Logging in used to be simple, almost too simple. So, IT leaders raced to add a second, third, and even fourth step to the authentication process—and now it’s too complicated. Users hate the extra steps, Help Desks get bombarded with password reset calls, and MFA hasn’t stopped the phishing that leads to ransomware and other nasty attacks.
Combined pressure from ransomware attacks, new government mandates, and rising cyber insurance premiums makes phishing-resistance a growing priority but all passwordless approaches are not created equal. This blog exposes the fundamental flaw in today’s MFA and how you can make sure your approach delivers on its foundational promise: Zero Trust identity and phishing-resistance.
We’ll cover:
- Why traditional MFA doesn’t stop phishing—and how it can
- The fastest way to become fully phishing-resistant
- How to keep IT in control at all times!
To learn more, download the eBook, Got Phished? How to Get MFA Right the First Time now.
Why IT needs a new MFA strategy

Regulators turning up the heat
Businesses worldwide face federal and industry mandates for Zero Trust security postures and phishing-resistant MFA:
- Memorandum 22-09 from the Biden administration’s Office of Management & Budget (OMB) mandates phishing-resistant MFA for the government supply chain by 2024
- De facto cybersecurity frameworks like MITRE ATT&CK stress phishing-resistance
- Cyber insurance discounts for demonstrating phishing-resistance won’t lag far behind

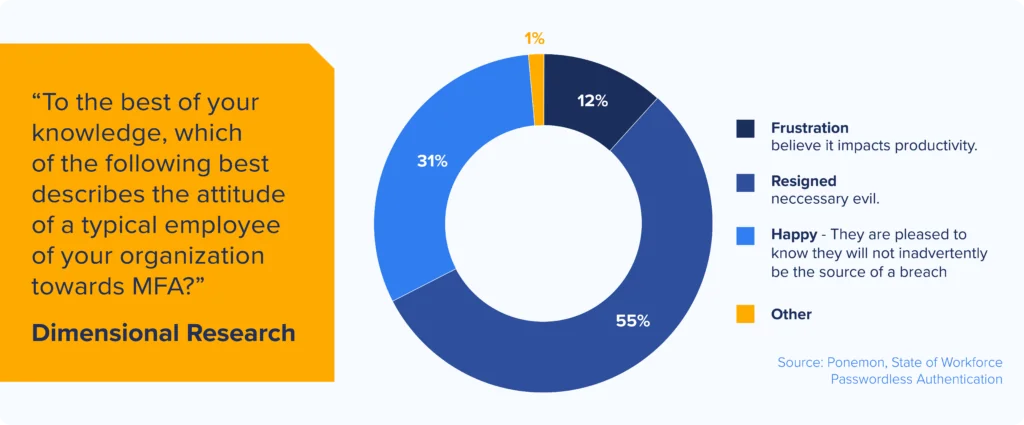
User frustration with MFA is off the charts.[i] Modern MFA layers a wide range of steps and techniques into the user login process: Physical hardware tokens, smart cards with X.509 chips, facial scanners, thumbprint readers, voice recognition all may be part of the process.
The more complicated we make the login process, the more users (and IT) resist MFA, with good reason:
- Users spend up to 5% of their time, about 20 minutes a day, just authenticating
- Up to 50% of Help Desk calls still involve credentials—to the tune of over $1 million per year in lost productivity
- Costs go up as IT buys, ships, and maintains smart cards, hardware tokens, and biometrics readers across an enterprise workforce
Education doesn’t cut it

Extensive testing by KnowBe4 found that, even after extensive training on how to recognize phishing scams, 5% of users still took the bait.
But the biggest problem with MFA as we know it is:
Traditional MFA can’t stop phishing—but passwordless MFA can
Attackers continue to innovate new tactics, techniques, and procedures (TTPs) to get around traditional MFA. And, traditional MFA continues to be built on a foundation of passwords—the perennial threat vector that leads to serious breaches.

