What is passwordless authentication?

Passwordless authentication equips users to reliably verify their identity — without using passwords — before logging into or accessing a particular resource. As we’ll see below, a variety of methods can be used to achieve and complete passwordless identity verification.
What Is the Difference Between Passwordless and “Regular” MFA?
Yes and no. With or without passwords, multi-factor authentication (MFA) aims to verify user identity during the login process. In that sense, password MFA is a form of password authentication. The broader topic of authentication might include other options, such as single sign-on (SSO), which can also be passwordless if the SSO solution never requires users to enter passwords at all.
What are the goals of passwordless authentication?
Companies adopt passwordless login for two reasons: to strengthen their cybersecurity posture against security attacks and to improve the quality of users’ login experience. In particular, passwordless MFA stops hard-to-detect phishing attacks that might include credential stuffing, quishing (phishing that involves QR codes), vishing (phishing that involves voice messages), man-in-the-middle (MITM) attacks, SIM swapping, and push-bombing or MFA fatigue attacks that exploit users’ frustrations with overly complicated login workflows.
The risks of continuing to use passwords to authenticate users
IBM’s definitive Cost of a Data Breach Report 2024 found that, for the 2nd year in a row, phishing and stolen or compromised credentials were the 2 most prevalent attack vectors. Once threat actors use social engineering and phishing attacks to scam a set of working credentials — or simply purchase them on the dark web — the potential to wreak havoc becomes rather terrifying.
Once inside your network, stealthy would-be attackers work their way toward your company’s ‘crown-jewel’ assets and privileged data, potentially putting your brand reputation, customers, and supply chain at risk. They might also look for a quick payday or to strike a malevolent blow by deploying ransomware or stealing and then exposing or selling your privileged data on the black market.
How passwordless authentication improves user experience (UX)
Simple. Entering too many passwords all day long wastes time. Entering passwords becomes repetitive, and in turn, boring and annoying. That creates friction.
On top of the frustration and lost productivity, asking users to create, remember, and juggle multiple passwords adds risk. Many users admit to maintaining the same set of credentials to log into multiple resources, a notoriously bad practice known as ‘password reuse’ that exponentially increases the odds that a user will inadvertently reveal a password to potential hackers.
On the other hand, maintaining different sets of credentials and following various login sequences for accessing web and cloud apps, on-prem custom or legacy systems, and specialized environments like physically isolated airgaps gets to be too much. One study from BBC found the workforce spends up to 22 minutes, or 5% of a typical workday, interacting with technology, basically logging in and out of things. That adds up!
Beyond that, requirements to rotate passwords regularly and use different devices like physical hardware tokens and passkeys and smartcards create more work, cost and confusion. The same goes for creating multiple biometric profiles which some users distrust as a violation of personal privacy.
Any resistance by users dramatically increases the risk of someone making a mistake or bad judgment call that exposes your company to risk along the way. Done right (and once you get past the initial onboarding effort), replacing passwords with a single unified passwordless authentication experience makes 90+% of users’ frustration with logging into applications go away.
Key Benefits of Passwordless Authentication for Businesses
Passwordless slashes the attack surface by 82%, makes people 5% more effective, and pays measurable business dividends. The security gains come from buying down risk 35 times return on investment (ROI) by eliminating the attacker’s ability to exploit passwords or phishing users, the attacker’s favorite tools. On the productivity side, businesses regularly see an 8x ROI from saving users time logging into apps and services throughout the workday, and IT admins eliminate time-consuming password tasks.
AuthN and AuthZ, or authentication and authorization, are the two steps taken to provide users access to classified information and privileged assets. With traditional password-based authentication, user experience dictates that a user only needs to log in once with a password to authorize their credentials, since entering a password multiple times can be cumbersome.
With passwordless, users can authenticate multiple times per session to ensure they are authorized to view the information they’re trying to access. Other benefits of a passwordless approach can be broken into two main categories: business and technical.
Streamlined User Experience for Business:
- User Experience (UX): Passwordless authentication means no more user-memorized secrets; this streamlines the authentication process.
- ROI: Passwords are expensive, and they require constant maintenance from your IT staff. Removing them reduces support tickets and frees IT to deal with real problems, all while contributing to your ROI.

Enhanced Security and Reduced Attack Surface:
- Better security: User-controlled passwords are a major vulnerability because employees reuse passwords and are able to share them with others. Passwords are one of the biggest cyberattack vectors and have been responsible for 81% of breaches (According to Verizon DBIR). They also lead to attacks such as credential stuffing, corporate account takeover (CATO), password spraying, and brute force attacks.
- Invalidates already compromised credentials: Companies may have compromised credentials floating around on the dark web and not even know it. Going passwordless invalidates all these.
Key Technical Operation Benefits:
- Supported on a variety of systems: Passwordless does a good job of integrating with whatever platform you’re already using.
