Passwordless is a subject that every identity and security leader has an opinion about, and from my discussions at Indentiverse Denver, strong views they want to share vigorously.
The word itself is so simple, passwordless. But how people visualize that word’s implication creates differing interpretations, cautionary skepticism, and conjure up minefields of exceptions in their password-centric environments (Active Directory). So rather than debating what is passwordless, it is better to consider the goals of passwordless, which few disagree with.
Imagine taking your workforce out of the password management business, never having to create, remember, type, expose, or rotate passwords. And all this in your Active Directory or other password-centric identity environments. The security and workforce productivity implications pay dividends to your business:
- Slash your attack surface by 82%
- Make your people 5% more effective
- Free up 40% of overburdened Help Desk from password reset tickets
- Bolster resilience by qualifying for cyber insurance with passwordless MFA
As with any forecast based on others’ experiences, your mileage may vary. Without question, eliminating the workforce from password management dramatically reduces security while delighting users, admins, and helpdesk staffers. Better yet, if done right, they gain a streamlined strong authentication workflow to all of their resources: from desktop to VPN, VDI, servers, cloud services, and business-critical custom and legacy apps.
Sounds great; why doesn’t everyone do it? Many identity leaders have started, and so can you (read: State of Workforce Passwordless Authentication Report). So let’s dig deeper into what you should consider while moving to passwordless.
What is Passwordless?
Passwordless authentication is a method of verifying your workforce users’ identities without the use of passwords or any other memorized secret”. Instead of passwords, identity is verified based on a “possession factor”, which is an object that uniquely identifies the user (e.g. a one-time password generator, a registered mobile device, a hardware token, or PKI certificate) and an “inherent factor” like a person’s biometric signature (e.g. fingerprint, face, retina, etc.). “
However, the aspiration statement above on what you get works better to test the good vs. bad and measure the completeness of achieving the passwordless objectives.
Passwordless Goal: Your workforce never having to create, remember, type, expose, or rotate passwords.
Is MFA Enough?
Multifactor authentication (MFA) is the 2000s response to strengthening the password, but MFA has proven to be exploitable and also made the user experience more complicated: Traditional MFA requires entering passwords and then adds additional factors to the workflow.
While MFA strengthens password-based authentication, the hacking industries and tooling innovators thrive thwarting MFA or evade MFA. Roger Grimm’s book Hacking Multifactor Authentication and Kevin Mitnick’s YouTube videos are frightening, yet entertaining, starting points that give you a sense of where the tit-for-tat battlelines stand today.
Although MFA industry-wide adoption is growing (79%), gaps in implementation persist, e.g. desktop, VPN, VDI, and custom or legacy apps, in spite of regulatory mandates applied to almost every industry. Cyber insurance has jumped on too and will likely add additional requirements to ensure they maintain their profits.
MFA ⍯ Your workforce never having to create, remember, type, expose, or rotate passwords
Less Typing Passwords But Still Passwords
Some authentication technologies reduce the number of times users have to log in with passwords that feel passwordless like but still require the user to remember secrets. Internally here at SDO, we call these “passwordless experience” workflows.
Single sign-on (SSO) is the most visible less typed password technology, particularly useful for web-based SaaS applications. SSO is typically enabled through Security Assertion Markup Language (SAML) integration with an Identity Service Provider (IDP, e.g., Azure AD, ForgeRock, etc.) along with a prebuilt web-app federation to the IDP.
SSO has improved workers’ experience, making task switching through multiple applications from their tiled browser portal page. However, the first authentication to the federated eco-system and subsequent token timeout requires password-based login, and less frequently used passwords are the most dangerous passwords. Dangerous because people write them down, make them easy to remember, and often reuse the simple ones across personal and non-federated sites.
Microsoft Window Hello for Business (WHfB) and Apple’s Touch ID are other examples of what people call passwordless but are actually “most of the time passwordless.” WHfB binds pins and/or biometrics (when available) to the user, whereas Mac uses biometrics exclusively. Both systems use these strategies as the primary way to authenticate the user’s access to the desktop.
However, these technologies have passwords behind the scenes on the desktop and in the workforce directory (e.g., AD) that the user must remember. You can see when the system demands the password be entered during infrequent but required tasks, e.g., after reset, admin tasks, AD rotation policy cycles, etc.).
Less passwords ⍯ Your workforce never having to create, remember, type, expose, or rotate passwords.
