Mobile push is the workforce user’s favorite type of MFA. At its best, it streamlines user access, confirming a second factor of what you have out-of-band from the web apps, corporate apps, or desktops being accessed. At its worst, this convenient mechanism is an easy path for attackers to trick us into helping hackers breach our corporate defenses. This is because push MFA’s weakness is people; human nature. Infuriating push bombing attacks flood unsuspecting victims with fraudulent requests, and when the user complies, it wipes out any security gains we hoped to gain from MFA.
What is MFA Push Bombing Attacks
Push bombing is a targeted MFA fatigue attack in which an aggressor triggers multiple login attempts against the target’s SSO portal or publically exposed corporate apps and services. Push bombing is used with phished, stolen, or leaked passwords against traditional MFA (password + second factor). If the attacker can get physical access, e.g., while you are out to lunch, even desktops are vulnerable. Once the attacker has typed in the first factor, the username, and password, then the attacker just needs the worker to accept the second factor delivered to their smartphone to get entry to the victim’s resources.
Push bombing works because workers access many different applications and have to re-authenticate into applications and desktops numerous times daily. This repetition creates muscle memory that can cause users to approve an errant push. Or, as the word bomb implies, attackers send continuous requests. Frustration exacerbates the user’s patience, driving them to click, assuming a technical glitch so they can get back to meeting deadlines.
Many MFA offerings cannot spot even the most blatant bombing attempts, especially where IAM login hygiene controls are lacking.
For advanced intruders looking for persistence, the next step is to change account credentials or MFA profiles for an account takeover as a jumping-off point for lateral movement toward more rewarding business assets.
Attackers love exploiting push because it works (ask recent Goliath victims Cisco and Uber). But what draws attackers to this technique is that it’s easy. In many cases, no malware or man-in-the-middle (MITM) phishing infrastructure is required for it to work. Attackers flow like water down the paths of least resistance.
How the Push Bomb Attack Works
Push bombing attacks can be simple attacks against an employee for a quick grab. However, these attacks are often entry points for a targeted attack against the victim’s employer or upward in the supply chain to larger enterprise customers. The attack is documented in Mitre ATT&CK Framework as T1621 – Multi-Factor Authentication Request Generation – and is generally executed in five parts:
- Reconnaissance: The attacker researches target workflow and publicly exposed resources.
- Credential Access: The attacker acquires the target’s credentials through phishing, password cracking, or the dark web.
- Initial Access: The attacker initiates access requests to exposed victims’ resources, triggering repeated push notifications to the victim with the intent to trick them. (through fake IT help desk calls saying, “We need you to approve that request”) or exacerbate the target into approving the second-factor acknowledgment accidentally or out of frustration
- Lateral Movement: The attacker graduates to an intruder status and, in many cases, moves laterally through the gooey enterprise’s interior toward more valuable assets.
- Impact: The intruder detonates ransomware payloads, exfiltrates data, or installs back doors to add to the Initial Access Broker property pool.
How to Stop Push Bombing Attacks
Stopping push-bombing attacks can be accomplished by combining user education and hardened MFA technologies.
User Education: Worker awareness of social engineering attacks like push bombing is essential to reducing the likelihood of attackers’ success. However, workers are people. For non-security personnel, security comes second, or even further down the priority ranking after getting their jobs done.
Awareness education has limits as demonstrated in the KnowBe4 annual phishing reports: After 12 months of intensive phishing training, 5% of 9.5 million people from 30,100 organizations still clicked the bait. And this year’s results mirror prior reports.
Technology plays a critical role in stopping push bombing.
Adaptive MFA techniques: User experience is essential for successful MFA programs. Forcing draconian hurdles builds user discontent, which isn’t good for the IT admins or management.
Adaptive MFA adds intelligence to traditional MFA workflows to combat anonymous indicators. On detection, the MFA platform presents users with aids and forces additional steps to the login workflow. These include:
- Originating request geolocation
- OTPs on the app for manual entry into the accessed service prompt
- Request frequency and interval policy violation action to slow and lockout push bombers
These adaptive techniques increase the user’s ability to protect the company’s resources. However, they have limits. For example, IP address geolocation can be error-prone due to inaccuracies introduced by VPN, TOR, and mobile infrastructure. Second, any errant accepts, even after the OTP and geo warning messages, results in attacker success.
Phishing-resistant MFA techniques: The newest development against push bombing is phishing-resistant MFA. This technology attempts to remove user weaknesses from phishing-related attacks.
Phishing-resistant MFA uses pinning techniques that bind users, workstations, and browsers to their assigned applications and services. Phishing-resistant MFA typically uses hardware tokens like X.509 smart cards and USB keys or FIDO2 hardware tokens to make unauthorized access impossible without possessing the tokens.
