We see it everywhere: Users tired of having to think up, remember, and rotate passwords just to get what they need. We even have terms for this authentication frustration, like “friction” and “MFA fatigue,” from entering more one-time passcodes (OTPs).
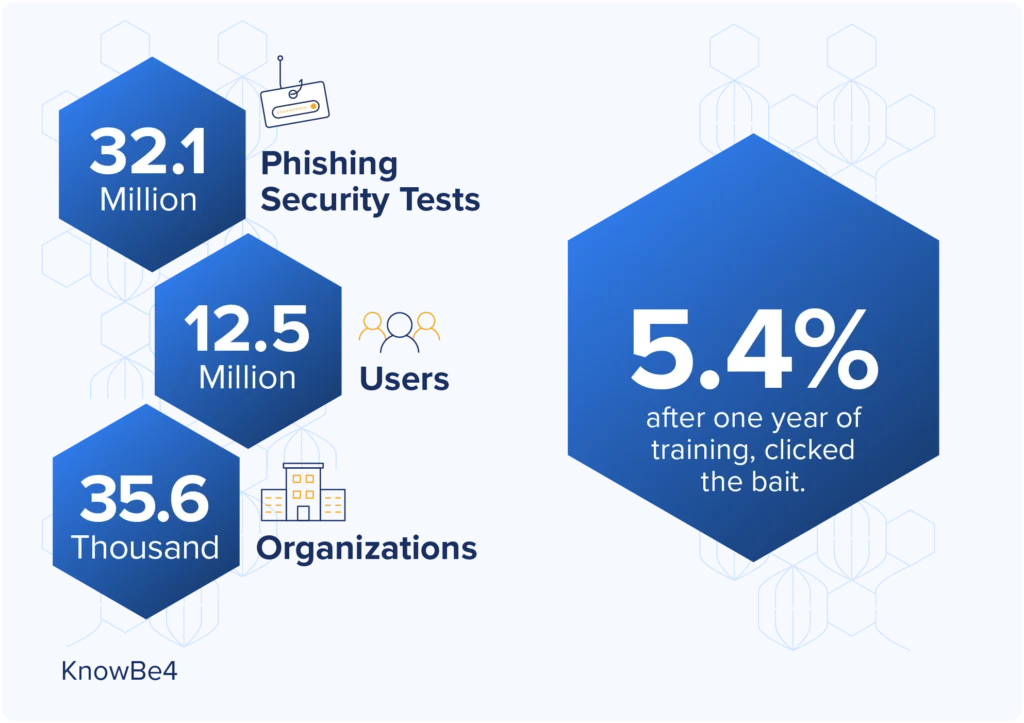
IT leaders don’t like passwords either, or at least they shouldn’t since credentials factor into 80% of data breaches. And MFA can’t stop phishing.
“But enough about users . . .”
While less grumbling and fewer breaches makes life better for IT in general, do the benefits really outweigh the time and trouble it takes to get there? The short answer is: yes. But when? And how?
As we’ll see in this book, IT stands to gain quite a bit from passwordless multifactor authentication (MFA)—we actually believe IT is the real big winner—as long as IT controls the journey. Some pathways are more work than others.
It is a hard pill to swallow, but the only thing separating an attacker from your crown jewels is an eight- or twelve-character secret that has proven to be easily exploited.
Users have spoken…They are not happy with MFA

The Top 5 Ways IT Benefits
In this article and in the comprehensive eBook, we’ll look at the most compelling ways passwordless workforce authentication benefits IT:
- Gets users out of password management—puts secrets solely in the hands of IT
- Keeps IT infrastructure modernization programs agile—IT stays in control of Zero Trust and passwordless journeys without ongoing user coordination
- Delivers rapid payback on identity modernization
- Slashes the attack surface, buys down cyber risk
- Checks the box on phishing-resistant mandates and cyber insurance criteria
But first, here’s a quick update on the state of passwordless MFA—what it means, what it does, and what it takes to get there.
Why passwordless MFA for the workforce?
Multi-factor authentication as we know it takes us beyond the realm of what users know, namely usernames and passwords that can be forgotten, leaked, or stolen. Adding steps like OTPs and device-bound biometrics means they also must have or be something, like a mobile phone or PC, or the individual with the right retina, voice, or fingerprint.
