
Summary
Shared accounts fail every security, compliance, and cyber insurance test, yet they remain a common practice, even in our nation’s critical infrastructure industries. Why? Because shared accounts make some collaborative work more efficient.
But now, instead of fighting the age-old battle between being secure and being productive, IT leaders can leverage Passwordless MFA technologies to close security gaps while keeping shift workers and other collaborative workflows moving at the speed of business. Passwordless delivers:
- Fast, impersonation-resistant authentication as individuals access shared accounts
- Complete visibility and audit trails that show every access of shared accounts
- Blocked access for uninvited users, attackers, and insider collusion
- Vastly improved security posture without changing shared accounts systems and applications
Why Do Shared Accounts Still Exist?
Two reasons: easy collaboration and lower cost. Shared workstation environments have long been common in many industries, including retail and healthcare, and are commonly found on industrial manufacturing floors and production plants. They increase productivity when multiple employees share resources either all at once or in a predictable sequence; for example, work that goes in shifts. Allowing whole groups of people to share the same account and see the same computer views and dashboards continues to simply make collaboration easier.
The other key driver is cost. Creating individual directory accounts for every user represents a significant IT expense, including setup and maintenance for a large pool of workers that may turnover frequently or use only a limited portion of shared resources. Companies also may save on software licenses and subscriptions.
So Why Change Now?
Again two reasons: modern cyber risk and privacy regulations. The threat landscape for industrial companies is changing at warp speed. Since the pandemic hit, cyber attacks against utilities, transportation, and other critical infrastructure are frequently reported in the media. Businesses, governments, and private citizens alike now know that things we once took for granted–everything from toilet paper and baby formula to food, water, and power supplies–are essential and must be protected.
Which brings us to the second point. Businesses only do things for three reasons: to make money, save money, and because someone told them they had to. Regulatory, industry, and cyber insurance mandates all now target critical infrastructure, forcing companies to close security gaps and improve cyber resilience.
The growing role of multi-factor authentication (MFA)
MFA is #1 on the modernization dictates in national cyber resilience directives like the EU NIS2 and US Presidential Executive Orders, closely aligned with cyber insurers. But as time goes on, industry leaders and identity managers alike have realized that traditional MFA alone is not enough, and perhaps fundamentally flawed because it relies on a foundation of passwords–credentials that can be phished, lost, leaked, and shared where sharing does not make sense.

A Simple Yet Elegant Solution
To reduce risk, friction, and cost at the same time, MFA needs to work without passwords. Secret Double Octopus’ passwordless MFA platform secures shared accounts and reduces friction while fulfilling the critical security edict of ”one person, one identity.”
While removing the vulnerable password (something users know) in favor of stronger authentication criteria like something users have and something users are, the Octopus adds visibility for detection, audit, and incident response while leaving shared accounts intact within the infrastructure.
How it works
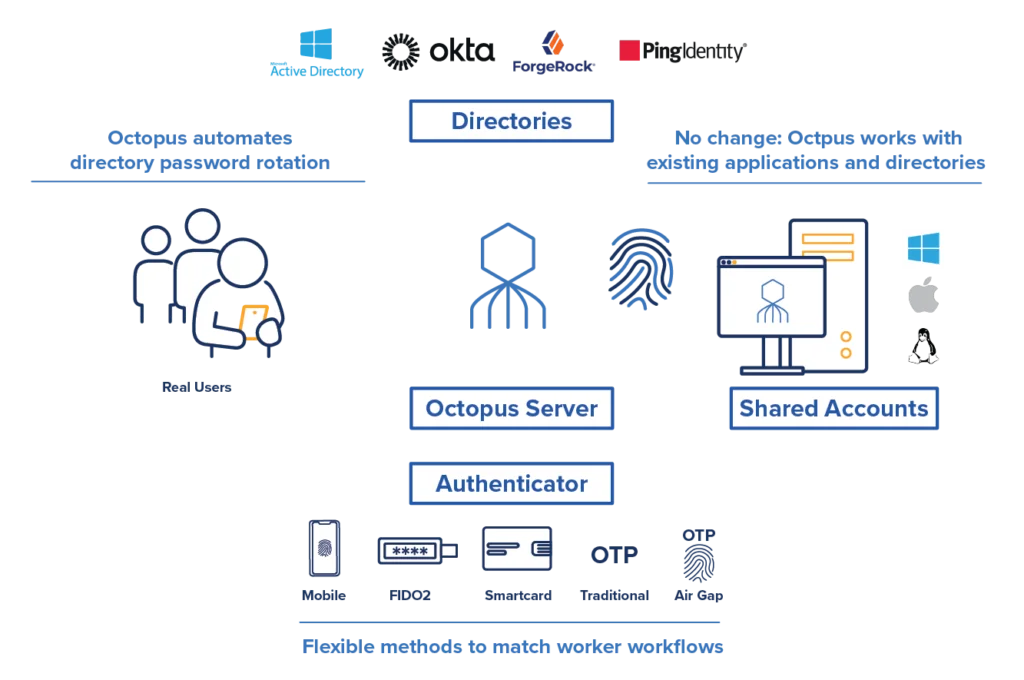
IT or the front-line manager orchestrates individual users’ accesses to shared accounts with single or multiple federated or unfederated directories or as a local Octopus RBAC admin. The Octopus manages and rotates user and shared account directory passwords within the backend infrastructure. That means although there is a shared password on the shared account, no user knows what it is, eliminating the threat of going around the MFA system or exposure to disgruntled exited employees and contractors.