How the Secret Double Octopus Combats Push Bombing Attacks
Moving to a modern strong authentication-enabled MFA platform is the most complete way to protect employees from all types of phishing and push-bombing MFA attacks.
Passwordless MFA: The Octopus platform’s ability to relieve users from creating or remembering any of their workplace passwords removes the most severe password phishing risk. The phishing-resistant passwordless MFA push workflow enables a seamless user experience to access devices and services.
Passwordless MFA raises the stakes by eliminating passwords, something you know in favor of something you are. This simple change offers the benefits of a fast return on investment (ROI) in several ways.
First, it slashes the attack surface. On the business side, higher ROI comes from users saving time and becoming more productive without password login overhead. We all experience this when we reminisce about the bad old days of fingering 6-digit codes every time we used our iPhone 5.
More interesting is that while users love passwordless MFA, IT is the big winner. IT immediately buys down security risk and stops time-draining password helpdesk calls. Not to mention, IT can modernize infrastructure faster without user secret sharing coordination.
Adaptive MFA: The Octopus supports escalating AuthN in response to unusual access request interaction with the Octopus Server by monitoring requester geolocation, devices used for access, browser cookies, and access patterns that indicate nefarious activity, such as push bombing.
The Octopus escalation mechanisms include:
- Simple accept only push for low-risk accesses
- Present requesting source geolocation
- Force user biometric
- Initiate verified push (additional OTP code required)
- Enforce increasing duration timeouts
- Account lockout
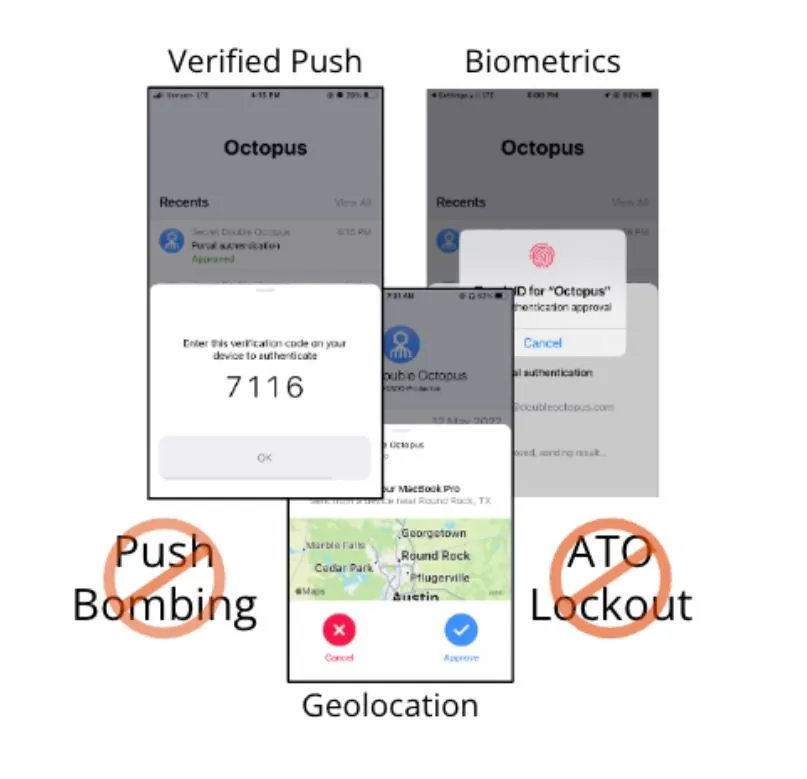
Phishing-Resistant MFA: The Octopus supports multiple phishing-resistant MFA modes that let businesses choose to use hardware-based FIDO2 tokens or SDO’s tokenless Desktop-to-App pinning for mobile push MFA. Both technologies leverage public and private key pinning through signed challenge and response protected in the FIDO or Desktop TPM vault.

Conclusion
Attackers innovate, so your enterprise identity workflows need to modernize authentication to stop the push-bomb menace.
But change is hard for successful businesses built on password identity infrastructure. Unlike certificate-based passwordless alternatives, the SDO passwordless MFA solution does not require you to build up PKI issuing infrastructure or modify directories before getting users off passwords. Instead, we integrate with all leading directories and access management solutions without interrupting existing identity workflows. As a result, you achieve security resilience faster while improving user experience and lowering operating costs while modernizing infrastructure without secret user coordination.
Learn more about the Octopus Platform
Watch the full webinar on-demand, 5 Ways Passwordless MFA Stops Modern Phishing and MFA Attacks, or book a demo to learn more today.