Most MFA misses the mark for Zero Trust
Cybersecurity mandates and best practices prescribe adopting strategies based on Zero Trust. Authorities like NIST, CISA, MITRE ATT&CK, and industry analysts all recommend rolling out multifactor authentication (MFA) but mainly acknowledge MFA as we know it isn’t working.
Newer interpretations raise the bar by calling for “phishing-resistant MFA” to stop today’s machine-led social engineering and the bad things that follow — ransomware, account takeover (ATO), business email compromise (BEC), etc. – by getting rid of passwords and improving identity management and verification.
Clearly, it’s time to change directions.

What you’ll learn
In this post we’ll discuss:
- The role of high-assurance authentication as the foundation of Zero Trust defense strategies
- Why today’s MFA can’t fulfill the promise of Zero Trust
- The potential for passwordless MFA to create Zero Trust Identity Verification with the highest thresholds of confidence
But first, an update on Zero Trust in 2024.
What is Zero Trust and where do businesses stand?
“Zero trust” refers to a quantum paradigm shift — a journey or evolution in mindset versus a particular use of point products and platforms. The name itself sums up the main mechanism of a Zero Trust philosophy: “Trust no one until you verify that they are who they say are, and then, only let them do what you need them to do.”
A matter of trust
Zero Trust fundamentally updates the old “castle and moat” approach of trying to keep malicious threats out by taking more realistic stance that assumes attackers canfind their way in. From there, the goal becomes spotting threats and acting fast to minimize the potential for damage by:
- Verifying identity and limiting access
- Maintaining dynamic control and limiting privileges
- Monitoring activity and limiting risk from digital exposure
A journey versus a destination
Trust is at heart a numbers game. While too much trust opens the door to attacks, even security idealists acknowledge the amount of trust we extend can’t ever really be “zero.”
Yet despite digital transformation, remote work, and interconnection to third parties and public cloud services, CISOs need to get as close as possible. Wherever companies are in their cybersecurity maturity journey, experts all agree that the obvious first step is toward implementing Zero Trust is making sure anyone attempting to access, move, or manipulate resources is who they claim to be.
Zero Trust Identity starts with MFA — but most MFA falls short

Implementing MFA improves upon simply relying on credentials – username/password combinations and PINs—for verifying identity. MFA alone might raise companies’ confidence level to maybe 70% — significantly better than with passwords alone, but still far from checking the box on “zero” trust.
Passwords are notoriously weak
As many companies have learned the hard way, the problem with conventional MFA is that user passwords provide a fatally flawed foundation. Passwords can be guessed, shared, lost, stolen, and even bought and sold. Second factors that use email, SMS texts and push notifications also can be socially engineered.
Using something that doesn’t involve “what users know” works better. Options include:
- Authenticator apps installed on personal devices
- Physical hardware tokens
- Biometric information captured by voice, iris, or facial recognition scanners
Stronger second and third factors based on “what users have” and “who users are” can bring MFA identity assurance levels closer to 80% but keeping passwords as a foundation precludes getting anywhere close to Zero Trust identity. Simply piling on additional steps gives users more hoops to jump through which becomes “too much of a good thing” very fast. Frustrated workers are less productive and more inclined to think up clever but dangerous workarounds.

Modern attackers even leverage social engineering techniques like push-bombing that bombard users with requests to grant access until they give in and click, “Yes, it’s me” to stop the requests from coming, even when they know it’s not them trying to log in. “MFA fatigue” is a growing problem, but the bigger-picture issue is:
Legacy MFA can’t stop phishing
Phishing leads to compromised credentials that still play a role in 80% of all security breaches.[i] Despite businesses’ ongoing investments in MFA, phishing continues to grow and evolve into a commoditized “as a Service” global industry powered by AI.
At the same time, regulations around phishing resistance have become more explicit, and immediate. M-22-09 from the Biden administration’s Office of Management and Budget in the US requires federal agencies – and companies that make up their supply chain – to achieve specific zero trust security goals by the end of Fiscal Year (FY) 2024.

