While mergers and acquisitions (M&A) fast-track growth and expansion, consolidating disparate workforces creates a host of challenges for IT and security teams. For one thing, a succession of transactions creates a gnarly mass of fragmented identities, login workflows, and identity and access management (IAM) platforms — some more advanced than others.
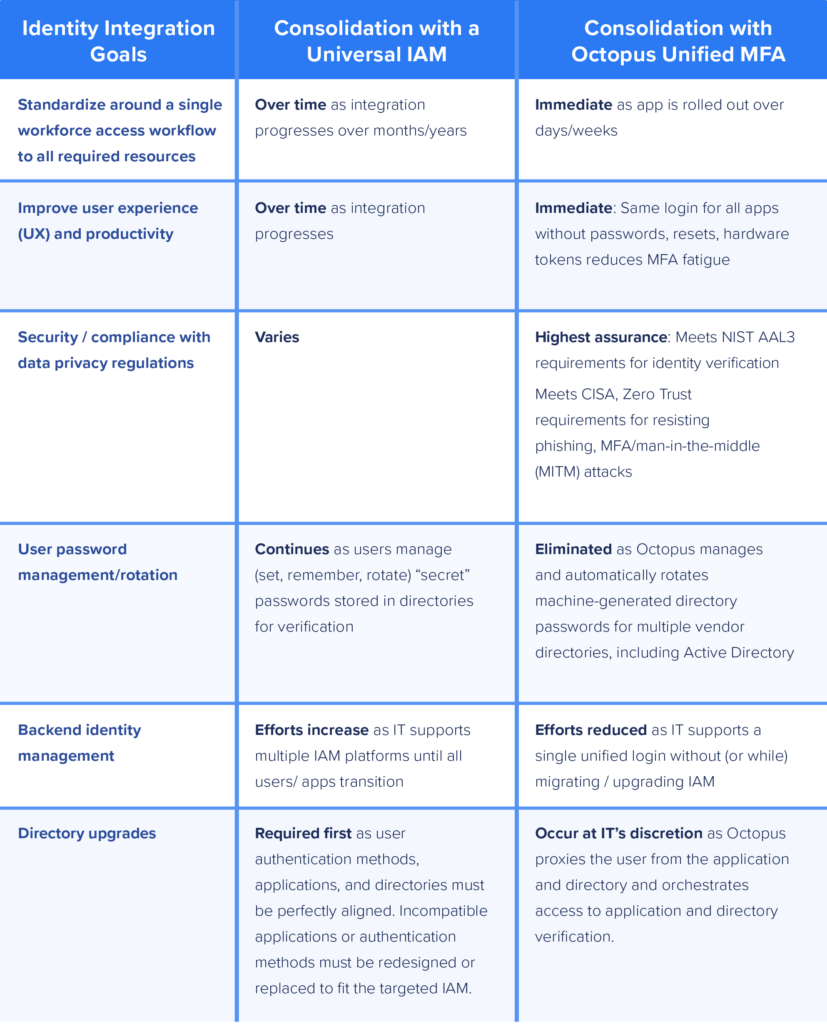
Business leaders recognize that workforce consolidation makes for an ideal time to centralize and standardize around a single unified login that improves security as well as employee efficiency — provided companies choose the right approach. For financial services and other providers in highly scrutinized sectors, the goals are clear-cut:
- Avoid risk associated with identity: Phishing, ransomware, insider threats, account takeover, lateral movement, failure to comply with fast-changing data privacy laws and regulations
- Create a better user experience: One simple login with fewer steps and devices and no secrets to remember
- Minimize IT and IAM efforts: Password management and resets, recoding applications, rearchitecting identity directory infrastructures

In this blog, we’ll compare two potential pathways to consolidating user login and identity management in terms of time, cost, risk, and complexity. We’ll see how starting with a lesser-known approach — rolling out unified passwordless MFA that works with any application — fast-tracks desired benefits while eliminating or deferring “the hard part.”