Traditional MFA effectively piles checks and balances on top of passwords, making authentication somewhat safer, exponentially more annoying, and still not good enough to stop phishing.
If traditional MFA can’t stop adversaries’ most popular and lucrative attacks, one obvious next step is to remove passwords from the authentication equation entirely
“What’s driving passwordless MFA?”
What drives everything? User experience, risk, cost, and compliance. In Chapter 3, we’ll see exactly how, done right, passwordless MFA meets three key objectives:
Enhance user experience (UX) and productivity
SDO estimates workers may waste 15 minutes a day simply authenticating into devices, sites, and services—a serious productivity hit when you multiply it by a large number of users (not to mention the time they waste calling IT to help reset credentials).
Threats and risk
Even as employees get better at spotting fake emails and spurious sign-in pages, security’s harsh truth still applies: traditional MFA can’t stop phishing.
IT can’t count on failing security awareness training that pushing the blame on users. IT needs to defend everything while adversaries just need one user to type one password in one wrong place.
Even with MFA and OTPs, authentication remains vulnerable not only to phishing, but next-generation “man in the middle” (MITM) attacks in which adversaries trick users into entering keys and OTPs into fake log-in pages so they can turn around and use them to access the real sites.
“Why isn’t MFA unphishable?”
Short answer: Because most methods still contain passwords, the secrets that can be lost, leaked, or stolen—i.e., phished. And the passwords are still managed by human users
Regulations and compliance
When businesses digitalized virtually overnight in 2020, remote work sparked a barrage of cyberattacks against employees, supply chains, and critical infrastructure. The damage prompted the Biden administration and other governments to set forth new mandates for adopting Zero Trust policies that include, among other things, “phishing-resistant MFA” by the end of Fiscal Year 20241.
Many other agencies and authorities worldwide issued similar mandates calling for tall change in short order.
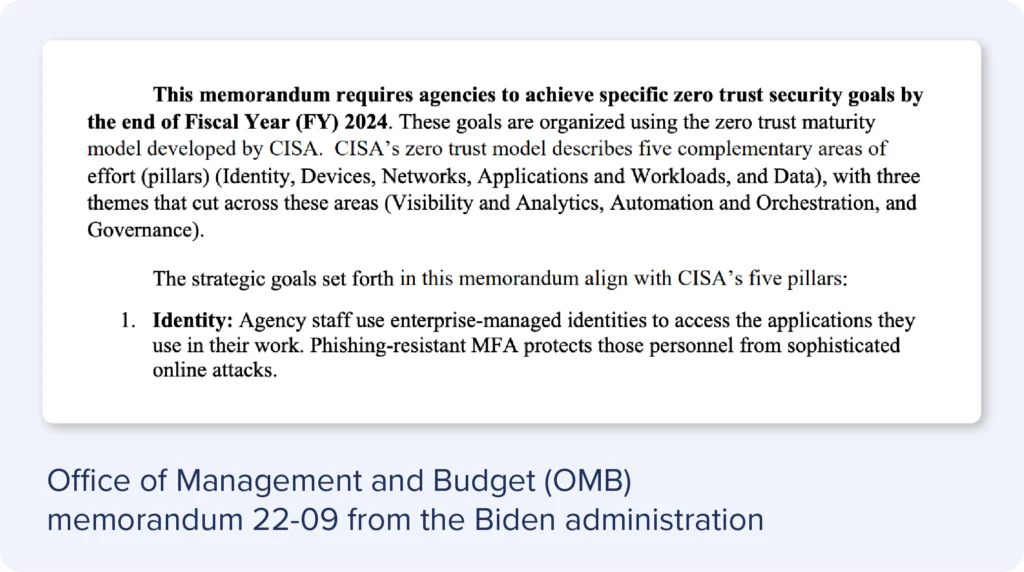
- M-22-09 Moving the U.S. Government Toward Zero Trust Cybersecurity Principles, https://www.whitehouse.gov/wp-content/uploads/2022/01/M-22-09.pdf ↩︎
“Aren’t we already passwordless?”
