Cybersecurity leaders at financial services companies have their work cut out for them – M&As, changing regulations, ongoing transformation, and the endless stream of threats levied by modern cyber criminals. No news there. What is somewhat surprising is that, in 2024, very few available technologies solve problems on all fronts. Multi-factor authentication (MFA) represents one exception in that it’s able to:
- Avoid cyber risk from phishing, ransomware, and account takeover (ATO)
- Speed the consolidation of workforces throughout M&As
- Move a company closer to Zero Trust best practices and uphold compliance
- Save everybody – users, IT, and security teams – a ton effort, time, and aggravation while saving the business millions of dollars every year
What makes MFA suddenly so valuable?
Experts have declared identity the “new perimeter” of modern cybersecurity defenses and MFA a key strategy in improving identity verification. MFA aims to stop phishing and credential abuse that leads to malware, ransomware, data leaks, supply chain and insider threats.
US NIST, CISA, MITRE ATT&CK all tout the importance of MFA to a zero trust philosophy, but readily acknowledge . . .
MFA as we know it falls short
MFA strengthens identify verification versus relying on passwords alone, but most solutions keep passwords as the first factor of authentication. That renders MFA far less valuable than expected.
A passwordless approach takes away attackers’ favorite tool—phishing—while increasing confidence that the person attempting to log in is a legitimate user looking to do only legitimate things. Getting rid of passwords (which represent “something users know”) and incorporating stronger pillars of identity verification — like something users have and something users “are” — eliminates most risk from impersonation and social engineering as well as:
- The 80+% of breaches that involve compromised credentials
- Phishing, modern phishing-as-a-service (PhaaS) and man in the middle (MITM) attacks
- All doubt that those responsible for security did everything possible to avoid credential compromise abuse of trust
But for passwordless to work, financial services organizations must extend secure login to every member of the workforce and every application, from any device or location.
Sound hard?
It doesn’t have to be. Our new ebook, Five Ways Financial Services IT Leaders Use MFA to End the “Identity Crisis”, shows how passwordless MFA can be much easier than it sounds.
Before we summarize that, let’s recap how passwordless MFA solves three of financial service IT leaders’ biggest challenges:
MFA Makes M&As Go Faster
A succession of mergers creates a gnarly mass of fragmented identities and login workflows. Workforce consolidation is as good a time as any to centralize and standardize around a single unified login and streamlined mechanism to access apps and infrastructure. But how?
Two approaches to consolidating MFA
Merging companies may use multiple IAM solutions like Okta, Ping, and Azure to access applications and Active Directory to manage identities on the back end. Standardizing on one approach eliminates disjointed workflows that give rise to visibility gaps, a frustrating user experience, and complex audit trails.
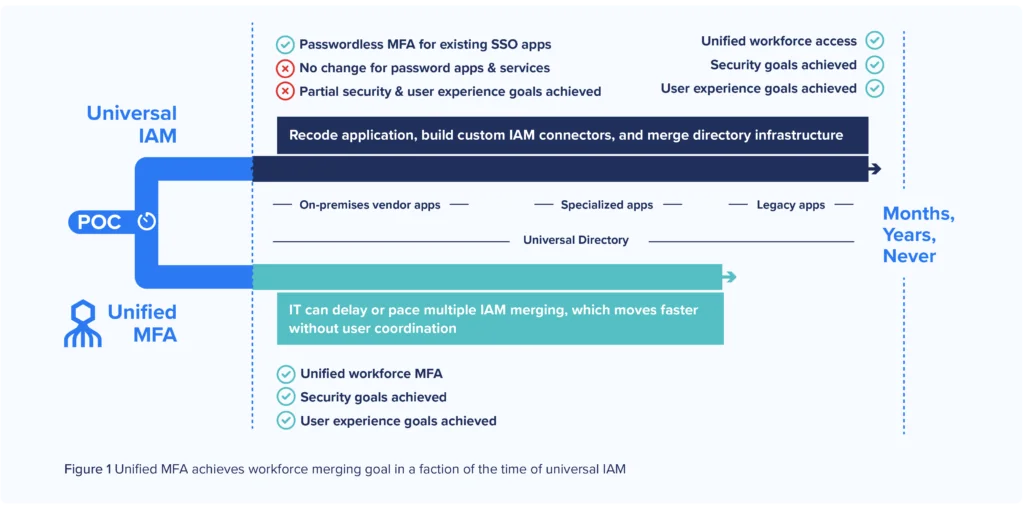
Option 1. Universal IAM
Large IAM vendors propose a “universal IAM” approach: transitioning all users, applications, directories, and identity infrastructures to their one IAM platform. The “universal IAM” approach sounds simpler in theory but phased migrations can take months, years, or never get completed at all. IT may need to recode applications to support the vendor’s single sign-on (SSO) and FIDO2 technology — no small feat since retooling a single application to work with a new IAM takes 5-7 days, best-case scenario.
