For today’s enterprise, maintaining an arsenal of effective network tools is all about access.
Organizations need to provide access to a slew of online programs and applications to the right people in order to streamline operations.
To accomplish this, organizations utilize methods to maximize the use of digital identities for multiple users. Single Sign-On (SSO) and its variant called Federated Identity tend to be the go-to mechanisms for most organizations.
The problem is, most companies don’t appreciate the differences between these two methods, as well as the implications they’ll have for employees and overall company security.
What is federated authentication and how does it work? How does it differ from SSO ?
What are the risks and benefits involved with these methods of digital access?
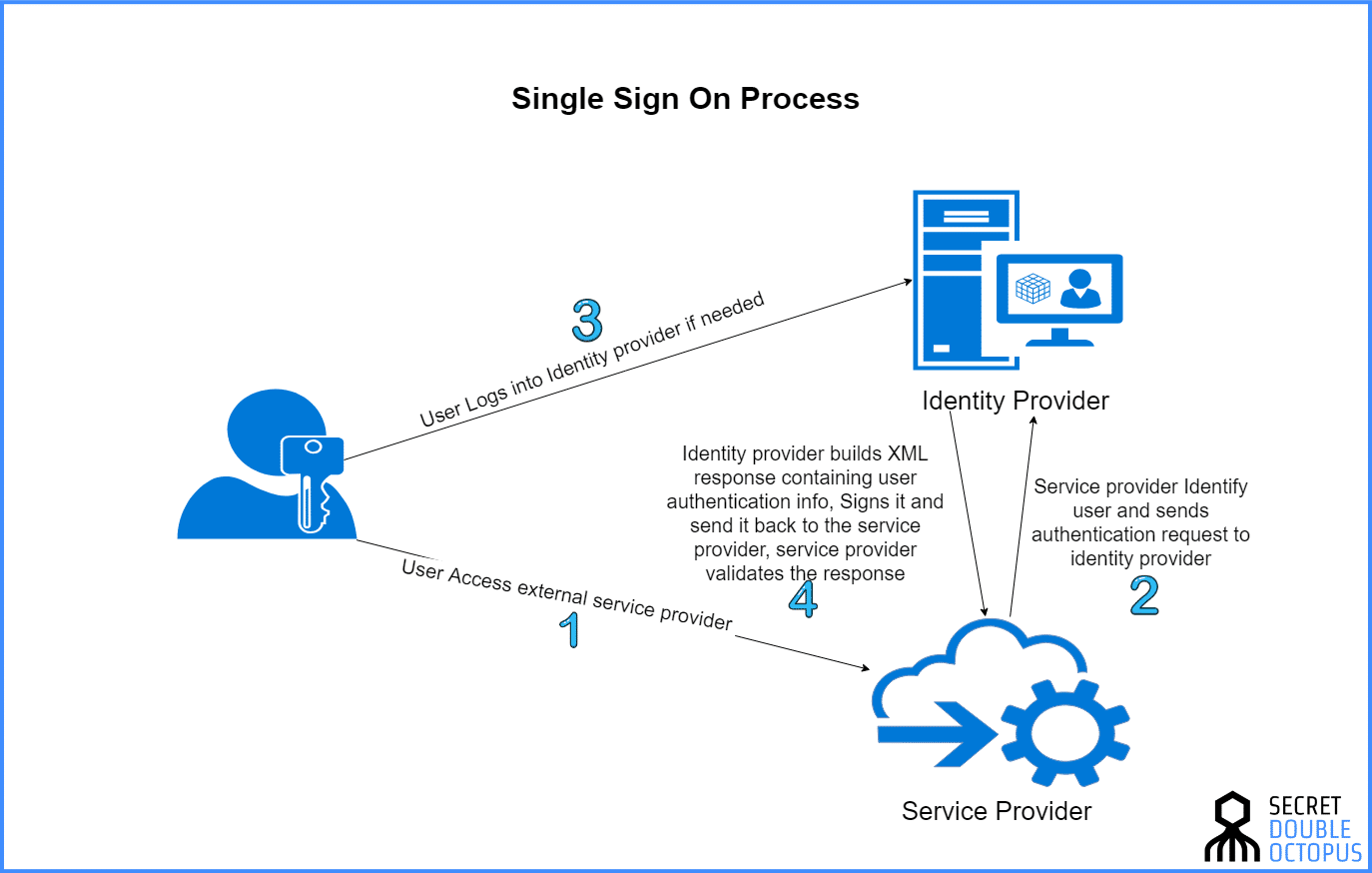
Single Sign-On: The key to access diversity
In the early days of the internet, the web’s infrastructure was not built to accommodate diversified identities. Multiple logins by a single digital identity were considered something to avoid from a cybersecurity perspective, but unfortunately was the mainstay of access in the boom of Shadow IT adoption of web/SaaS applications.