Yes, and no. Things like single sign-on (SSO) and identity provider (IdP) portals deliver a “passwordless like” experience. Now users can access various sites and applications for some length of time without reauthenticating. But eventually, SSO, IdP portals, and even PC-based biometrics all require passwords, like during updates and restarts. Passwords get used less often, which means users may choose things that are easier to remember and misplace or forget them more frequently.
Less annoying perhaps, but still not phishing-resistant or even really passwordless. Which begs the question . . .
Users never create, remember, or expose passwords. Instead, they prove their identity to Octopus using stronger passwordless methods for every access.
On the backend, Octopus replaces the user’s directory password field with a machine-generated token that is automatically rotated on your schedule. Then Octopus orchestrates user access to IT-managed apps and services.
So, how do we get there?
The Cybersecurity & Infrastructure Security Agency (CISA) lists as options for phishing-resistant passwordless MFA:
- FIDO/WebAuth authentication used primarily with websites
- Public key infrastructure or PKI-based approaches such as X.509 certificates
As we’ll see in the ebook, SDO’s approach adds a third dimension to extend and accelerate adoption. Unlike FIDO and certificates that require applications and directories to fit their integration requirements, Octopus is a passwordless MFA approach that works with your existing applications and identity infrastructure. No change required.

The Top 5 Ways IT Benefits from Real-world Passwordless MFA
1. Take password management away from users
While everyone agrees we’re better off without them, passwords themselves aren’t really the problem. Password management, and the fact that it remains user-driven, causes the real trouble.
Going passwordless takes users out of the identity management game and shifts guardianship of potentially dangerous secrets over to IT, where it belongs. This simple, profound shift becomes a gift that keeps on giving.
Eliminate password Help Desk calls
Research shows that on average:
- 40% or more of all Help Desk calls involve passwords
- Help Desk calls last 8.5 minutes and cost between $25-70
- Users call the Help Desk 8 times a year due to account lockouts
- It takes 9 minutes for users to refocus after calling Help Desks
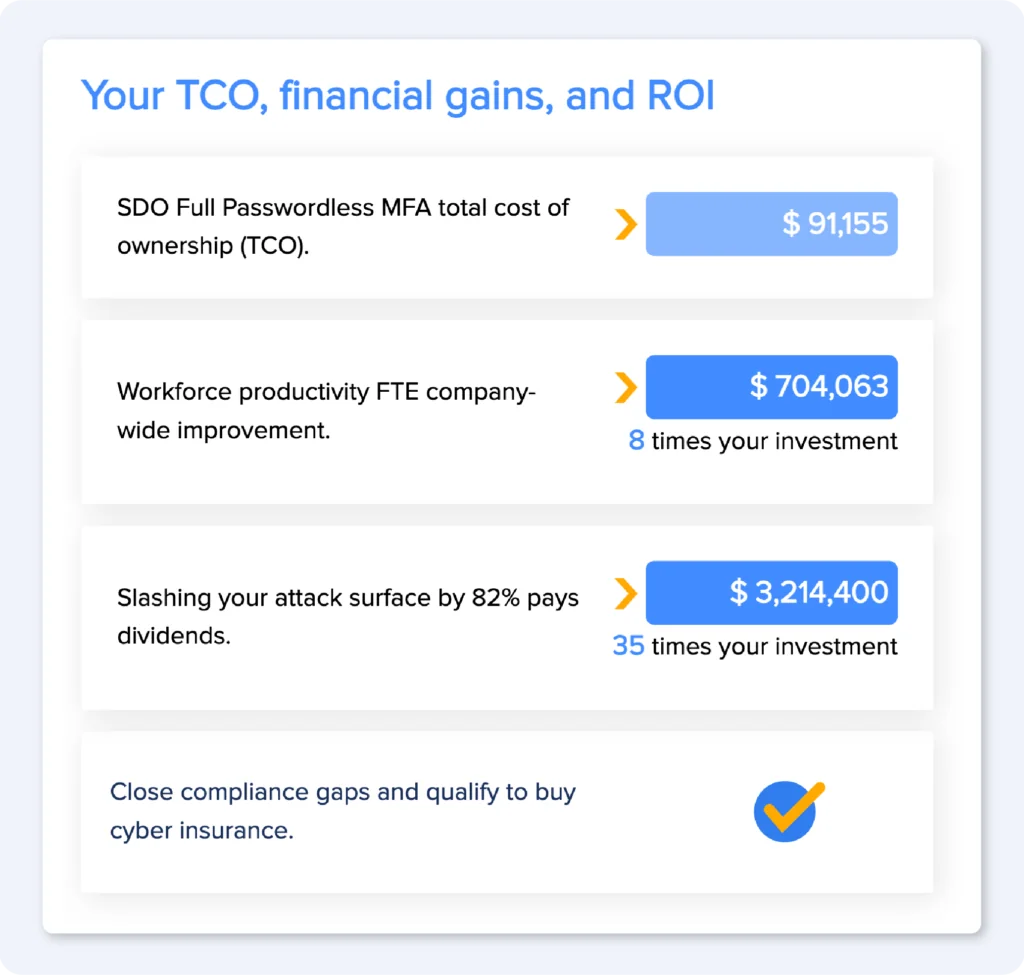
Plugging these values into our Passwordless ROI Calculator, SDO concludes the average company with 1,000 employees would save nearly $150K (and innumerable headaches) per year by eliminating passwords from user MFA.