Option 2. Unified MFA
Secret Double Octopus delivers the same security benefits and streamlined user experience, only faster. Migrating the MFA portion of the login process to the Octopus platform adds a flexible passwordless authentication layer that works with any existing IAM platforms. IT can migrate users without recoding applications or directories.

Modern Security for Legacy Apps
The banking industry’s heightened focus on protecting customer data leads financial services institutions to store privileged data onsite instead of migrating to public cloud services. Storing data on legacy server infrastructures, and even some old mainframe computers within data centers may be safer, but maintaining older systems brings its own challenges.
And needless to say, the talent pool of experts versed in older technologies shrinks every year and companies hesitate to disrupt complex infrastructures that predate the current team.
“On-prem” doesn’t always mean “old”
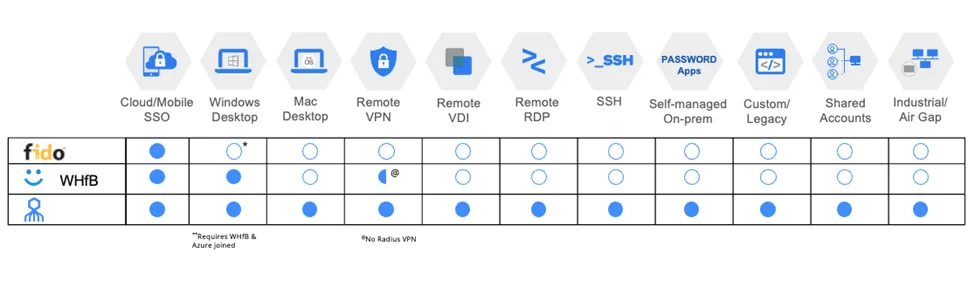
Bloomberg reported that 54% of all new applications are being deployed locally1 versus in the cloud. While doubling down on data center operations, companies must find new ways to strike the balance between digitalization, security, and user experience — a formidable challenge since most IAM strategies, and even most MFA solutions, heavily target cloud and Web-based applications.
Financial companies’ workforces typically support a range of Windows, Macs, Linux, legacy and custom systems. Windows Hello for Business (WHfB) only works with some-not-all Windows platforms. FIDO2 technology only work with web-based resources. Partial use case coverage leaves enterprises at a loss to deliver a secure, unified high-assurance login for all remote and local users.
Octopus upholds a legacy of trust
Octopus Passwordless MFA delivers three essential advantages:
- A safe, simple, unified login everywhere, anytime from desktops, on-premises apps, and the cloud
- Complete use case coverage to stop phishing
- Achieves Zero Trust identity
Octopus provides enterprise-wide use case coverage for on-prem, remote and cloud applications. All applications can be migrated quickly and easily instead of one-by-one so companies growing by acquisition can quickly integrate new workforces and tighten controls as they go.
The CISO’s new dilemma: “Did we do enough?”
Ninety percent (90%) of data breaches still start with a phish and about 90% of MFA solutions can’t stop phishing. Following a breach, penalties (and next year’s insurance premiums) may hinge on subjective assessments of whether security leaders did enough to stop it from happening.
One definitive doctrine, the NIST 800-63 (Digital Identity Guideline) spells out requirements for high assurance MFA based on the potential harm a failed authentication might cause to an organization and its stakeholders. The Octopus platform delivers AAL3-compliant identity verification for high-assurance, phishing-resistant MFA for highly regulated industries.
| Impact of failed authentication | Maximum impact to safety | Acceptable authentication methods | |
|---|---|---|---|
| AAL1 | Low | None possible | Username & password SMS/email OTP MFA |
| AAL2 | Moderate | Low | Mobile push notifications OTP tokens |
| AAL3 | High | Moderate or high | High assurance authentication |
Adopting passwordless MFA helps make the case that companies did everything in their power to prevent and neutralize attacks based on compromised credentials and identities. Continuing to use passwords clearly proves they did not.
High-Assurance MFA Makes Dollars and Sense
Every industry will eventually adopt a phishing-resistant, passwordless approach to MFA but financial services companies will likely be early adopters — and early beneficiaries as:
- Passwordless MFA pays for itself in the first year
- Phishing-resistance eliminates 80%+ of risk
- Employees become 5% more productive
- IT avoids up to 40% of all Help Desk calls
Choosing the ideal solution
Read the eBook for a quick checklist of questions to ask in evaluating the ideal MFA solution for your company.