MFA as we know it doesn’t stop phishing because it continues to use credentials — the highly vulnerable “something users know”—as factor #1 in verifying identity. Today’s MFA adds stronger pillars based on “something users have,” typically their phone or PC, and something users “are,” verified using biometrics.
Piling on more steps will never be enough to check the box on phishing-resistance. The one obvious way to bridge the remaining gap is to eliminate user credentials and password management from the authentication equation entirely.
A passwordless approach stops phishing — and man-in-the-middle attacks
Passwordless MFA stops phishing campaigns aimed at tricking users into giving up their credentials because, so far as users are concerned, credentials don’t exist. The right approach also stops man-in-the-middle (MITM) attacks that start with phishing.
Attackers sit between a legitimate site and a false copy. Attackers send phishing emails prompting a user to log into the real site and steals the information either by recording the session or capturing cookies and hijacking the session.
The ultimate proof that we need to take people out of the process, MITM attacks succeed even when users do nothing wrong. Several types of MITM exploits include:
- Campaigns that use physical proximity to lure users to fake unsecured Wi-Fi hotspots in places like coffee shops
- “Man-in-the-browser” (MITB) attacks where phishing emails prompt users to click links and install malware that records data sent between the victim’s device and specific sites
- SIM swapping exploits where cybercriminals impersonate users, answer security questions, and ask mobile carriers to reassign cell phone numbers to a new SIM card that lets them access victims’ data remotely
- MFA prompt / push bombing / MFA fatigue attacks that use social engineering and leverage the fact that MFA bombards users with verification prompts until they give in and approve requests
Removing passwords takes the phish out of the sea
A Passwordless MFA solution satisfies the intent of Zero Trust and phishing-resistant mandates—and will soon be a bonus for cyber insurance premiums—because it actually stops phishing (and the breaches that follow). CISA, NIST, MITRE ATT&CK, and other mandates and security frameworks all prescribe phishing-resistant MFA.
The right approach improves user experience (UX) and gives IT more, time, flexibility, and budget to modernize identity and access management (IAM). In the absence of a clearly defined standard, CISA lists two options for implementing phishing-resistant MFA:
- Public key infrastructure (PKI)-based
- FIDO/WebAuthn authentication
PKI add deployment friction
PKI uses a pair of public and private passkeys to pin devices for purposes of authentication. Client side PKI deployments add considerable cost and require significant retooling of applications and directory infrastructures. Updating just applications to use certificates, or Windows Hello for Business for authentication can take months, even years, and the disruption leaves dangerous gaps in enterprise-wide workflows.
FIDO only works for web
FIDO is great, because it is phishing-resistant. CISA calls FIDO, “the only widely available phishing-resistant authentication” but it’s only “widely available” for web or browser-based services. And Enterprises are so much more than just web apps. Developed by the FIDO Alliance and published by the World Wide Web Consortium (W3C), the WebAuthn protocol specified within the FIDO2 standard found rapid traction among leading browsers, mobile devices, and OSs.
Octopus Passwordless MFA lets IT course-correct — or get MFA right the first time
Passwordless MFA should deliver four powerful benefits:
- Less risk
- Less friction
- Less change
- Less cost

To this end, Secure Double Octopus (SDO) built a unique solution that raises the bar for MFA:
All applications become phishing-resistant
Otherwise, you aren’t phishing-resistant. Octopus delivers 100% enterprise use case coverage and secure remote access, anywhere, anytime, and from any device (even within air-gapped facilities).
Along with the inherent benefits of passwordless, the Octopus passwordless authentication platform delivers a suite of phishing-resistant capabilities that work with password directories.
IT gets to be the big winner
The Octopus approach decouples front-end authentication from maintaining directory infrastructures. This allows user login to become passwordless everywhere and makes it possible to start onboarding users in less than hour. Directories don’t need to be retooled or upgraded until IT feels ready.
A practical approach to phishing-resistant MFA, Octopus:
- Takes passwords out of the user authentication process and password management out of users’ domain
- Addresses all workforce use cases
- Disrupts modern MITM attacks
- Maintains or expands IT control
- Supports FIDO2 with a clear path to PKI
MFA works with mobile push
Users prefer the simplicity of push notifications because they’re fast and easy and don’t require external devices (though biometrics like fingerprint readers). IT likes the fact that there’s nothing to buy or carry — in other words, nothing for users to lose.
Change is hard. Octopus is easy.
SDO’s approach eliminates passwords from the user experience to protect your business and satisfy the intent of Zero Trust mandates to become phishing-resistant. We offer the only solution that can do this today for all enterprise use cases while keeping IT in control of their passwordless journey.
SDO’s approach achieves the full promise of passwordless MFA—reduced risk, cost, friction, Help Desk calls, and phishing—by enabling IT to achieve no passwords with no change. Octopus equips enterprises to:
- Achieve full passwordless MFA use case coverage – and phishing-resistance—out of the gate
- Save millions per year
- Improve both the user and IT experience
- Satisfy regulatory mandates and lower cyber insurance premiums

[i] https://go.doubleoctopus.com/ponemon-workforce-authentication-report
Post COVID19, the size of the global multi factor authentication market size is estimated to be $ 10,300 million in 2020, and is projected to reach $ 40,000 million by 2030. [2]
Curious?
To learn more about the unique advantage and differentiators of the SDO approach, download the eBook, Got Phished? How to Get MFA Right the First Time now.