Can IT check the box for phishing-resistant—and mean it—before compliance mandates kick in?
Critical infrastructure sectors are under assault from cyber threats. The gloves are off, the stakes are high, and the pressure to modernize is strong.
Zero Trust mandates from the Biden administration single out authentication for obvious reasons—most users do it every day, and it’s still way too easy to phish or steals credentials. And truth be told, no one really wants users “managing” passwords anymore.

But how should you go about getting rid of them? Authentication experts at Secret Double Octopus (SDO) developed a Critical Infrastructure Passwordless MFA Buyers Guide to help IT leaders at critical infrastructure providers decide.

Current research shows that while attacks against critical infrastructure are up, only half of the companies surveyed have adopted multi-factor authentication, a critical step in improving security.
The new guide to passwordless multi-factor authentication (MFA) outlines key categories and considerations for evaluating different approaches:
- What are IT’s near- and long-term goals?
- Which services require strong authentication?
- How much does each approach cost?
- What pain will it cause to deploy?
- Is there a viable Plan B?
Aligning Security Objectives with MFA Solutions for Critical Infrastructure
With pressure mounting on all sides—attackers growing more aggressive and regulators and cyber insurance providers growing less patient— goals include:
- Stopping phishing
- Extending strong authentication to air gaps
- Preserving the custom and legacy systems at the heart of the core business
Why passwordless for phishing?
MFA as we know it isn’t secure enough because attackers have commoditized tooling to phish around it. Today, crafty man-in-the-middle (MITM) attacks intercept one-time passcodes (OTPs) and even biometrics used in traditional MFA to gain access to business-critical systems.
Phishing resistance demands strong authentication and that ultimately means passwordless MFA that never requires users to enter passwords. The Guide shows how some solutions claiming to be passwordless actually require passwords periodically. Less often than before, but less is not enough.
Why passwordless for air gaps?
Many critical sector businesses operate invaluable resources within air gap islands or local environments that constrain physical and digital access—i.e., there’s no Internet. Since traditional MFA won’t work without connectivity, many locations use only simple authentication, a “hope nobody notices” approach that’s already proved risky.

