Passwordless Authentication Frequently Asked Questions (Part 2)
As more and more people become aware of the vulnerabilities of passwords, there’s an increasing interest in deploying passwordless authentication in the networks and services of organizations and businesses. However, one of the problems that most organizations face is that the software they use has been designed to work with passwords with default.
In the past months, we’ve received plenty of questions and queries regarding the deployment and use of passwordless authentication at different levels. Here are some of the most important things you should know.
Q: Is passwordless authentication an enforceable company policy?
A: The use of passwordless authentication methods like biometric and facial recognition has become a norm on mobile devices. But many organizations still struggle on deploying the technology on their corporate networks.
Whether you can deploy passwordless authentication on your network depends on the infrastructure that supports it. Fortunately, the developers of most prominent operating systems and authentication standards acknowledge the need to integrate the option of passwordless authentication into their software. Microsoft recently announced the support for passwordless sign-in on both its individual Windows products and networks running on the Microsoft Active Directory. Users will be able to use FIDO2 keys equipped with fingerprint scanners or fingerprint scanners integrated on their laptops to log in to their Microsoft and AD accounts instead of passwords.
Linux also supports passwordless SSH logins for several years now. Network administrators can configure their servers to use software keys in addition or instead of passwords.
This means that both systems can enforce a policy where users can only login with passwordless authentication technology.
Both directory services on Windows and Linux also support SAML authentication, an open standard that enables network administrators to implement their own authentication mechanism. This means you can integrate a mobile-based out-of-band authentication technology like Secret Double Octopus into your network.
Q: Can I use a passwordless solution with my current SSO?
A: Single sign-on (SSO) authentication is a good way to reduce the authentication attack surface, simplify the management of passwords, and provide a better user experience. The idea is to use one service (Google, Microsoft Azure, Active Directory, Amazon AWS…) to sign in to multiple accounts.
However, many organizations would also want to be able to integrate the convenience of SSO with the added security of passwordless authentication. Most prominent SSO technologies are based on SAML, which is flexible on the authentication technology.
Secret Double Octopus provides a passwordless SSO technology based on SAML that organizations can implement into their online services. It also has a passwordless implementation for several popular SSO technologies, including Google’s G-Suite and Amazon’s AWS.
Q: Will I be able to replace “service accounts” with passwordless authentication?
A: No, In Microsoft Windows, service accounts are accounts that are explicitly used to run services in the background. All versions of Windows come with a few default service accounts such as Local Service, Network Service, and Local System, which have different levels of access to local and network resources. These service accounts are simple to configure and use but are typically shared among multiple applications and services and cannot be managed on a domain level.
For organizations and users that want to customize the security of various services and applications, they can use Managed Service Accounts like CyberArk, which provides better administration and password management.
You can further enhance the security and ease of use of your Managed Service Accounts by integrating a passwordless authentication technology with your AD installation. This gives you the flexibility of managed service accounts plus the convenience of passwordless authentication.
Q: Is passwordless authentication compliant with regulatory standards?
A: In the past years, regulatory bodies have come to understand and acknowledge the weaknesses and security threats associated with the storage and use of passwords. That’s why they’re constantly raising the bar for the minimum requirements of passwords (length, complexity, encryption, change cycles) as well as making it mandatory to add two-factor authentication in many settings.
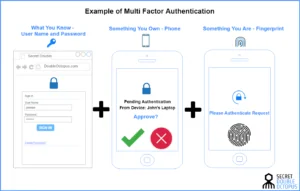
The NIST, the body that sets technology standards in the U.S. and acts as a point of reference for many other countries, requires that in many settings services secure user identities through multi-factor authentication. This means the service must support at least two of the following:
- Something you know (passwords)
- Something you have (mobile device or FIDO key)
- Something you are (biometric data)
In some settings, such as financial service, the standards body explicitly requires the use of biometric data as one of the authentication factors. This means that a technology such as Secret Double Octopus, which combines out-of-band mobile and biometric authentication, is a good choice to make sure your organization is compliant with security standards and regulations while also using convenient, user-friendly technology.
Q: Is passwordless authentication user-friendly? What type of pushback should I expect?
A: Obviously, using passwords, which are becoming increasingly hard to manage and too complex to remember, is much more difficult than swiping a notification or pressing your finger against the fingerprint scanner of your phone.
A recent survey by Secret Double Octopus gathered from employees of medium (1000-5000) and large (5000+) enterprises, found 81 percent of the respondents believe that passwordless authentication technologies such as Face ID are trustworthy and 91 percent think it’s easy to use. Most would also prefer to use a passwordless authentication technology instead of the traditional username/password combination.
Those figures speak to what users prefer. Also, from the organization’s perspective, it is much easier to manage and secure passwordless identities because there’s no need to store and encrypt secrets. Also, given advances in mobile device technologies, most smartphones already support passwordless authentication, which means, for the most part, organizations don’t need to invest in the purchase of new hardware because their employees already have everything they need to enroll on the company’s new authentication technology.
Q: Can I implement a passwordless solution at the server level?
A: Both Windows and Linux support passwordless authentication. In a 2018 update to its Active Directory LDAP service, Microsoft added native support for passwordless authentication through FIDO2 keys. This means that with the proper server-level configurations, AD users can walk up to any domain-connected workstation and insert their key to log in to their accounts without making changes at the machine level.
Linux also has native support for software keys, which can replace passwords. When passwordless authentication is implemented on a Linux server, users can remotely login to their SSH consoles by presenting their software key instead of typing in their password.
Also, organizations that want to use security solutions like Secret Double Octopus can use the SAML implementation of the technology which integrates with their respective server technology. This enables organizations to use the added benefit and security of SSO and mobile authentication on their networks.