The memo titled, “Moving the U.S. Government Toward Zero Trust Cybersecurity Principles,” directly links Zero Trust to phishing-resistant MFA:
A transition to a “zero trust” approach to security provides a defensible architecture for this new environment. As described in the Department of Defense Zero Trust Reference Architecture, “The foundational tenet of the Zero Trust Model is that no actor, system, network,
or service operating outside or within the security perimeter is trusted. Instead, we must verify
anything and everything attempting to establish access . . . This strategy places significant emphasis on stronger enterprise identity and access controls, including multi-factor authentication (MFA).”
As the foundational layer, the memo says:
The strategic goals set forth in this memorandum align with CISA’s five pillars:
1. Identity: Agency staff use enterprise-managed identities to access the applications they
use in their work. Phishing-resistant MFA protects those personnel from sophisticated online attacks.
What does this mean for enterprises?
The takeaway here is that any approach to MFA that continues to use credentials – “something users know”— as its first factor of authentication will fail (and already has failed) to meet MFA’s primary goal of shutting down phishing attacks. This failure translates into a dangerous time advantage for threat actors since, once an attacker succeeds in posing as a trusted user, many security controls won’t flag aberrant behavior until something bad happens.
To begin closing the confidence gap left by most MFA, modern approaches must remove user passwords in favor of stronger authentication workflows that combine more reliable factors of verification:
- Something users have (tokens, smartcards, cryptographically pinned devices), and
- Something they are verified with biometrics (facial, iris, voice, fingerprint scanning)
Impersonation and insider threats fly under the radar
Once a user completes authentication, legacy security policies default to allowing them to move through the network undeterred, a posture that makes detecting insider threats and third-party attacks much more challenging. A malicious or even misguided insider can provide working credentials, tokens, and one-time passcodes (OTPs) to somebody else to get something done quickly. That person might or might not be trustworthy or security-minded.
Overemphasis on checking boxes
To close the confidence gap, companies must go beyond merely checking boxes associated with Zero Trust to create and enforce policies and processes that find and shut down risk. From an infrastructure perspective, that means removing user passwords altogether and, wherever removing them altogether isn’t possible, replacing static passwords with tokens generated on the fly to complete authentication. Passwordless MFA bridges the Zero Trust confidence gap
In general, a passwordless MFA approach:
- Stops phishing by removing the credentials being phished
- Complies with mandates and recommendations for Zero Trust and phishing-resistance
- Makes life easier for users (and IT)
If traditional MFA gives us to roughly an 80% confidence level that the person attempting to access resources is who we think they are, taking passwords out of the login equation brings trust levels up above 90%. With a passwordless approach, anyone seeking access must prove their identity using reliable criteria – “what users have” and “who users are” – and possibly cryptographic binding of users to corporate applications. There are no judgment calls for anyone to make and no risky actions that can be manipulated.
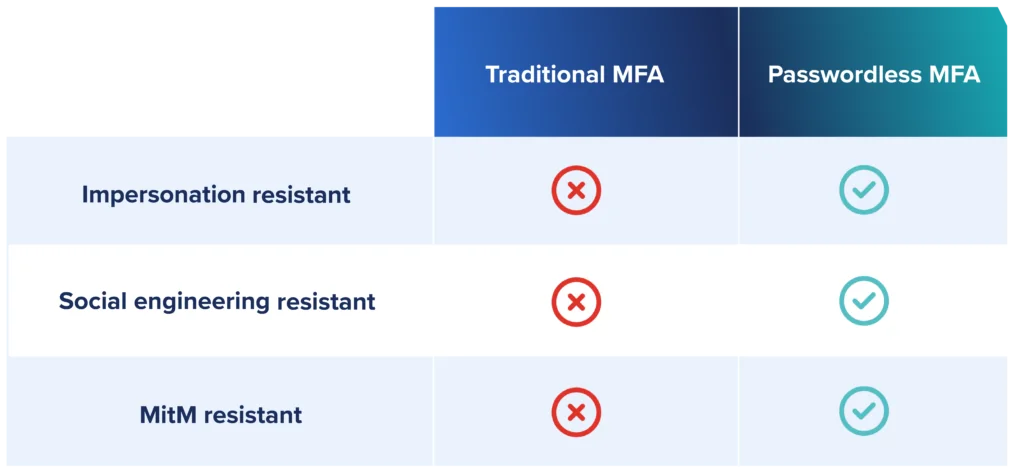
But it’s worth noting that all passwordless MFA solutions are not created equal. The Secret Double Octopus passwordless authentication platform meets NIST 800-63 (Digital Identity Guideline) requirements for AAL3-compliant high-assurance verification.
High-assurance passwordless approaches100% confidence
What would companies do differently if they could all but guarantee that every person seeking to access critical resources was who they say they are? The possibilities are endless but at the very least, they’d move faster.
NIST 800-63 defines progressive assurance levels based on the potential harm a successful malicious authentication might cause an organization and maps risk levels to MFA requirements
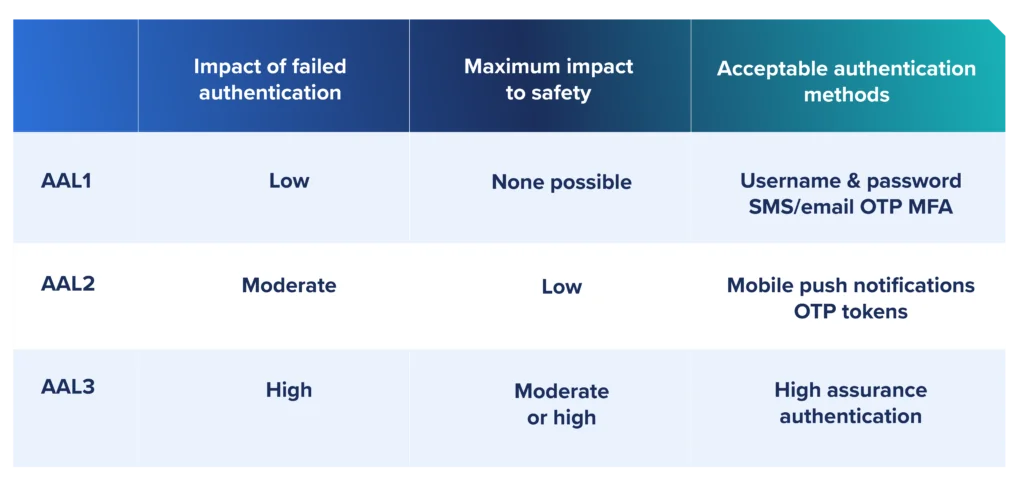
NIST 800-63 directly applies to federal government entities but requirements radiate out to suppliers and other enterprises that do business with the government. That being the case, it’s only a matter of time before the rules for MFA in the private sector follow suit.
What’s the takeaway?
To achieve the highest thresholds for identity verification, passwordless MFA needs to be best-in-class, with added features for high assurance to stop phishing, impersonation, and collusion.