Some Passwordless Workflows, Some Not
Related to the SSO and WHfB example above, another authentication category is passwordless technology that is passwordless for some but not all workflows. This type of passwordless technology relies on an authentication method that is not ubiquitous to the whole enterprise authentication infrastructure, leaving some commonly used workforce tasks requiring password entry workflows with or without MFA. These multi-workflow authentication models are disruptive to workers, solving some problems while making others even more disruptive. As stated before, less frequently used passwords are the most dangerous passwords.
The most common example of a “some passwordless workflow, some not” implementation is using signed certificates with public key infrastructure (PKI) for authentication. Neither certificate nor PKI is new; we use them daily for browsing, digital signing, and encrypting our data. However, enterprise workforce workflows are complex, with many applications, networking, and data services are not built to support certificate authentication exclusively, or no PKI infrastructure exists for authentication usage.
Better to give you a visual example than spend another thousand words detailing why certificates create workforce authentication workflow gaps. Let’s present a use case comparison:
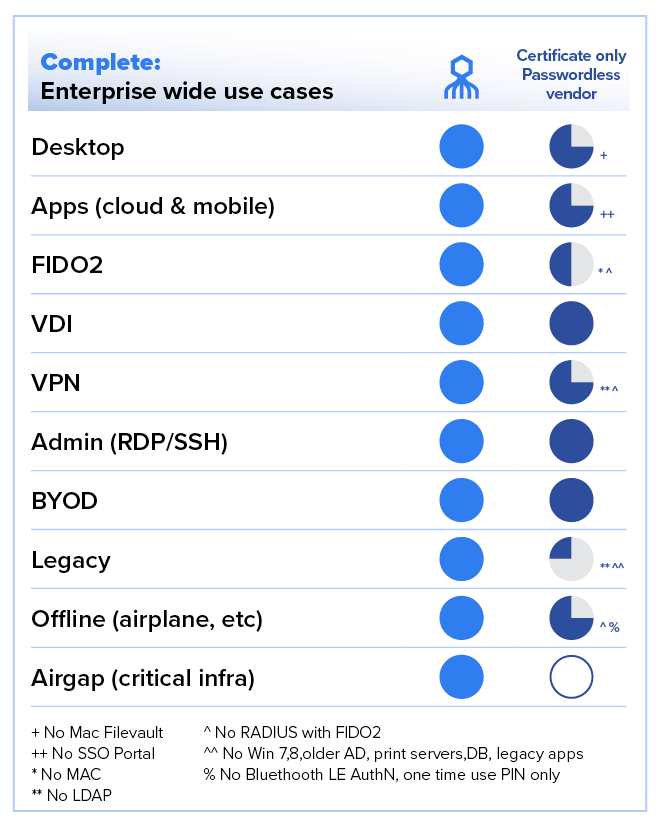
Some passwords workflows ⍯ Your workforce never having to create, remember, type, expose, or rotate passwords.
Secret Double Octopus Full Passwordless
Secret Double Octopus exclusively focuses on solving complex workforce strong authentication challenges, including desktop MFA, SSO, and Full Passwordless. Full passwordless is a goal to achieve, the Holy Grail if you will. Its an argument for breadth (covering all the login events a user may face in their work) and depth (being able to deal with the nuanced complexity of enterprises to get that full coverage). At SDO, that’s been our design goal since day one and we believe we’ve reached it. As a result, SDO is the recognized “best-in-class” passwordless solution and the most feature-complete workforce platform.
The Octopus Authentication Platform is delivered as self-managed or SaaS, deployed on-prem or cloud. Octopus is designed to address the diverse authentication needs of today’s modern distributed enterprise. SDO provides a universal authenticator for accessing all your enterprise resources, including custom or legacy apps, desktops, web apps and VPN (amongst others). Once enrolled, users enjoy Full Passwordless experience across all of their workforce workflows, never having to recall or change another password.
With SDO, you can get started by closing MFA compliance gaps like desktop MFA with a pathway to Full Passwordless MFA. Additionally, with Octopus, it doesn’t have to be all or none. If there are departments that push back on losing control over their passwords, SDO can run in a hybrid model. Some users can set their password, then let SDO orchestrate their authentication “passwordfree” with MFA, while other groups have the Full passwordless workflows.
Full Passwordless = Your workforce never having to create, remember, type, expose, or rotate passwords.
Ready to get started? Set up a meeting with our passwordless expert.