This savings alone goes a long way toward paying for investments in enterprise-class passwordless solutions, but the real value comes from freeing IT experts to do expert IT things (that may or may not involve hostile/panicked users).
2. Fast payback and a 25X ROI
Other financial benefits include:
Reduce rotation costs
If your IT department has users change passwords every 3 to 6 months, rotation cycles consume considerable resources. Without user coordination to prompt, chase, and help users make it happen, password rotation happens with the click of a button.

Make users more productive
We practiced typing in passwords—regular ones, not the type that meet elaborate new schemes—and found it takes about 15 seconds. From there, we calculated that if an employee does that many times a day, they spend about 5% of their time simply authenticating.
After a year, eliminating passwords from user-side authentication translates into productivity gains worth roughly $800 to an average organization with 1,000 employees. Users get time back, IT gets the credit.
Save nearly $2M
In The State of Workforce Passwordless Authentication, Ponemon found companies could ultimately save nearly $2M per year using next-generation passwordless MFA.
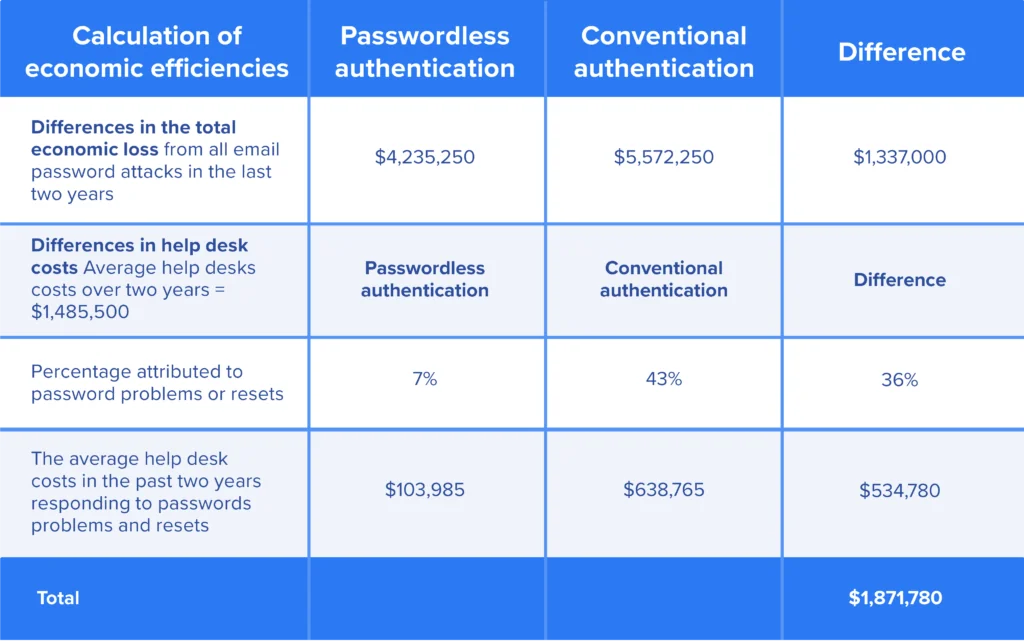

The SDO ROI calculator estimates even greater potential for financial gains 9X from productivity gains and another 25X overall return on investment (ROI) improvement from buying down security risk.
