Early February this year, researchers found a Man-in-the-middle (MITM) vulnerability in the popular Ledger hardware crypto wallet application that allowed hackers to redirect victims’ funds to their own wallets by changing the destination address of cryptocurrency transactions. The news came as a disappointment to users who considered hardware wallets such as Ledger as the most secure way to store their digital fortunes.
Bitcoin and blockchain, its underlying technology, have been designed with security in mind.
But as the latest disclosure showed, any system that relies on key-agreement protocols and the storage and exchange of secrets is vulnerable to man-in-the-middle attacks in one way or another, and the best way to fend off MITM attacks is to use authentication systems that obviate the need for secrets.
How do MITM attacks work?
To transfer and store funds, cryptocurrencies such as bitcoin use the blockchain, a distributed ledger of transactions. Every transaction made in bitcoin is sent to an address on the blockchain protected by a pair of encryption keys. A public key available to everyone enables any party to send funds to the address, and a secret private key enables the owner of the address to transfer its funds to other parties.
In a MITM attack, a malicious actor compromises the communication between two parties and steals or tampers with the information they exchange. In the case of the Ledger wallet, a malware installed on the target computer changes the destination address of bitcoin transactions and replaces it with the address of the attacker’s wallet. The only way users can detect and stop the attack is to manually compare the address displayed on their computer with the one that appears on the Ledger’s display.
This isn’t the first time bitcoin and other cryptocurrencies have become the subject of man-in-the-middle attacks. In past years, hackers have used different methods to intercept or steal private keys and to alter transaction addresses to lay their hands on the highly valuable and popular cryptocurrencies. In other cases, they’ve broken into online cryptocurrency exchanges and managed to steal large stores of cryptocurrency keys worth hundreds of millions of dollars.
In this regard, bitcoin and other digital currencies are no different than other key-agreement protocols that rely on secrets. Hackers have used MITM attacks to steal passwords, encryption keys, code signing keys and other sensitive data that we use to identify and authenticate ourselves online. MITM attacks are especially dangerous because they enable hackers to pose as legitimate parties and to perform very damaging actions such as inject malware in the web pages, files, and applications that we access and exchange online.
For instance, last year, a group of hackers broke into the servers of a Ukrainian accounting software firm and gained access to the keys the company used to sign the binary updates it sent to its clients. The hackers created a patch for the company’s accounting application that was inflicted with a dangerous ransomware virus and signed the patch with the keys making them look legitimate. They then pushed the malware to thousands of customers that used the company’s application, which thought the application was coming from a legitimate source. In short order, the ransomware propagated to tens of thousands of computers.
Compare Enterprise Authentication People
How multi-channel technologies prevent man-in-the-middle attacks
Hackers that stage man-in-the-middle attacks know that we rely on secrets to guarantee the integrity of our identities and security of our communications. If they manage to gain access to those secrets, they’ll be able to impersonate us and perform a malicious activity on our behalf.
If you had a way to authenticate yourself, communicate and share information without the need to exchange secrets, hackers would have a harder time staging man-in-the-middle attacks. That is the main idea behind secret-less protocols such as Secret Double Octopus.
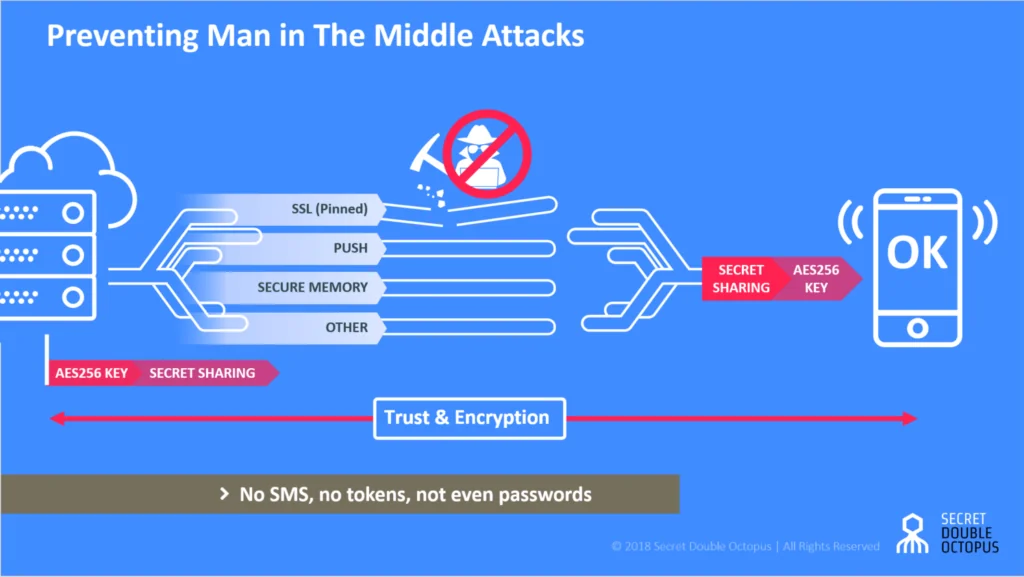
Secret Double Octopus zero-knowledge authentication enables different parties to verify each other’s’ identities without the need to exchange keys or reveal critical information. Secret Double Octopus and its associated mobile app, the Octopus Authenticator, neither store nor send passwords or keys. Without one point of failure, hackers are unable to stage man in the middle attacks.
To further protect sensitive operations, Secret Double Octopus utilize a multichannel secret sharing algorithm in which authentication is done piecemeal through different channels, including SSL, Push notification and secured mobile memory. This means that potential attackers will have to separately hack each channel to be able to falsely identify as the user, which is virtually impossible.
From a user’s perspective, the Secret Double Octopus provides a friendly and easy-to-use interface. It doesn’t require users to memorize passwords or to go through complicated steps in order to validate and approve operations while maintaining the highest level of authentication assurance.