How much safer did 2FA make us?
SaaS vendors worldwide: “Add a phone number to keep your password secure.”
Hackers worldwide: “Lol”
The endless barrage of successful phishing and ransomware attacks shows the futility of relying on passwords to protect sensitive data. So, we began adding two-factor authentication or “2FA” and requiring users to complete another step in the login process to help prevent breaches and identity theft. And 2FA worked, to a point.

What you will learn:
- What 2FA is, and isn’t
- Hackers bypass 2FA in many ways
- Passwordless authentication addresses the root cause of attacks (spoiler alert: it’s not just passwords)
2FA is not a cure-all
Adding a second step proved vastly better than a password-only login, but still far from enough to stop modern attacks that use AI and “kits” to launch sophisticated social engineering and phishing campaigns. IT and security professionals added more steps to create modern multifactor authentication (MFA) that makes identity verification incrementally safer, yet phishing lives on.
So, one thing became clear:
Passwords are fundamentally unsafe
As long as passwords stay in the mix, and at the foundation of authentication, piling on more layers of identity verification to the login process makes for a band-aid solution at best. 2FA and most MFA fail to address the root cause of breaches – passwords and password management by the humans who create them.
In this post, we’ll take a quick look at various ways threat actors bypass 2FA and why true peace of mind can only be achieved with a passwordless approach to authentication.
How do hackers bypass 2FA?
Common techniques for bypassing 2FA include:
Necro browser
Genius solutions are simple and this one fits the bill. Two tools Muraena and NecroBrowser automate phishing attacks that can bypass 2FA. Most defenses won’t stop them for a simple reason – these attacks go directly to the root cause of almost all breaches – the users.
It works like any phishing scheme save for one significant upgrade. Instead of simply creating a fake website that looks like a legitimate one to trick users into typing in their passwords, the toolkit acts as a proxy between the victim and a legitimate website. Once the user attempts to log in – the request is sent on behalf of the user to the service. The user, mistakenly thinking that they are on the legit login page, hands in both the password and the 2FA PIN — directly into the hands of the attacker who gains complete access to the system.
The biggest issue with NecroBrowser is that although the setup for such an attack is relatively complex, since it is a completely automated tool, bypassing 2FA becomes accessible to almost anyone, regardless of their technological prowess.
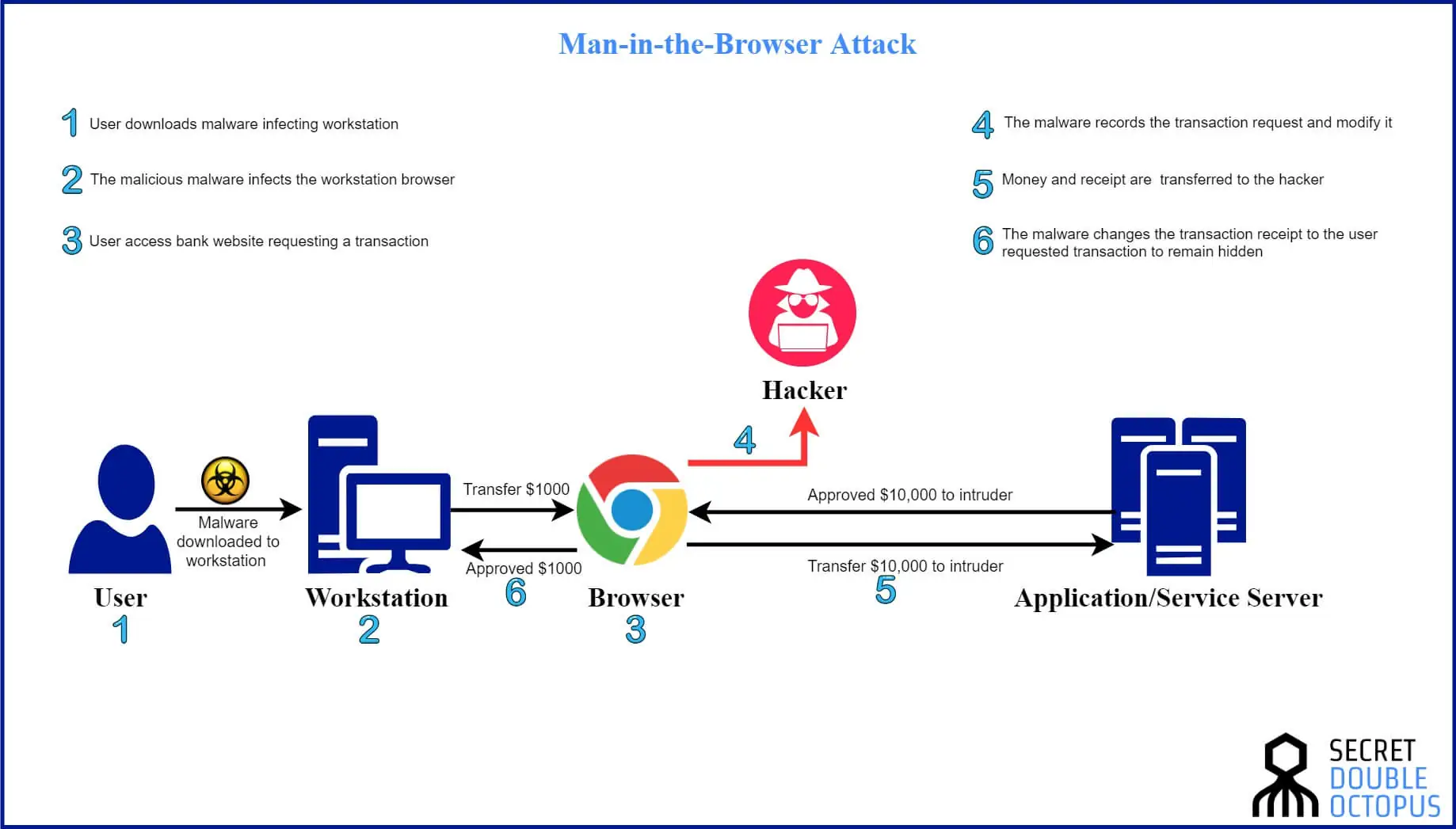
Man in the browser attacks
Man-in-the-browser attacks require a bit more legwork. First, a hacker prepares in advance by infecting an endpoint with a Trojan virus. This is usually done by asking the user “nicely” with the help of phishing, social engineering and spear-phishing techniques.
