Just a few years ago, biometric logins were the stuff of science fiction and technophiles. Today, the market has produced a slew of tools that have made biometrics available for the common user.
Microsoft’s “passwordless-experience” solution, Windows Hello for Business (WHfB), is one of the industry’s most widespread authentication platforms designed for enterprise-wide use. Like any of the Seattle giant’s solutions, it’s a great point to start, but does it really deliver what large, complex enterprise environments need?
Let’s start with the basics:
What Does it Do
Released in 2015, Windows Hello gave Windows users an alternative way to log into their devices and applications, eliminating tedious passwords. It is a tri-option technology, offering facial, retinal, and fingerprint recognition.
Centrality and Control
The pros to Windows Hello for Business are the system’s scalability and the centralized management it gives to company executives.
Windows Hello for Business took the Hello idea (Biometric framework) and bundled it with management tools and enforcement techniques to ensure both a uniform security profile and security posture that encompasses the whole enterprise. To accomplish this, Windows Hello uses Group Policy or mobile device management (MDM) policies for management and enforcement, and leverages key- and certificate-based authentication in most cloud-focused scenarios for maximum protection.
So Windows Hello for Business did provide a workable administration scheme for businesses and was easily extendable throughout an organization. However, the creators left some serious drawbacks to the system, first and foremost relating to security and the range of use cases supported, all of which leave security and IT teams boxed in and only partially satisfied.
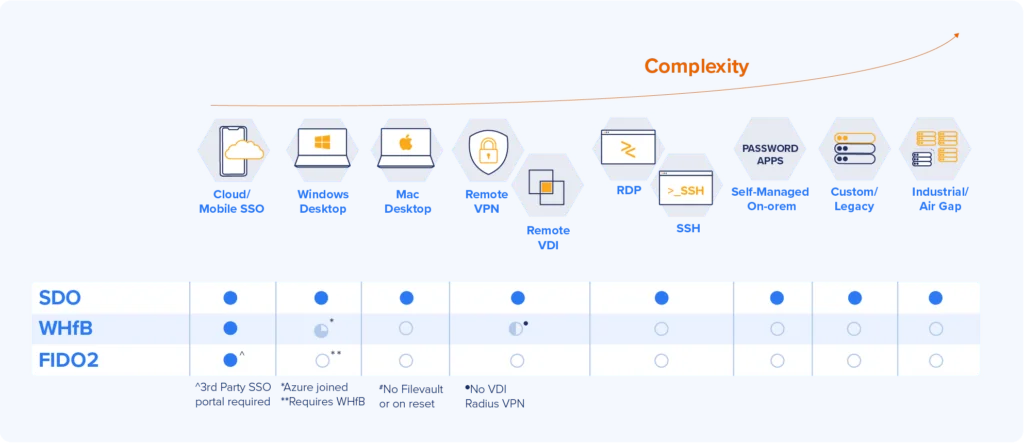
Is Windows Hello considered stronger than a traditional password?
Every security expert will advise adding Multi-Factor Authentication (MFA). Windows Hello for Business provides an easy yet limited MFA solution for Windows machines with compatible hardware or dedicated added hardware.
The use of a private key that is stored over dedicated secured hardware is widely used in the mobile industry (Secure Enclave), the hardware component is not accessible via web access and provides a safe place to store biometric or pin number authentication data, making it much safer than a password stored on a hard drive, and immune to threats such as credential stuffing and tools like Mimikatz.
However, when it comes to the most dangerous part of any corporate IT system – user-managed passwords – WHfB doesn’t deliver much good news. Not only are those passwords still in place, but employees are less likely to remember them, and more likely to write them down, or simply forget them when a renewal is needed. The effects on the organization’s security stance and Helpdesk operation might be negative overall.
Limited Compatibility
To utilize Windows Hello for Business, a user must possess a compatible machine. If a given device will not support Hello, a user must purchase a peripheral accessory to add functionality–not a practical solution for implementing technology across an organization.
But that is only the beginning. Enterprise employees are commonly burdened with dozens or hundreds of accounts to different corporate apps, systems, and networks. Most of which will not be relevant for WHfB-based authentication. This means that the #1 threat factor – employee-managed passwords – is still in place throughout the organization, making employees miserable and security teams worried.
No Logins from Different Machines
The Windows Hello model also impairs the flexibility of workers by limiting the workstations or devices from which they can operate.
Hello’s authentication scheme works by pairing the unique physical attributes of a user with cryptographic keys. These keys are what replace passwords as authentication factors. The keys, in turn, are stored within specialized security hardware, or are encrypted in software, and are unlocked after authentication occurs.
The same applies to Windows Hello for Business secondary method.
For organizations uninterested in biometrics, Windows Hello also supports PIN usage. When the user enters the PIN, it is not transmitted over the network, rather it’s matched to pre-stored keys. The fact that the keys are stored on the machine itself means that the user cannot authenticate using any other device.
No Escaping PINS
Interestingly, many users get the wrong idea on this point. They assume that the PIN requirement on Hello can be completely disabled and utilize face and biometrics only. The fact is that this is not possible on Hello’s platform. The system was designed for a “fallback” method in a scenario where the use of biometrics isn’t possible. The PIN is that method. This means that there is no option for disabling the PIN credential for a particular user.
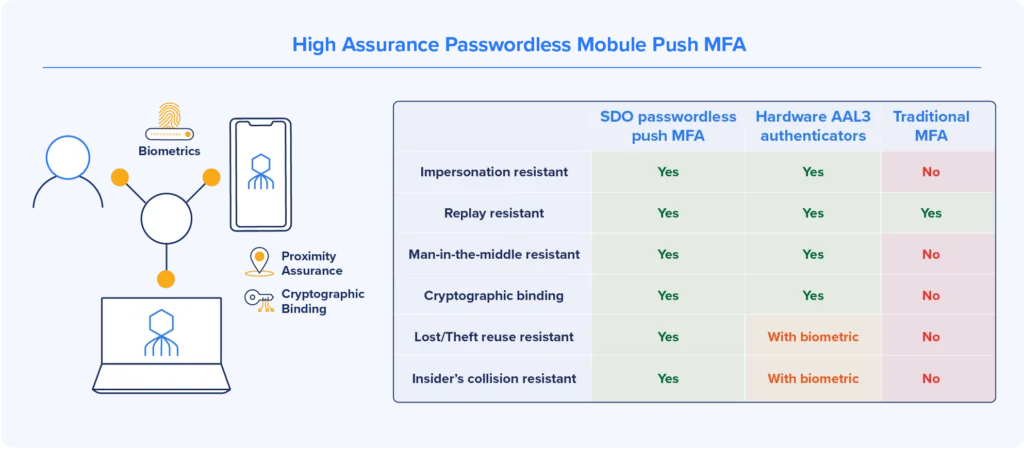
Octopus’s Solution – Passwordless Means No Passwords
The passwordless MFA technology employed by Secret Double Octopus addresses all of these security, usability and implementation challenges.
The fully scalable platform is compatible with all of the common operating systems including Linux as well as iOS and Android.
The Octopus Authenticator requires no dedicated software and turns users’ personal smart devices into mobile authenticators.
Additionally, the platform also allows for the off-workstation use of private keys, giving workers the flexibility to operate across the entire enterprise.