The drawback to this lack of standardization for digital identity was having to log on to different web applications separately and distinctly: a cumbersome, time-consuming, and most importantly, workflow killing reality. The industry had to find an answer to this problem quickly.
Enter Single Sign-On (SSO) .
SSO is a simple yet vital function that allows multiple web applications to be accessed simultaneously. It’s what lets you, for instance, browse your Gmail account in one tab and open YouTube in another. It is also the tool in which web services grant you access to different sections in the same broader account. Consider online banking for instance. A user can typically move from their checking account to a savings account without re-entering login credentials, even though these two accounts are very distinct. When online bank clients click on another section of their accounts, the site re-authenticates them using the same credentials entered during the original login.
What is an Example of Single Sign On (SSO)?
There are many SSO solutions in the market. Active Directory (AD) is an example of SSO because all domain resources joined to AD can be accessed without the need for additional authentication. SAP, Oracle, IBM, and others offer SSO solutions for enterprise use. Okta, OneLogin, and others specialize in single sign-on for web applications.
What are the Advantages of Single Sign On (SSO)?
To name a few of the many advantages that SSO provides an organization
- Access logs – an SSO portal provides detail reporting on who accessed what
- Session time – by eliminating credential re-authentication, users spend less time on the authentication process leading to improved productivity.
- Centralized database – one database that includes logs for authentication and authorization to support compliance and administration.
- Fewer credentials mean a lower chance of phishing – phishing emails and social engineering become much more difficult
- Reduced help desk costs – reducing the number of credentials (passwords) translates to fewer help-desk calls which are estimated at 20 – 50% of all help desk calls.
What are the Disadvantages of Single Sign On (SSO)?
The main disadvantage of SSO is in its use of one set of credentials. If those credentials are not protected correctly and are stolen, an attacker has access to the entire kingdom. Companies should always use a 2nd factor to login to SSO (at the very least), and companies who take security seriously will use multi factor authentication (MFA).
The second less talked about disadvantage to SSO is the fact that while it provides single sign-on it does not provide a single sign-off, the logoff process varies from application to application and depends on the settings of the application, user sessions usually stay active long after the user has completed his/hers use, which can lead to session hijacking .
Federated Authentication Vs. SSO
While the advent of SSO brought great convenience to users, it left some holes unfilled.
For one, users have to rely on any given application to support multi-factor authentication (MFA) for additional protection. The user still has to remember all the different passwords for each site they’re using or resort to a password manager. SSO also creates potential security liabilities . For example, any user with login credentials for a specific service will continue to have access until their account is manually deactivated. This inevitably creates the scenario in which employees maintain access to company services long after they leave the company. It also results in the company still paying for licenses that are assigned to former employees. These factors can make SSO both costly and insecure.
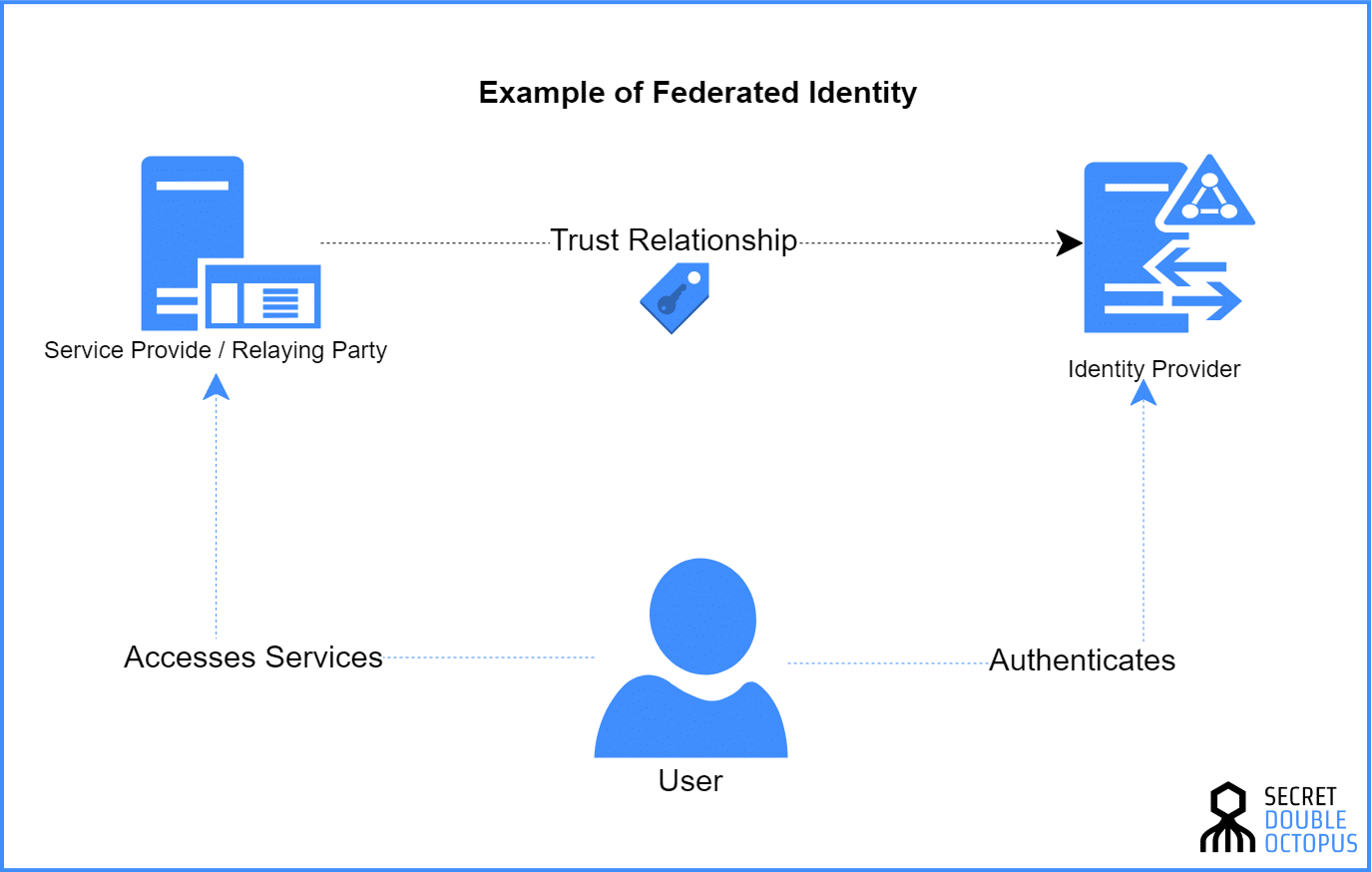
What is Federated Identity Management?