- Decentralized: Because passwordless doesn’t require a master list of passwords or a password manager, it’s decentralized, meaning a breach doesn’t compromise the security of your entire system.
- Advances Zero Trust security posture: Zero Trust is exactly what it sounds like – never trust any user at any time. Maximum security is achieved by constantly authenticating, all without the user even knowing it.
How does passwordless authentication work?
Passwordless MFA, the most common emerging approach to passwordless authentication, works by removing the question of ‘what users know,’ namely the password that they have to create or remember, from the login equation. Instead, the two or more (multiple) steps taken to verify the user’s identity feature ‘something users have,’ like a hardware key or smartphone that’s ‘pinned’ to the authentication app — or — something they ‘are,’ verified with biometrics like fingerprints, voiceprints, or facial/iris recognition that can’t easily be stolen or mimicked.
The most popular and forward-looking passwordless MFA solutions provide flexible options to accommodate the preferences of users and IT, security, and identity and access management (IAM) leaders. Whatever the process, once users complete the steps and satisfy the passwordless authentication platform, they’re presumed trustworthy and granted access to certain devices or resources, whatever they’re authorized to access by IT.
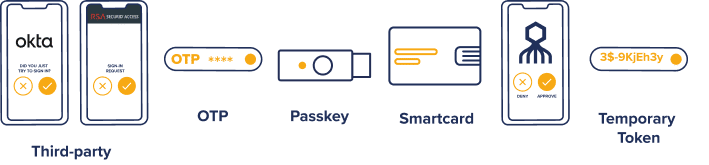
Passwordless authentication methods – a look under the hood
All passwordless technologies are rooted in cryptography based on random numbers and encrypted transmission. In place of passwords, three standard methods can be used to verify identity through the possession of a hardware or software token:
(1) X.509 client-side certificates (e.g., smart cards, US government CAC and PIV badges)
(2) FIDO tokens (synced or device-bound passkeys)
(3) Octopus machine-generated tokens (compatible with password apps and directories)
For every authentication flow, the user’s authenticator must be compatible with what the application and the directory expect. For example, password apps require that a user provide a password to the app that the app will in turn pass to the directory to verify and complete the authentication cycle. Certificates and FIDO work the same way. Though the principles used in these methods are the same, the three cannot be mixed together.
Most applications accept a password by default, and many only support passwords. These password-based apps can be recoded or reconfigured to work with X.509 or FIDO authentication methods, but that requires significant development and retooling efforts.
| Passwordless method | Active Directory | Cloud Directory (Entra, Okta, Ping) |
| Client side certificates | Yes | Yes |
| FIDO | No | Yes |
| Passwords and Octopus Tokens | Yes | Yes |
With the growth of SSO, most commercial SaaS applications can be configured to defer their authentication to an Identity provider (IDP) that can support all three authentication methods. Here again, many enterprise on-prem line-of-business apps and legacy apps do not work with IDP protocols like SAML, OAuth2, and WS-Fed without redesign.

Does the same passwordless MFA work for everything?
This has become, literally, the million-dollar question. The short answer is: it should. Since most phishing attacks target credentials, businesses must eliminate user passwords completely to achieve phishing-resistance. In many industries, organizations (particularly government agencies, utility companies, manufacturers and other providers of ‘critical infrastructure’) must meet formal criteria for attempting to stop phishing to comply with industry and national mandates for protecting data privacy.
The more a single MFA solution can be used to achieve passwordless authentication, the better. A familiar, unified experience makes users’ lives easier and reduces IT efforted required by IT to negotiate and manage licenses, updates, and support contracts from multiple vendors.
