environments
Manufacturing production floors, laboratories, unmanned warehouses, public utilities, and other industrial environments also may operate air gapped or physically isolated environments that house vital systems and data in spaces that, for security reasons, cannot be connected to the Internet at all. Air gapped facilities often include legacy equipment that may not easily be modified to support MFA and other security controls.
Mounting risk leads to massive regulation
Governments worldwide continue to step up regulations around cybersecurity with many calling for adoption of Zero Trust best practices built around not only MFA, but phishing-resistant MFA. The National Institute for Standards and Technologies (NIST) 800-171 targeting supply chain risk says companies must use MFA to secure local and network/remote access for all privileged accounts — and for networked/remote access for non-privileged accounts as well.
Articles 1.12 and 1.14 further require companies to centralize and be able to audit remote access by employees, contractors, technicians, and other third parties maintaining machines on production floors. Similarly, NIST 800-63 takes aim at phishing by prescribing authentication strategies that resist social engineering and attacks on MFA itself, such as push bombing, SIM swapping, and hijacking SMS.
Following guidelines from federal agencies like the Cybersecurity Infrastructure & Security Agency (CISA) and frameworks like MITRE ATT&CK, companies have begun looking for a better, more compliant, and extensible approach to MFA — one that finally puts an end to phishing.
What’s ‘wrong’ with most MFA?
In a word, passwords. Traditional MFA builds upon a foundation of passwords as the first factor of identity verification. Passwords represent secrets that, in theory, only users know. From there, MFA sends a prompt asking users to do take additional steps to verify identity:
- Enter a code or PIN sent via text or email
- Click to approve or OK a request to access resources
- Provide biometric information (for example, pressing their thumbprint to the screen)
- Insert a physical token or chip/smart card
Adding multiple steps should, and does, significantly improve confidence but not to the degree required to secure CI or any industry targeted by motivated threat actor groups with deep pockets.
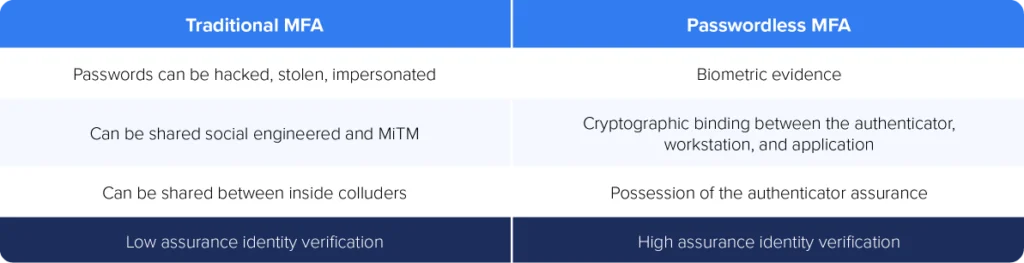
Passwords can be lost, leaked, bought, or stolen—and phished
The data says it all: 90% of successful cyberattacks start with phishing according to CISA’s Shields Up campaign.
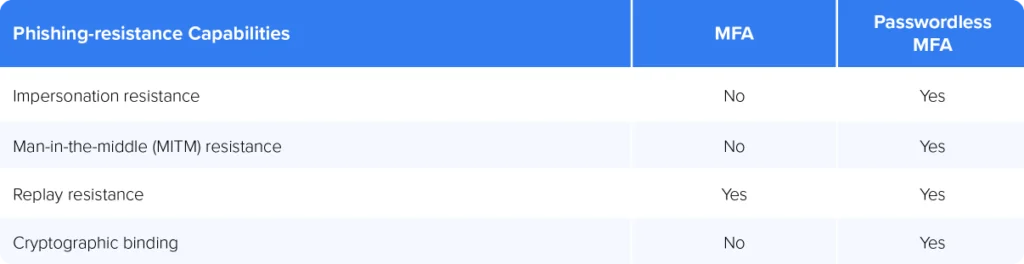
Octopus Passwordless MFA meets CI’s unique needs
A passwordless approach to MFA provides a better solution for strong, phishing-resistant authentication. By taking hackers’ favorite threat vector—vulnerable user-managed ‘secrets’—out of the login process, passwordless MFA stops phishing and the nasty things that follow, including lateral movement, ransomware, account takeover, data exfiltration.
Without user passwords, there’s nothing to phish. For this reason, the Secret Double Octopus Passwordless MFA platform takes “what users know” out of the equation in favor of two stronger pillars of authentication:
- Who or what users are confirmed via biometrics (facial, fingerprint, voice recognition)
- What users have like hardware tokens, smartcards, and the right smartphone or laptop
Octopus introduces three distinct advantages for CI environments
The SDO passwordless MFA solution provides Zero Trust Identity that catches and avoids more threats than other MFA, and even regular passwordless MFA approaches. SDO offers three benefits OT/IT security leaders should look for in evaluating IAM solutions.