The concept of Federated Identity Management (FIM) was introduced to address these issues.
Federated Identity Management is the set of agreements and standards that enable the portability of identities across multiple enterprises and numerous applications to support large numbers of users.
It is essentially an arrangement that can be made among multiple organizations that let subscribers use the same identification data to obtain access to an application, program, and even the networks of all members of the group. This is the important difference between SSO and Federated Identity. While SSO allows a single authentication credential to access different systems within a single organization, a federated identity management system provides single access to multiple systems across different enterprises. In such a system, users do not provide credentials directly to a web application, only to the federated identity management system itself.
It’s all about trust
The advantages of Federated Identity over standard SSO have made this method the preferred option for many media to large companies.
The problem that many companies skim over though, is that, at a fundamental level, FIM still leaves open the fundamental security problems of identity diversification created by SSO.
How is this?
Any Federated Identity system is based first and foremost on mutual trust . Each party using the federated identity credentials are essentially allowing all the other members to access information contained on, and track activities of the shared application. This risk is exponentiated when dealing with sensitive applications such as data management software and other programs that deal with personal data. Furthermore, FIM systems rely on the constant communication back and forth by individual users and a centralized identity provider (IDP) in order to authenticate and grant authorization. If for some reason the metadata used to authenticate a user to the IDP was compromised, through unintended leaks, or more classical hacking methods such as phishing attacks, a criminal would be granted the same access to the federated identity provided to all other partners.
While many solutions exist to make FIM more efficient, pretty much all still leave open serious security risks.
Why Should I Make The Move to Federated Authentication?
Enterprises that use a wide range of applications and services are eventually faced with a scalability issue–how many passwords are their employees supposed to remember? Even with the use of SSO, their access is limited to applications within the same organizations. Switching to a federated identity provider allows employees to access their employers’ full suite of services, as long as they support an identity federation.
It creates a frictionless user experience that maximizes both data security and internal communications in a way that traditional passwords and other authentication methods like two factor authentication cannot.
The New Paradigm
Secret Double Octopus’s Passwordless MFA is a paradigm shift in managing multiple users to the same web platforms and applications. Unlike other authentication tools, it does not rely on metadata that a user needs to remember and then submit in order to be authenticated. Additionally, communication between the user’s device and the platform is accomplished via Secret Sharing , meaning partial information using multiple layers and routes is transmitted at a time, preventing the interception of any usable data by an adversary.
Diversifying digital identities ramps-up an organization’s work efficiency by reducing authentication time for all cloud and on-premise programs and applications. It should not have to come at the cost of a company’s network security. Incorporating the right authentication tools at the individual user level can allow an organization to reap the full benefits of SSO.