Understanding MFA Fatigue Attacks
Opportunistic cybercriminals happily exploit users’ frustration with typing in passwords all day long to perpetrate modern ‘MFA fatigue’ attacks. Read on to see how multifactor authentication or “MFA” paves the way for targeted push-bombing and other attacks that increase your business’s odds of suffering a breach, and how you can make logins safer without adding to users’ frustration.
What you will learn
- What is ‘MFA fatigue’?
- What are MFA Fatigue attacks?
- How you can avoid fatigue while improving security?
What is ‘MFA Fatigue’?
Companies invest in MFA to improve the security of their user (and sometimes customer) login processes. MFA usually starts with passwords, which everyone knows can be easily phished, or guessed, bought or stolen. From there, MFA adds one or more additional steps to verify identity such as:
- Entering 4-6-digit PIN numbers sent via text/SMS
- Sending push notifications to employees’ smartphones
- Using biometrics like facial, voice, and iris scanning or recognition
- Using physical hardware tokens and smart cards that only the user should have
Employees in specialized sectors of government, industrial manufacturing, and critical infrastructure (CI) might also carry X.509-based smart cards or badges used to swipe their way into top-security or physically isolated environments (such as air-gap facilities on factory floors). When login workflows and push notifications involve too moving pieces – email, phones, apps, tokens portals — MFA ‘sprawl’ leads a predictable outcome: fatigue.
For example, a user might follow three different processes throughout the day just to log into frequently used applications:
- Windows Hello for Business (WHfB) works with some Microsoft apps and services but doesn’t secure Macs, Linux, and other systems
- MFA and SSO solutions from Okta and others work with Web and SaaS apps but not with many legacy and on-prem systems
- Custom, legacy and on-prem apps use Active Directory (AD) or standalone databases (DB) to authenticate users
These three methods offer three very different user experiences on the front end and pose very different hurdles for IT teams on the back end. MFA fatigue gets compounded even more during mergers and acquisitions (M&A) when users get asked to juggle even more stuff to access redundant systems.

MFA Fatigue Attacks: A Threat to Security and User Satisfaction
In modern MFA Fatigue attacks, threat actors obtain user credentials and initiate requests to access resources. Once the imposter completes the first step of identity verification—entering passwords—the system sends a push notification to the legitimate users’ phone asking them to hit “Yes, it’s me” and approve the request to grant access.
In MFA Fatigue attacks, threat actors bombard the system with multiple requests that in turn bombard users with multiple push notifications, similar to what happens in denial of service (DOS) attacks on the network side. Attacks succeed because, even when the real user isn’t attempting to log into anything, they assume the prompts are either coming from IT or happening because there’s a glitch in the system.
Or, they simply get frustrated, give in, and hit “yes” just to make the incessant alerts stop. Either way, users allow attackers to effectively bypass MFA and enter the network environment. The use of working credentials in MFA Fatigue attacks negates the value of a company’s investments in MFA and literally turns it against them.

Once they get in, threat actors can either act quickly — before anyone notices – or bide their time and move through the network undetected, changing permissions, stealing data, and compromising crown-jewel assets as they go.
Poor UX: a hidden cost of MFA Fatigue
Conventional MFA keeps security at odds with user satisfaction. MFA attacks add to the burden by asking users to be on the lookout for possible threats. If the company continues to use passwords as the first factor of identity verification, they may need to take steps that add even more stress for users.
For example, an enterprise might revert from convenient push notifications that users know and love to more intricate and tightly controlled methods like carrying tokens and badges or receiving and typing one-time passcodes (OTPs) to complete authentication.
MFA Fatigue attacks on the rise
MFA Fatigue continues to grow in popularity among threat actors because it’s easy. With big batches of working credentials for sale on the black market, attackers can easily begin spamming unsuspecting users. If they’re patient about it, odds ae good attackers can leverage fatigue to exploit the frustration of one or more impatient humans.