Broad use case coverage and flexible authentication options
FIDO2-based passwordless MFA solutions get a lot of press but only work for web-based applications. The Secret Double Octopus Passwordless MFA Authentication Platform provides a FIDO2-based solution but also includes mechanisms for addressing vital non-Web applications as well as custom applications and legacy systems often found in industrial environments.
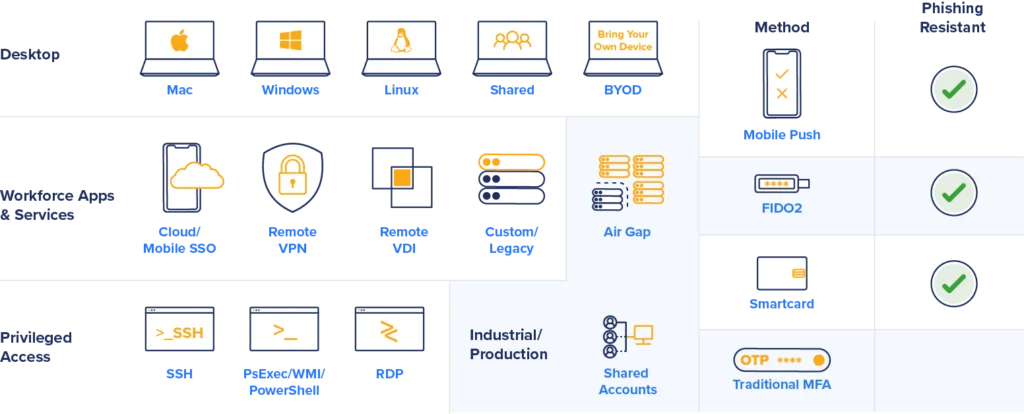
For high-security government environments, Octopus also supports high-assurance authenticators such as X.509 certificate smartcards and PIV badges with smartcard readers.
Octopus also adds cryptographic technology that binds, or pins, the authentication application directly to the user and application.
No change required to backend infrastructure, no delays to implementation
Many passwordless MFA approaches require applications to be recoded and directories rearchitected to support public key cryptography technologies—a Herculean effort that can take years to complete for one single application. Unlike these solutions, SDO extends coverage to password-centric applications by de-coupling the user log-in process from back-end directory management and replacing passwords on the back end with ephemeral tokens—that cannot be stolen or intercepted—used to authenticate into directories.
IT avoids having to retool apps and directories before rolling out passwordless MFA to users. Onboarding can begin within an hour and coverage extended to every application within hours and days instead of months and years (or worst case, not at all).
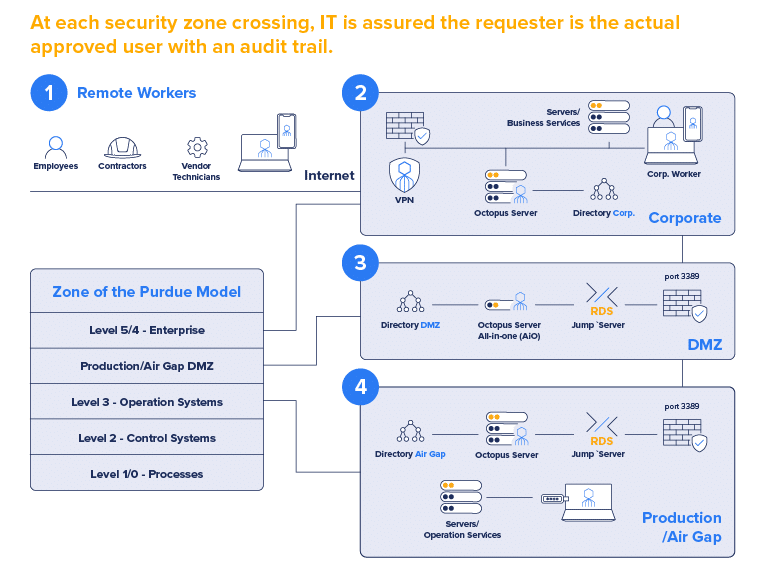
Secure remote access to air-gapped critical infrastructure
Octopus MFA allows technicians and vendors to authenticate into secure enclaves either onsite or remotely. User progress through the typical corporate infrastructure, shown here as layers 4 and 5 of the Purdue Model for securing industrial control systems (ICS), then continue on, providing proof of identity every step of the way.
For a step-by-step example, check out our eBook, Secure Access to Industrial Critical Infrastructure.
Unified MFA changes the business case for CI
The Octopus platform creates an ideal MFA solution for strong, highly flexible authentication (AuthN) that fits the diverse requirements of challenging CI environments without creating MFA fatigue or adding new risk.

Octopus lets IT and OT cybersecurity leaders offer a single, unified login workflow to all onsite and remote workers that makes organizations safer and improves the user experience. Octopus also improves the business case for MFA and Zero Trust Identity by saving companies millions per year in IT overhead, Help Desk support, lost worker productivity, risk avoidance, and cyber-insurance premiums – a rare win-win-win for most organizations.
To learn more, download the eBook here.