While modern Identity and Access Management solutions are continuously becoming more sophisticated and provide many ways to address users’ rights and privileges, many organizations are still highly dependant on shared credentials to access privileged or administrative accounts.
These shared resources can be found on almost any platform or application, from email accounts to security tools, servers, and databases.
An organization may end up using shared accounts for a variety of reasons, with some tools leaving no other option to keep things running smoothly. Regardless of the reason, shared accounts naturally expose the organization’s network and data to multiple risks.
Activity Tracking and Visibility
To really achieve access visibility and track activity on an online platform, administrators first need to know which users are accessing it and when. Shared accounts create a major gap in this regard. If a shared account is breached for instance, knowing which user was logged in at the time is a big part of investigating the incident and understanding the attack.
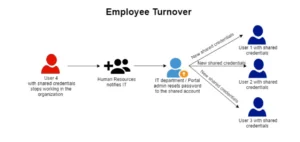
Credentials Compromise due to Employee Turnover
The reality for most businesses is that employees join, leave and move around within the organization. Changing credentials or account permissions every time a user joins or leaves is complicated, costly, and worst of all – leaves a lot of room for human error. A recent prosecution by the U.S. Department of Justice highlighted this risk all too clearly – according to reports, a former analyst at an autism treatment center in Tennessee likely used shared credentials when he illicitly accessed patient databases at his former place of employment.
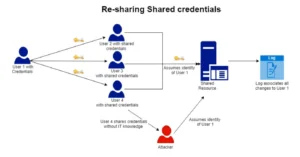
Shared Credentials can be Re-Shared:
Clearly, once an administrator gives access to a user, that user can freely share their credentials with anyone. Not knowing who holds which credentials is an IT nightmare, especially when dealing with administrator or other privileged accounts. Credentials falling into the wrong hands can easily give privileged access to an attacker which could lead to numerous attacks, most notably in this case – Corporate Account Takeover (CATO).
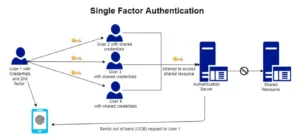
One factor authentication :
Additionally, shared credentials make it hard to apply Multi-Factor Authentication (MFA) to an account. Second factors such as SMS, OTP, or push notifications tend to be bound to one particular user since only one user can carry the Out Of Band (OOB) device – be it a cellphone or a hardware token – necessary for authentication.
The two options organizations think they have
The problem of securing shared accounts have not gone unnoticed. While organizations try to keep track of who holds which credentials using band-aid solutions, the industry has produced two primary types of solutions:
-
Password managers
Password managers allow users to share passwords without revealing the actual credentials. This sounds ideal but the passwords still need to be transmitted, which means they become vulnerable to capture by hackers via man-in-the-middle attacks (MITM) or other data interception methods. As an industry leader in password sharing warned (in their own user-guide no less) “savvy end users could potentially access the password” in transit by capturing it “using advanced techniques”. Needless to say, hackers are very much aware of this.
-
Privileged Access Management (PAM) solutions
PAM solutions provide scrupulous monitoring over shared accounts and present the highest level of identity security and auditing. But these tools tend to be expensive to purchase and deploy, ranging between $80 – $300 per machine, and are usually used only on accounts with access to critical systems. While PAM solutions solve the problem of shared accounts, they carry a significant total cost of ownership and ongoing IT resources.
Securing Privileged and shared accounts with Secret Double Octopus
The unique challenge of securing shared accounts has been a constant worry for IT managers and security experts for years. Traditional ways of protecting employees accounts, such as multi-factor authentication (MFA) and physical security tokens, never delivered a highly secure yet user-friendly solution for this specific business need. Now, with a technology built precisely for the needs of the modern and versatile enterprise, Secret Double Octopus’s Passwordless Authentication offers unparalleled security for shared accounts.
Deploying Octopus Authentication on shared accounts allows for:
- Fast and easy Multi-Factor Authentication: Adding extra layers of security to access shared accounts with our passwordless MFA minimizes the risk of all major user-side and man-in-the-middle attacks, making credential-theft virtually impossible.
- Centralized approach: Secret Double Octopus’s admin panel gives administrators a “one-stop shop” to manage access to shared accounts, allowing users to be added and removed upon need. Shared accounts can be added at a group level making enrollment a seamless, and easy process
- Employee turnover: When employees leave, their access to the shared account is completely revoked. Removing a user means removing access from all resources, not just the ones personally associated with the user.
- Re-Sharing is prevented: Moving beyond single-factor authentication that relies on passwords means credentials cannot be shared. This frees IT from worrying about who might access shared accounts and when, as only they hold the power to grant shared access.
Shoring Up the Network, Reaping the Benefits
Securing shared accounts allows companies to take advantage of all the logistical benefits of mutually used credentials without worrying about the risks. Octopus’s high-assurance solution breaks the trade-off between security and usability, meaning that organizations no longer have to compromise on security to maximize workflow and efficiency.