Two paths to consolidating login workflows during M&A
Newly acquired or merging companies likely use several different IAM solutions like Okta, Ping, and Azure to provide access to applications in conjunction with Active Directory to manage identities on the back end. Maintaining disparate solutions creates disjointed workflows that give rise to IT visibility gaps, security blind spots, inconsistent user experience (UX), and complex audit trails.
To overcome these challenges, large IAM vendors propose adopting a “universal IAM;” meaning, IT leaders choose and transition acquired entities’ applications, directories, and identity infrastructures to a single targeted IAM platform. This looks good on paper but charts a path froth with incompatibilities.
Hours to start, days to finish versus months and years
Time is the enemy of workforce unification. Users get frustrated with complex, siloed access to the resources they need, and having to manage a host of different passwords and authenticators. Savvy attackers know the drill and watch for the chance to exploit chaos and confusion to gain a foothold.
Universal IAM requires all managed resources from the identity platform that’s being phased out to be retooled to match the requirements of the universal IAM platform. This may require IT to recode applications to support the vendors SSO and FIDO2 technology – which only works for web applications. The more effort it takes to extend the solution to a multitude of applications — before onboarding users — the longer lead times for consolidation.
Phased migrations can take months, even years to complete as some workloads, applications, and services like single sign-on (SSO) convert more easily while others require considerable work to recode or reconfigure systems to mesh with the chosen IAM.
For industries like financial services, challenging applications often include custom, specialized and legacy apps running on-premises and holding the business’s most valuable data. Many of these have been in place for decades and cannot be converted through any reasonable effort.
On average, retooling applications to work with a new universal IAM takes a week or longer for each application, a daunting feat and timetable for companies sporting thousands of apps and facing the most stringent security regulations. In the next section we’ll see how the other approach allows login workflows to be standardized very quickly – days and weeks instead of months and years — without prolonging the transition phases for users or IT.
Unified passwordless MFA fast-tracks the benefits of universal IAM

Authentication requires precise interaction and agreement between users, applications, and directories. The “universal IAM” approach requires all managed resources from all identity platforms to be refitted to match the requirements of the designated universal IAM platform.
In comparison, another approach to consolidation delivers the same benefits by adding a flexible passwordless authentication layer that works with existing IAM platforms. Compared to continuing to support many (or even any) MFAs that still uses passwords, Octopus Passwordless MFA achieves the security, compliance, and operational efficiency goals associated with workforce consolidation in a fraction of the time.
Unlike other MFA platforms, the Secret Double Octopus (SDO) approach provides full use case coverage for on-prem and cloud applications without requiring IT to recode applications or rearchitect backend identity infrastructures all at once. A unified passwordless MFA gives the workforce a single, stronger, often easier workflow for all managed resources, and IT the flexibility to tackle infrastructure upgrades and unification at their own chosen pace.
Octopus decouples user login from identity infrastructure upgrades to give IT full control. The platform works with all leading vendor IAM platforms, including on-premises Active Directory and multi-vendor platforms. Octopus provides a unique mechanism for interfacing to modern applications such as SSO and FIDO as well as those built to work with passwords.
Businesses can prioritize and accelerate workforce security and user productivity and consolidate identity management when IT decides unifying the identity backend is mission essential. At that point, IT can move faster in recoding apps and rearchitecting identity infrastructure without having to coordinate with users around changing how they authenticate or updating shared secrets.
High-assurance passwordless MFA makes dollars and sense for financial services and other high-assurance sectors
The consolidation of disparate workforces presents an ideal opportunity for businesses with less advanced IAM practices to leapfrog to a phishing-resistant, passwordless approach to MFA – which is clearly where authentication is headed. Adopting unified, phishing-resistant MFA at the outset of system integration adds significant cyber protection for a relatively low upfront investment:
- Eliminates 80%+ of risk on day one, provided the solution can achieve significant use case coverage for phishing resistance.