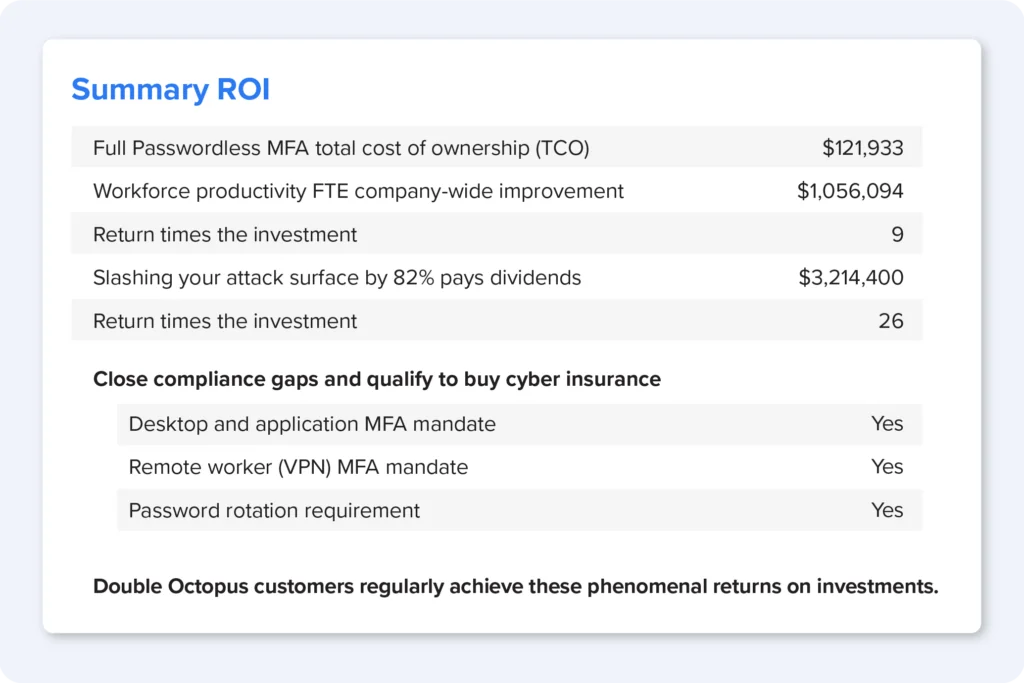
3. IT stays agile and in control
When your team is ready, IT can modernize and migrate your identity infrastructure to PKI and FIDO2 with no dependencies and no disruption to user activities whatsoever. With solutions for password-centric environments as well as FIDO2, Octopus provides a versatile path to phishing resistance, Zero Trust, and ultimately, Passwordless Everywhere.
Maintain simple, secure fallback
Even with smartcards, most workforce approaches to passwordless authentication maintain passwords as a fallback. The secrets typically get rotated once a year, which is less disruptive than four times a year, but keeping users enmeshed in the process still adds risk.
The SDO approach includes versatile machine generated tokens, that replaces directory password entries as a fallback, but rotation on the backend prevents them from ever being exposed to users, the Internet, or even IT teams themselves. Users don’t remember passwords, but they can self-service retrieve the token for emergency or unusual cases after strong authentication has been completed.
Our projected savings of $2M per year includes dramatically buying down cyber risk based on the following assumptions:
- 50% of companies experience a cybersecurity breach every year
- The average breach costs $4.2M by the time organizations fully recover
- Credentials factor into 82% of breaches (according to Verizon Data Breach and Incident Report)
Simply removing credentials from user authentication effectively slashes your digital attack surface by 80% and reduces the likelihood, frequency, and cost of recovering from breaches. The average company stands to buy down $1.7M of cyber risk per year.