A bold goal, but achievable. Passwordless MFA maintains the original objective of efficiency and cost-savings, but now with resilience and security provided to shared accounts.
Showing is more effective than telling, so I asked my friend John Kimberly (an SE at SDO) to create a demo using Sentry Enterprises FIDO2 ID cards to show how it works.
Why FIDO? Why not the cheaper proximity cards?
Octopus gives users flexible options for authentication methods that match employees’ workflow needs. In John’s demo, we used the cryptographic FIDO2 mechanism, but any of the methods listed in the diagram above can be used. All Octopus passwordless MFA methods follow strong authentication principles.
An alternative approach is issuing low-cost proximity cards commonly used for physical access. These are less secure than FIDO ID cards but may be under consideration by shared accounts administrators. I asked Mike Baker (Sr. VP, Sentry Enterprises) to comment on the benefits of high-assurance FIDO vs using less expensive proximity ID card methods. Here is what he said:
“While proximity cards do open protected doors, only the card itself is authenticated, not the actual user of the card. The person holding the proximity card could be anyone who found it, or if was shared, or who copied it nefariously. In short, the proximity card can be shared or copied and also, only works with physical security devices.
SentryCards, on the other hand, cannot be shared and provide absolute proof that the person who used the card is the actual person to whom the card was issued. There is no denying who actually logged in or used a physical device with the SentryCard.”
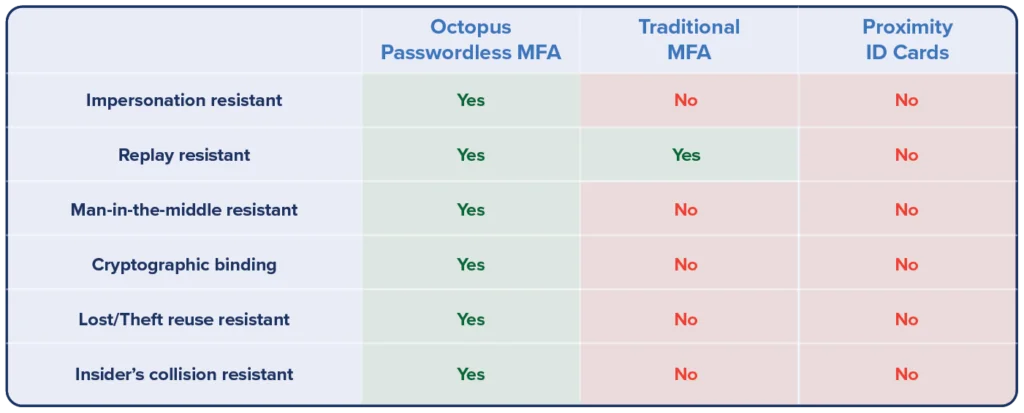
Faster, safer, and more compliant
Stong authentication into shared accounts that is both safer and faster can be achieved quickly (users can be up and running in less than an hour) with a passwordless MFA approach that requires no changes to the corporate infrastructure. To learn more about the Double Octopus shared account solution, read the new solution brief (link) on this topic, or schedule a personal demo here.