- Poses low barriers to entry: The cost to deploy MFA remains low compared with overhauling entire identity infrastructures and equity in current MFA solutions will likely be low.
- Slashes overhead: Eliminates password reset efforts and 40% or more of all Help Desk calls on average.
- Enhances productivity. Traditional MFA piles additional steps on top of entering passwords which bogs down the login process for all users all day, every day. Eliminating the foundational step of entering passwords saves considerable time (not to mention aggravation) to make all users more effective all day, every day.
- Positively impacts cyber insurance premiums: Passwordless MFA meets best-practice identity management recommendations from CISA, NIST, MITRE ATT&CK and other federal, state, and industry authorities.
These benefits make unified passwordless MFA an ideal solution for the financial services sector and other industries favoring consolidation-based growth strategies.
Choosing the ideal solution to streamline workforce consolidation
In evaluating the right solution, IAM and security leaders should ask:

Does the solution deliver broad or complete use case coverage?
Most commercial or bundled MFA solutions don’t come close to satisfying the full range of services used in industries such as financial services and healthcare. Windows Hello for Business (WHfB), for example, only works with Windows platforms and not even all Windows applications. Workforces at leading financial institutions typically maintain some percentage of Macs, Linux, and legacy or custom systems, and even decades-old mainframe technologies.
The longer the companies have been in business, the more likely they are to have challenging legacy apps and systems running. A security upgrade also may be long overdue, and the individuals or consultants who designed systems are long gone. In other words: no one will want to mess with these systems until they absolutely must.
Does the approach go far enough toward stopping phishing?
Sadly, traditional MFA remains vulnerable to phishing. Savvy modern attackers devise more sophisticated and often automated techniques to impersonate or intercept legitimate users attempting to access legitimate resources. Even some passwordless approaches prove stronger than others at resisting impersonation, SIM swapping, man-in-the-middle (MITM), and MFA push-bombing attacks.
The Octopus platform includes a dedicated phishing-resistance suite of features that meets requirements outlined by authorities like NIST and CISA for comprehensive phishing-resistance.
Does the solution offer the highest assurance of identity verification?
In the past, moving to high-assurance authentication meant changing the enterprise’s applications and identity infrastructure to support X.509 certificates. The use of PIV and CAC hardware authenticators achieved traction among some government agencies, but don’t work for most enterprises due to the added cost and complexity, and added administrative burden on IT, particularly during times of high employee turnover such as M&As.
Unlike passwordless MFA solutions based on FIDO2 technology that only work with web-based resources, the Passwordless MFA solution offered by Octopus meets the full gamut of enterprise authentication needs – legacy apps, VPNs, remote access, and physically challenging environments.
Is this approach budget-friendly?
Workforce consolidation efforts associated with M&A may have a separate or dedicated project budget, making it possible to tackle long-overdue security updates. Several factors — along with broad use case coverage — can enhance a prospective solution’s payback analysis.
Will IT need to purchase, ship, and maintain new hardware tokens or other physical authenticators? Will the solution increase or decrease calls to the Help Desk? Will it streamline or complicate compliance audits and reporting?
Octopus delivers a “benefits-first” approach – see for yourself
M&A, MFA, and passwordless can be three separate journeys as mergers business, IT, and security leaders look to ensure consolidation won’t pave the way for breaches that destroy reputation. Early consolidation of identity practices delivers exponentially greater benefits out of the gate and over time.
Octopus unifies MFA, strengthens security improvements, and delivers a better user experience with substantially lower effort and expense than universal IAM. Broad use case coverage and deployment flexibility make it faster and easier to onboard additional groups throughout future M&As and other growth strategies as business priorities change.
Learn more, start now
For more information about passwordless MFA, watch this short video to learn how you can get started in about an hour. Or, run an ROI calculation on our Passwordless ROI Calculator to see how much you can save within the first year.