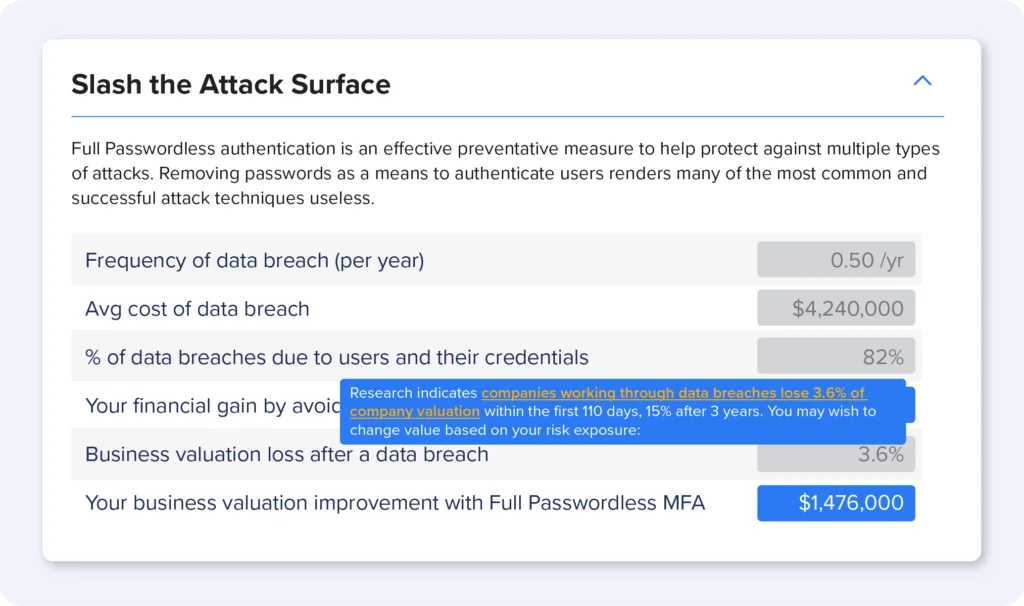
Your security posture and ROI also improve as passwordless MFA helps:
Safeguard the brand
Perhaps even more valuable, research shows public companies lose 3.6% of their brand valuation 110 days after a data breach, and as much as 15% after three years. Smaller enterprises and their brand reputation may never recover at all.
Lower insurance premiums
Insurance premiums will strain the budget faster and farther than regulatory mandates. Being able to prove you have phishing-resistant strong authentication in place will help satisfy requirements and best practices for securing and proving the identities of desktop, remote work, and privileged access users.
Uplevel cyber skills
Suffering fewer breaches that must be investigated, contained, and learned from leaves more IT and SecOps cycles available for threat hunting, threat modeling, breach and attack simulation, red and blue team exercises, and other high-impact initiatives. More stimulating jobs help you retain premier talent and leave companies safer at the end of the day.
We’ve seen how passwordless multifactor authentication:
- Takes “what users know” out of the equation
- Shifts IAM to IT
- Eliminates MFA fatigue
- Saves users valuable time every day
But perhaps best of all . . .
Stop feeding the phish
With the application-by-application approach, cloud stuff usually go passwordless first. In reality:

How can IT check the box when 25-50% of users are still setting and forgetting the same passwords to access even a small set of applications over and over? Eliminating passwords from the user experience only satisfies the intent of Zero Trust mandates if you do it for all use cases and applications. Otherwise, you’re leaving plenty of phish in the sea.
De-coupling user authentication from backend infrastructure lets you check the phishing-resistant box now and re-architect your infrastructure to PKI when IT says so.
