High-Assurance Push Authentication
For Cloud and On-Prem Directories

IT leaders face fast-approaching deadlines to prove the business has met MFA mandates and cyber insurance criteria everywhere. But traditional MFA can’t beat the phishing menace. A phishing-resistant MFA is mission-critical.
With Secret Double Octopus (SDO), you upgrade your workforce to phishing-resistant MFA without re-architecting directories or refactoring applications.
Desktop-to-Apps Pinning stops advanced MITM phishing attacks without adding hardware smartcards or FIDO2 keys or changing your Identity infrastructure.
Other FID02 offerings just work with web apps. SDO includes CTAP2 and certified Server to protect Mac, Windows, and Linux desktops, web apps, and corporate apps.
Octopus adaptive MFA capabilities, including verified push, geolocation, and anomalous retry lockout, protect even unobservant users from push bomb attacks.
Choose a vendor that has been proven time and time again with massive scaled out global deployments.
The Octopus relieves users from password management and works with existing directories. Users never create, forget. or expose passwords, putting secrets exclusively in the hands the business. Now, admins eliminate tedious password help desk calls and modernize identity infrastructure faster without user coordination.

Enterprises run on complex and diverse workloads. But, other offerings leave critical apps and essential services behind because it doesn’t fit their certificate authentication workflows. SDO provides comprehensive use case coverage, including desktops, web apps, remote work, and corporate custom and legacy services.
LEARN MORE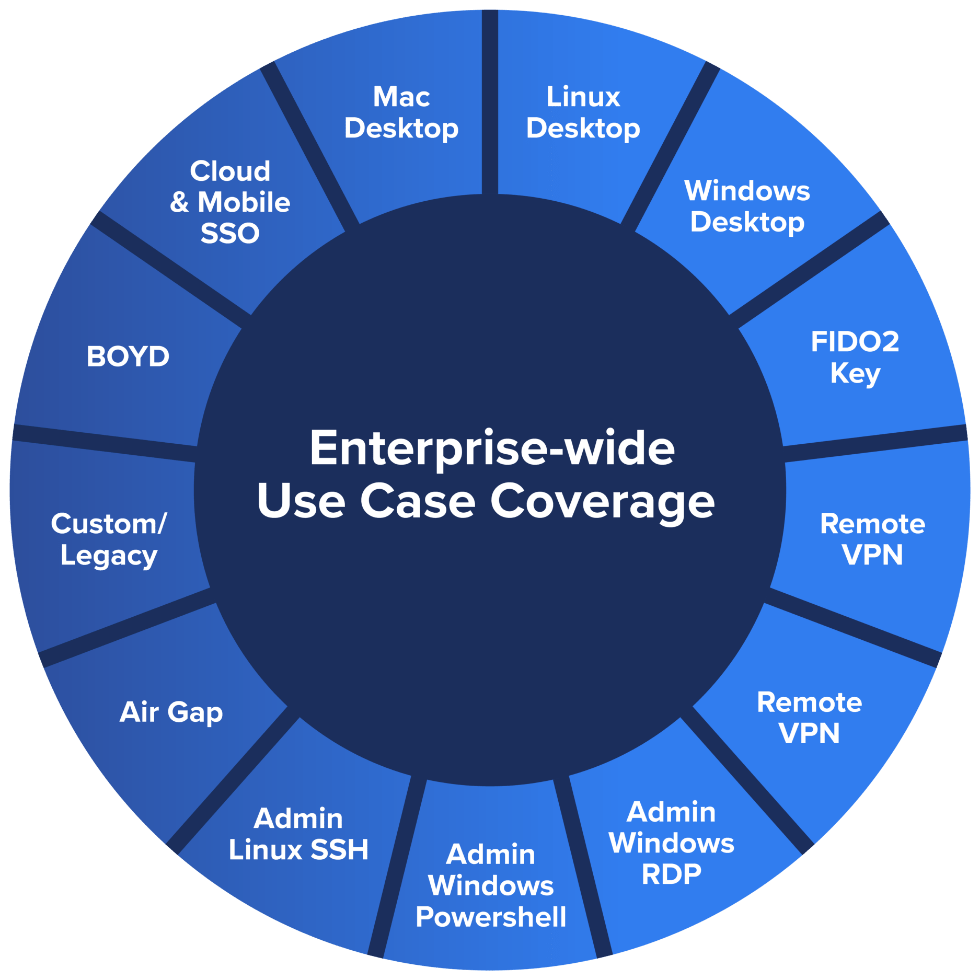
FIDO2 has the backing of Internet giants and promises a streamlined, low-cost, self-provisioned authentication future. SDO provides a complete solution that bridge FIDO2 to your on-prem and private cloud apps and services today:

SDO took top honors as the Best-in-Class Passwordless Authentication Solution for enterprises in an AITE Novarica study. This was the most thorough analysis of all significant passwordless solutions in the market and included discussions with actual deployed customers.
DOWNLOAD REPORT