Once the Trojan is active, the attacker gains control of the user’s internet activities. Threat actors get full access to the browser history and activity, and even see what users type in – including their passwords.
Trojans designed for MITB attacks generate code for extra input fields to appear on websites the user visits, including the ones required for stealing 2FA tokens.
The upshot? Users trust browser with too much personal information.
Social engineering and phishing
Social engineering uses human psychology against users, and no technology can effectively block them from doing so as long as passwords remain in the mix. Threat actors leverage social engineering to bypass 2FA in several ways:
Scenario one: The hacker gains user credentials and goes phishing
- The hacker sends a warning message to the user, something along the lines of, “Your user account has been accessed from a suspicious IP address. If the IP does not belong to you, please reply with the verification code sent to your number.”
- At the same time, the hacker uses a username and password to log into the targeted service.
- The service provider sends a 2FA code to the connected device, thinking that the request came from the user.
- The user responds to the fake warning message with the verification code they just received.
Voila, the hacker bypasses the second step of 2FA.
Scenario Two: The hacker has no credentials but still goes phishing
If the hacker does not know the username, password, phone number or verification code, they can still use social engineering and phishing attacks to get what they need:
- The hacker creates a persuasive email that looks like it’s coming from the targeted service.
- The email has a link that looks real. The user clicks the link and gets taken to a fake login page.
- The user attempts to login on the fake page and serves up credentials that the hacker can use to simultaneously sign in on the real site.
- The real site sends a verification code to the number associated with the legitimate user and the user promptly enters the 2FA token on the fake login site.
- The hacker take the code and uses it to complete login on the real website.
Voila, the hacker bypasses the second step of 2FA.
Privilege escalation
Once attackers gain access to a corporate account, they look for vulnerabilities, design flaws or configuration oversights to gain elevated access to protected resources all the way from the user level up to the Kernel level. From there, they manipulate 2FA settings, like modifying the phone number associated with an account so that the OTPs used as the second factor of identity verification in 2FA now get sent to the attacker’s device.

Passwordless MFA prevents 2FA bypass
As we’ve seen, hackers can target 2FA authentication in a virtually endless number of ways including:
- Brute force attacks on 2FA PINs
- Intercepting 2FA PINs “in transit”
- Rerouting 2FA to attacker’s device
- Stealing session tokens after 2FA occurs
- Exploiting bugs such as 2FA tokens that don’t expire
The way out of this mess is simple – get rid of passwords. Humans represent the last line of defense against hackers in a password-first world, a very precarious situation since 100% of data breaches involve humans and more than 80% still involve credentials. People are busy, and often in a hurry, so they create easy to guess passwords, reuse the same ones across services, write them down, share them, and give them away without even realizing it.
Password managers and complex rotation procedures only complicate policies and drive users crazy. They don’t work now, and they definitely won’t work in an AI-powered future.
Passwordless authentication offers ‘human-proof’ protection
Passwordless MFA creates authentication workflows that don’t rely on the weakest link in security (sorry but it’s still people). The Octopus Passwordless authentication platform offers seamless, mathematically unbreakable authentication that doesn’t require humans to create, manage, memorize or enter passwords—ever. Octopus provides AAL3-compliant, phishing-resistant login that takes away attackers’ favorite tool and the extra hassle users hate.
Key Takeaways
- 2FA enhances security but is not infallible and can be bypassed by skilled attackers.
- Hackers use techniques like NecroBrowser, man-in-the-browser attacks, and social engineering to exploit 2FA vulnerabilities.
- Human error often weakens security, as users are the weakest link in the chain.
- Transitioning to passwordless MFA can eliminate the need for users to manage passwords, reducing risk.
- Passwordless MFA provides a more robust security solution by minimizing human involvement in authentication.
- As cyber threats evolve, organizations must adopt advanced measures that address the root causes of breaches.