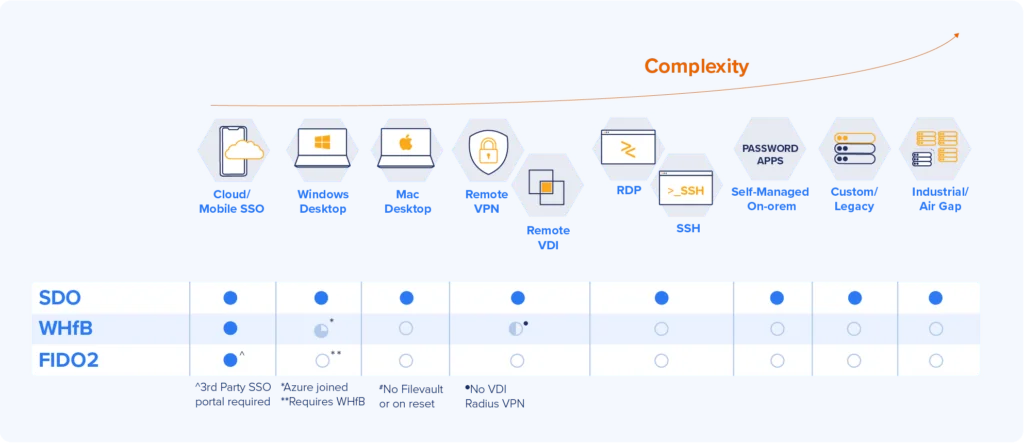
Windows Hello for Business brings a passwordless experience to cloud and mobile applications but cannot yet extend it to many critical business applications. The Octopus platform extends high assurance passwordless MFA enterprise-wide.
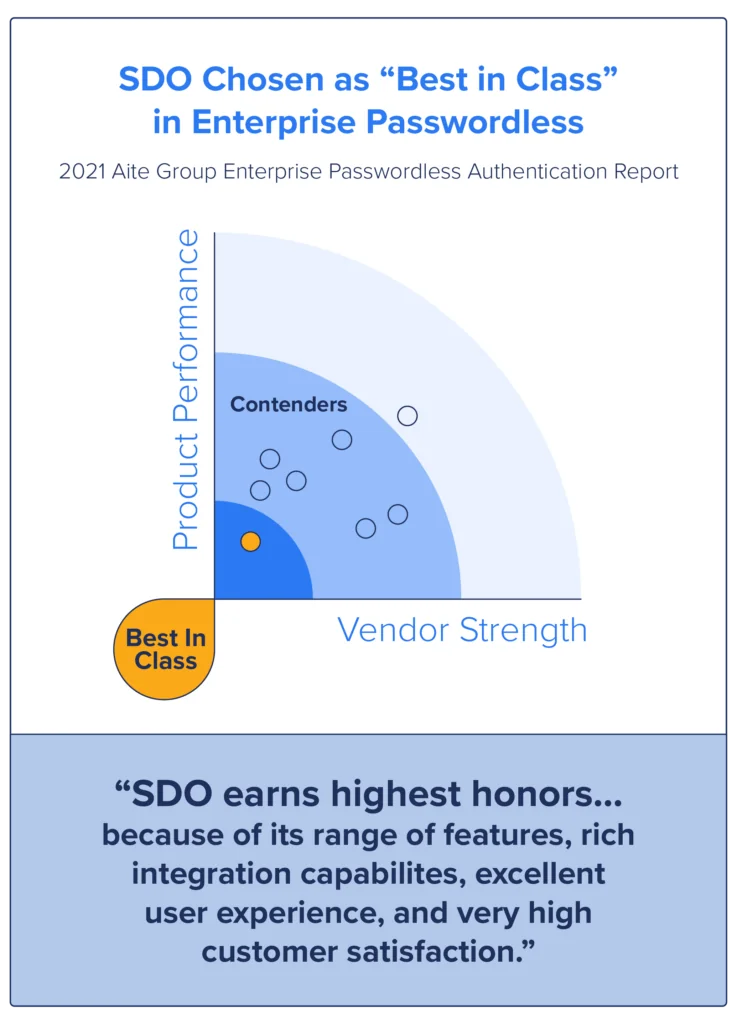
Who is SDO?
Founded by renowned cryptography researchers and cybersecurity engineers, Secret Double Octopus leads the charge to eliminate user passwords from the authentication equation while keeping IT in control of the journey. More than 100 enterprises worldwide use our Octopus SaaS platform to free users and IT from having to choose between security and convenience now and into the future.
Our “changeless change” approach delivers:
- Password-friendly passwordless
- Work with your existing applications and identity infrastructure
But enough about us . . . Make your life easier today.
Run your own calculation
We’ve included sample calculations from our Passwordless ROI Calculator through this book, but individual risks and regulations vary by company, size, IT budget and industry.
Get the complete story
Read the whole ebook for more insights on how IT wins with passwordless MFA or Get a personalized demo.