To illustrate, we compare FIDO WebAuth support for web apps and Microsoft’s Windows Hello for Business (WHfB) use case coverage compared with Octopus enterprise-wide coverage:
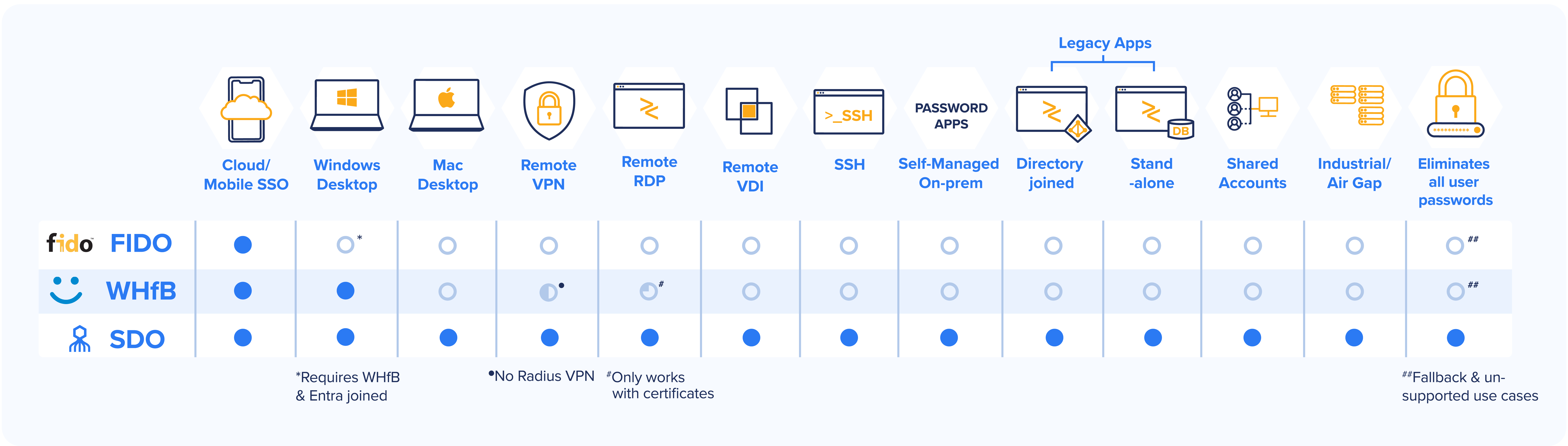
The last column reflects incompatibilities in many enterprise use cases, forcing workers to remember and use their directory passwords with FIDO and WHfB (or similar IAM solutions like Okta and Ping). These systems are only partially passwordless, leaving security risks and user frustration when accessing incompatible services. With the Octopus, users never remember or type passwords accessing every app and service in the enterprise.
Obstacles companies face in adopting passwordless MFA
Everyone seems to know that passwordless MFA is the future of workforce authentication. The ‘why’ is well understood. The questions then become where, when, how much, and how fast. The most common challenges are:
- Achieving complete enterprise-wide coverage for every use case. Octopus passwordless MFA meets this requirement by working with Windows, Macs, Linux, and any custom, on-prem, or legacy application. And, the SDO platform works with all popular authentication options and backend databases. We do this by replacing passwords with machine-generated, one-time-use random tokens used to complete identity verification with Active Directory and other identity databases — without users ever knowing they exist.
- Accelerating onboarding and adoption. Because the Octopus platform works with any app and does not require rearchitecting of identity infrastructure, companies can extend passwordless authentication to users in days or weeks instead of months and years — a massive savings and acceleration of return on investment (ROI). Users only need to learn one authentication workflow to access everything they need, so training goes quickly, and most users report increased satisfaction within just a few weeks.
- MFA may not take top priority. Most security budgets and IAM strategies don’t mature as quickly as today’s AI-powered cyberattacks. But once CISOs, CIOs, and CFOs realize just how much risk they can ‘buy down’ — and how many Help Desk calls they can avoid — by stopping phishing and getting rid of passwords once and for all, projects take on greater urgency. SDO created a Passwordless MFA ROI Calculator that shows how most enterprises save up to $2M in their first year alone.
Octopus delivers the rare trifecta: less risk, less time, less effort
The Octopus platform features a host of enhancements for stopping phishing, MITM attacks, and for achieving high-assurance, AAL3-compliant identity verification. These features all make life better for users and for IT, but the truly unique core appeal of the Octopus is 100% enterprise-wide use case coverage virtually out of the gate.
Architected to work with new technologies and what enterprises already have in place, Octopus handles several important, empowering ‘outlier’ use cases that other companies, even large ones like Okta and Microsoft, can’t address:
- Zero passwords = Zero-trust Identity: users never create, remember, type, or expose passwords
- Close MFA compliance gaps: shared accounts, air gap, remote access, legacy apps
- Compatible with existing enterprise apps and directory services without redesign
- Achieve your security and UX goals in weeks, not years, as with other offering
To learn more about the Octopus platform, read the Octopus Solutions Overview or schedule a demo with our authentication experts to get started right away.
FAQs:
Will the move to a passwordless solution be costly to my organization? Does more secure mean more expensive?
Passwordless authentication is a rare security improvement that makes life easier for users. The security risk reduction and worker and admin productivity gains pay business dividends. Find out how much with the Passwordless MFA ROI calculator.
Is passwordless authentication user-friendly? What type of pushback should I expect?
The majority of corporate employees prefer passwordless technologies because of the ease of use they provide. Solutions such as push notifications, for instance, are revolutionizing authentication by delivering a substantial increase in security and relieving users of the burdens of remembering and securing passwords.
Can passwordless solutions be implemented in a hybrid enterprise (cloud/on-premises)?
Yes. Due to the increase in the integration of on-premises and cloud-based identity management systems, many authentication solutions have adapted themselves to this model.
The Octopus Authenticator has full integration capabilities with network services such as Microsoft’s Active Directory and other cloud platforms, making it a suitable solution for hybrid enterprises.