To learn more about ultra-high-assurance identity verification, check out our recent blog, The CISO’s MFA dilemma: “Did I do enough to stop a breach?”
Octopus pivots defenses toward prevention and Zero Trust
Octopus Passwordless MFA bridges the gap between the vision and reality of zero trust to improve trust management and prevent more attacks. This means:
- Achieving the highest-assurance identity verification with 100% enterprise-wide use case coverage
- Increasing user satisfaction
- Alleviating resource gaps
High assurance/trust level model
Octopus adds additional assurances to elevate identity verification confidence levels to 95% or higher. These include:
- Cryptographic pinning of devices and applications to resist impersonation attacks and render any info gathered through phishing or social engineering campaigns useless
- An enhanced phishing-resistance feature suite designed to stop MITM attacks
- Proximity assurance verification for AAL3-compliant, highest-assurance authentication
Better user and IT experience
Reactive defenses bring companies of all sizes face-to-face with the worldwide shortage of cybersecurity skills. Updating behind-the-scenes Active Directory infrastructures to support passwordless MFA on the front end can quickly overtax IT and security teams.
With other passwordless MFA solutions, it might take days or weeks to update the infrastructure to support each individual application. The Octopus passwordless MFA solution makes it possible to adopt passwordless login on the front for all applications in a matter of hours or days and update the backend infrastructure whenever IT chooses.
- Eliminates user-managed passwords, user- and IT-led password resets and rotations, and 40% of all Help Desk calls
- Keeps imposters out of your environment and prevents lateral movement from triggering alerts that take time to investigate
- Reduces efforts and costs associated with triage, incident response (IR), forensics, recovery, and brand damage
100% of investments should move you closer to Zero Trust
To accelerate your Zero Trust journey—and its intended benefits—Octopus Passwordless MFA helps companies go beyond checking boxes to strengthen security so you can:
- Avoid risk from AI-led social engineering, phishing, ransomware, insider and third-party threats
- Reduce cost and time-to-benefit from MFA
- Scale your defenses as your threat landscape evolves during mergers and acquisitions (M&A), digitalization, and remote work
- Turn identity into a preventative layer of security

To learn more about the Octopus MFA Platform, download the ebook, Got Phished? How to Get MFA Right the First Time.
[i] [i]Verizon, 2022 Data Breach Investigations Report, 2022