Anyone can fall prey
Threat actors haven’t been shy about targeting the likes of Cisco and Microsoft — two technology icons whose products secure enterprises worldwide — alongside ‘regular companies’ like Uber.
How to Prevent MFA Fatigue: 3 Vital Best Practices
Step 1: Educate users to spot attacks
The first step in preventing MFA Fatigue attacks from succeeding is teaching users to ignore unexplained prompts — and call security. Most enterprises require their workforce to take in-depth, or at least regular security awareness training. Education focuses heavily on helping employees spot phishing and social engineering attacks but less so on MFA and how to tell when threat actors insert themselves into the process.
Man in the middle (MITM) scams and push-bombing campaigns don’t receive enough coverage to help busy workers spot when something looks ‘phishy.’
How to Avoid MFA Fatigue and Prevent Attacks
Step 2: Review and update authentication policies
Regular reviews of authentication policies keep MFA and other investments in security aligned with the evolving needs of your business as well as user perceptions and preferences.
Step 3: Get rid of those risky passwords
As long as passwords remain the foundational step, users will keep getting phished. Threat actors get more creative every day in their use of AI tools like ChatGPT to make social engineering and phishing campaigns more compelling and convincing. The more these techniques advance, the more sense it makes to get rid of phishable credentials.
Instead of building authentication workflows around secrets that represent ‘something users know’ — i.e. the password — IAM leaders must migrate the workforce to a passwordless MFA that doesn’t waste users’ time. This strategic shift takes ‘what users know’ out of the equation in favor of ‘what users have’ (tokens, cards, the right device) and ‘who users are” as multiple ways to verify identity beyond a reasonable doubt.
| Pro tip – Don’t create passwordless MFA fatigue! Standardize MFA around a passwordless approach that provides coverage for virtually all workforce applications – in days or weeks versus months, years, or decades. Audit and take stock of the services your employees access on site, online, and remotely, and find or build a single workflow that securely unlocks them all. |
Passwordless MFA stops phishing, which prevents attackers from tricking users into providing credentials. Without passwords, attackers can’t initiate the login process to trigger push notifications these attacks need to succeed. They need to either purchase credentials – which adds to the base cost of launching attacks – or choose another technique for which IT might have other controls in place.
Octopus passwordless authentication reduces MFA fatigue among users — and IT
The Octopus Passwordless MFA platform from Secret Double Octopus (SDO) equips IT to create a single, simple login that works for all company-managed applications and to roll it out quickly. While other MFA and SSO solutions trumpet the benefits of passwordless, most if not all provide coverage only for a subset of the resources that workers need to do their jobs.
Unlike other solutions, the Octopus Passwordless MFA solution works with Windows, Mac, and Linux applications, SSO portals, air gaps, and any desired authenticator apps, techniques, and devices. Companies use one high-assurance NIST AAL 3-complaint login workflow for every application without having to recode apps or rearchitect directories.
Octopus also adds a suite of phishing resistant and MFA fatigue-resistant capabilities:
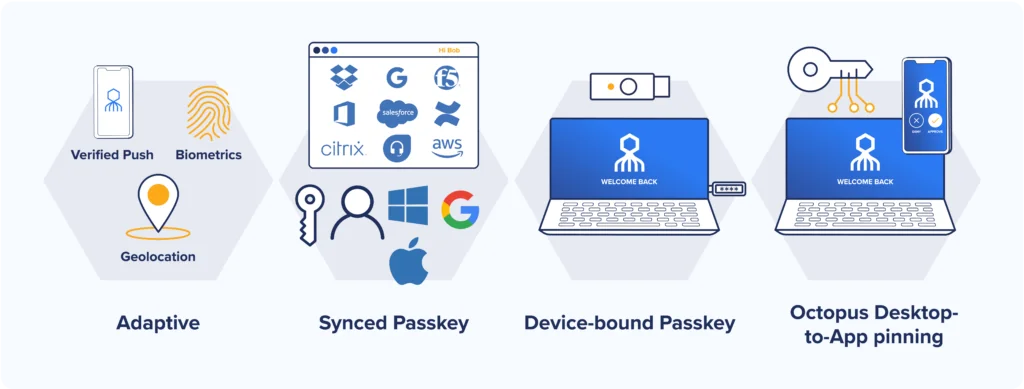
Getting rid of passwords puts an end to phishing which in turn prevents MFA Fatigue attacks. With no credentials to enter to trigger push notifications, MFA Fatigue becomes a non-starter.
Key Takeaways
- The more complicated MFA becomes, the greater the chance that MFA fatigue will lead to — instead of prevent — attacks
- Streamlining MFA by getting rid of passwords and educating users about push bombing helps avoid MFA Fatigue attacks
- A 100% passwordless approach to authentication lets organizations stop attacks without adding to MFA fatigue
Frequently Asked Questions (FAQs)
1. How can organizations tell when users experience MFA fatigue?
Two telltale signs indicate when users feel overwhelmed or frustrated with MFA:
- Related calls to the Help Desk increase
- Users find ways to bypass MFA altogether
2. Does single sign-on (SSO) reduce MFA fatigue?
Many companies invest in SSO portals to consolidate authentication for multiple web and SaaS apps in one place using a single login step or workflow. SSO helps mitigate fatigue by reducing the number of different authentication processes and devices workers have to juggle every day just to access the resources needed to do their jobs.
SSO reduces the frequency with which users have to enter passwords to once a day or even less frequently but does not eliminate the core risk inherent in using passwords at all. Only a passwordless approach to authentication removes the credentials and removes the bait attackers seek when launching modern social engineering and phishing campaigns. SSO, like MFA, must be 100% passwordless to avoid risk while reducing MFA fatigue.