The Guide shows how to evaluate MFA platforms based on their ability to support strong authentication inside your air gap islands, both on-premises islands and for remote access by essential workers.
Why passwordless for a legacy?
Heterogeneous legacy infrastructures have evolved over time, with custom applications based on previous-generation languages built by previous generations of developers. These highly specialized, complex systems carry a large technical debt and they work just fine, so it’s no small task to rip them out and start over mainly to stop phishing.
But attackers, regulators, and cyber insurance auditors won’t make allowances for how hard it is to modernize your current workflows. So, the questions become:
- Does a prospective approach to passwordless MFA depend on IT building a new dedicated client-side authentication infrastructure to support FIDO and PKI?
- Does the platform in question support Windows, Macs, Linux, Windows servers, RDP, SSH, VPN, VDI with Radius, LDAP, Kerberos, and other authentication protocols out of the box?
- Will you be ready to check the box for “phishing resistant” across your workforce environment—air gaps and all—right now?
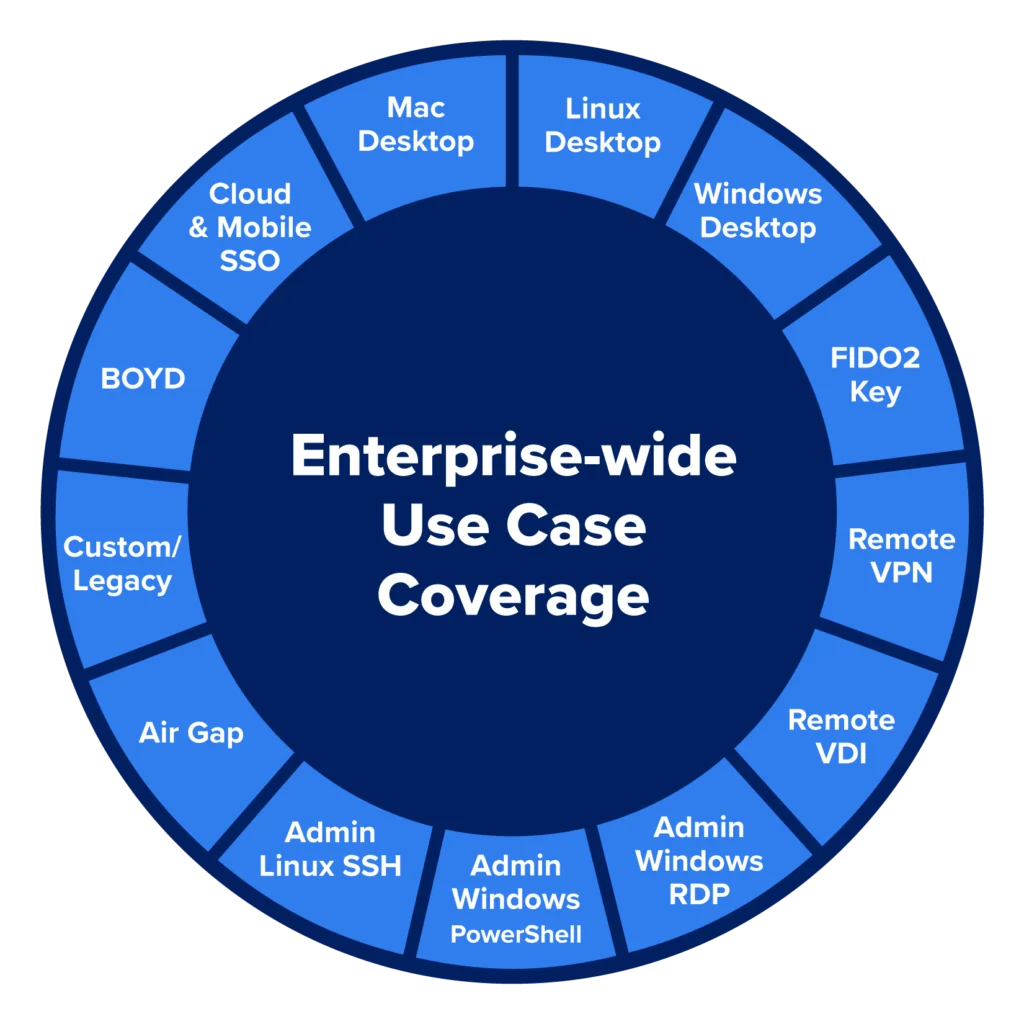
All applications need to offer passwordless user authentication, or you’re not really passwordless.
Securing Remote Access to Critical Infrastructure with MFA
Watch the video below to see how IT leaders can enable unphishable and unsharable biometrics-proven access for essential remote workers into digitally walled-off environments.
We’ve seen the future and the future is PKI
Public Key Infrastructure (PKI) technologies like X.509 certificates or FIDO2-compliant approaches offer a truly passwordless and unfishable means of authentication. But implementing these approaches disrupts operations and creates hybrid login workflows.
And, it takes too long. We have seen organizations take nearly a full year to extend passwordless MFA to a single application using a classic PKI approach. Companies faced with looming deadlines may not have that kind of time, but you don’t want to invest in temporary, soon-to-be-obsolete solutions either.
IT needs a fast path to passwordless MFA today—without obliterating the entire password-centric directory structure—and a realistic path to PKI tomorrow (or whenever IT says “go”).
How much will your passwordless MFA for Critical Infrastructure cost?
The costs of delivering passwordless MFA differ depending on the inner workings of the solution. The guide shows how you can evaluate passwordless solutions for flexibility in supporting hardware and software tokens, managing secrets, integration to web-based SSO and mobile authenticators.
As an example, decades-old X.509 smart cards cost too much and prove too rigid in execution to make sense for most companies in the private sector. Rather than just say “It varies,” SDO developed a Passwordless MFA ROI Calculator IT leaders can use to model costs, savings, and payback based on individual environments and resources.
What pain is involved?
With full migration to PKI, the answer could be quite a bit. The Guide emphasizes compatibility with your existing identity infrastructure. Unless you’re embarking on a greenfield deployment or massive overhaul, the goal should be to minimize operational disruption while meeting mandates and security objectives and laying the groundwork for a smooth migration.
Does the solution include a secure fallback?
Today, all authentication approaches fall back to passwords when something really goes wrong. The user directory entry holds other options for authentication methods, but the password is still required as a backup for lost or broken authenticators and during system failure.
The PKI-driven “Passwordless Everywhere” future stands to change this down the road, but what do you do in the meantime? Who manages the passwords in the event of a disaster? Do users need to find or remember them, or can IT generate and send new ones after verifying identity?
The Guide looks at criteria for identifying the most frictionless and secure strategy for retrieving passwords when things inevitably go wrong.
Weighing the pros and cons
To help IT rank prospective solutions, the Critical Infrastructure Passwordless MFA Buyer’s Guide features a scorecard with a weighted scoring table for ranking the categories most important to your business. Assigning each category a score from 1 to 5 and ranking considerations lets decision-makers identify the solution that best matches your business needs.
Our approach
SDO’s Octopus Authenticator de-couples user-side authentication from the eventual migration of the infrastructure to PKI to create a path that keeps IT in control. Our approach:
- Lets companies check the box on phishing resistance and are phishing-resistant, including MITM attacks
- Creates a fast path to passwordless MFA right now without IT changing password-centric directory infrastructures
- Meets enterprise-wide use cases for office, production, R&D, sales, transport, air gaps, and third-party authentication—no app left behind
- Supports mobile apps, hardware FIDO2 keys, and combinations of OTP and passwords to match the diverse workforce needs

More information
Download the Guide to learn more about Critical Infrastructure Passwordless MFA, and let us know if we can answer any questions.