Regulators, cyber insurance carriers, and cybersecurity best practices all highlight the need for strong authentication to stop ransomware and protect remote access. Recognizing that passwords lay at the heart of the problem, the FIDO Alliance outlined passwordless alternatives and standards for securing web-based applications – but most enterprises need more.
With new regulations slated for 2024, here’s a quick update on the benefits and limitations of FIDO2, the second iteration of the FIDO “standard.” We’ll look at how far FIDO can and cannot go in securing the enterprise, and how the Octopus passwordless authentication platform extends the intended benefits of FIDO authentication to on-premise apps and network services that drive the business.
FIDO outlines a passwordless future
NIST 800-63 (Digital Identity Guidelines), MITRE ATT&CK, and guidelines from CISA and other authorities all speak to the value of using multi-factor authentication (MFA) to verify identity. Formed in 2012 to develop a vision and define a path to a passwordless future, the Alliance site reads:
The FIDO Alliance developed FIDO Authentication standards based on public key cryptography for authentication that is more secure than passwords and SMS OTPs, simpler for consumers to use, and easier for service providers to deploy and manage. FIDO Authentication enables password-only logins to be replaced with secure and fast login experiences across websites and apps.
Led by Google, Amazon, Apple, Microsoft, and other industry giants, the FIDO Alliance developed WebAuthn technology to secure web or SaaS apps, and it does.
FIDO achieves phishing-resistance
Most businesses invest in MFA for two reasons:
- To strengthen identity verification for remote access
- To finally stop phishing that leads to compromised credentials and 80% of all security breaches
At the same time, organizations hope MFA will streamline the login process for workers to create a better user experience, and where possible, reduce the burden on IT and security operations. FIDO delivers on all fronts—when implemented the right way.
How it works
Solutions proposed by the FIDO Alliance use public and private key pairs and modern cryptography to link user devices, web sites or pages, and authenticators together in such a way that all three must be present for access requests to be granted. You can implement this triad in several ways.
Authentication might involve hardware keys or tokens or biometrics that verify user identity with things like voice, facial, or fingerprint scanning technology, but it’s the binding of these three elements together that makes FIDO so secure. Using biometrics and cryptography, FIDO provides high assurance that the person requesting access is who they say they are, requesting access to the right computer with a managed or approved authentication mechanism.
At the end of the day, FIDO delivers on the promise of phishing-resistance without creating “MFA fatigue,” and a passwordless approach makes things easier for IT as well. Research shows that getting rid of user passwords, and more importantly, password management by users, avoids up to 40% of annual Help Desk calls. That translates into massive savings and frees IT and security professionals to funnel more cycles and resources toward threat hunting and other preventative activities.
So far, so good, so . . .

Why don’t we have FIDO-based authentication everywhere?
The simple answer is: because FIDO2 doesn’t work everywhere.
Web not required on-premises
FIDO-enabled authentication only secures applications and systems accessed via the web using browser-based technology. Stopping Web-based phishing may indeed be the right priority as companies continue to support remote work on a permanent basis, but the Internet equals risk.
Requests from remote users connecting in through virtual private networks (VPNs) have to traverse the public Internet—where threat actors know how to hide—to access your business’s digital crown jewels. And even when legitimate users try to access resources located inside the building using a single sign-on (SSO) portal, they may be required to log into it via the VPN, which adds the element of exposure on the public Internet to an otherwise secure self-contained interaction.
FIDO can stop phishing campaigns from luring victims to spurious web sites to steal their credentials but can’t address most on-premises applications. Somewhat surprisingly, on-prem apps still account for more than half of all new software deployments by enterprises.
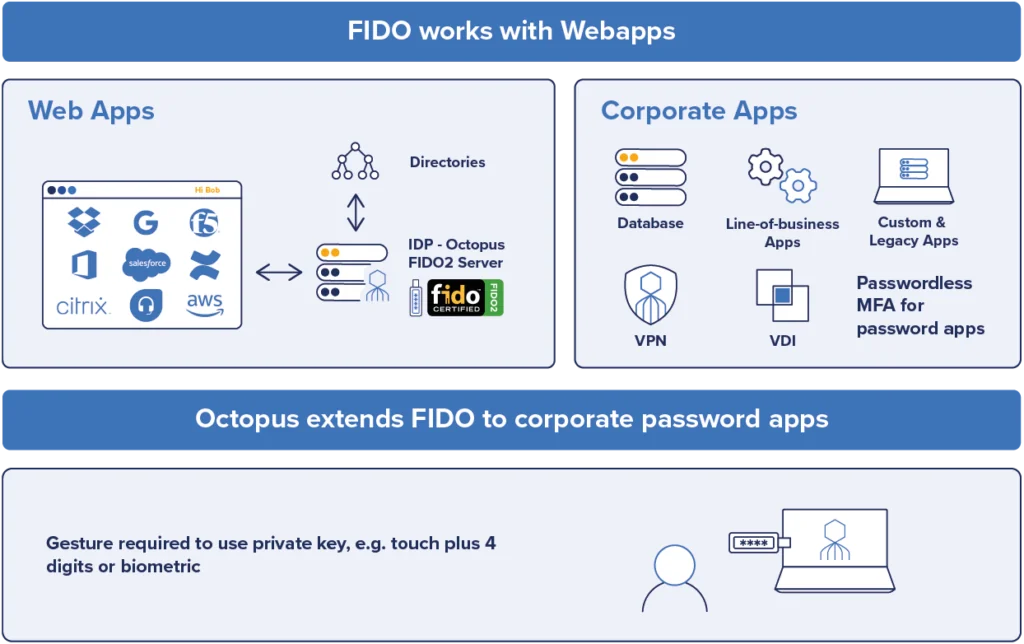
“On-prem” doesn’t always mean “legacy”
Current research findings show:
- 54% of business applications reside on-premises (Bloomberg)
- > 50% of new or current software sales are being deployed on-prem (Spiceworks)
These statistics bring IT leaders face-to-face with the harsh conclusion that, while FIDO delivers the end-goal of stronger authentication, it doesn’t do so everywhere, or anywhere close to enough.
“But doesn’t phishing only happen on the Web?”
Technically, yes. But the lateral movement that follows targets high-profile assets often residing on-prem. Many companies, particularly those involved with nations’ critical infrastructure, also have vendors and other third-party supply chain partners logging into on-prem systems remotely.
Enterprises need a FIDO or FIDO-like approach onsite to help detect, shut down, and prevent insider attacks, collusion, and lateral movement from ushering adversaries toward critical assets and data. This modern authentication requires a mix of push notifications, proximity assurance, sophisticated cryptography, and biometrics.
The question remains . . .
Even if FIDO adoption reaches a point where it secures the entire 50% of applications that are Web-based — and that level of coverage is a long way off yet — what about the other 50%?
Octopus Extends FIDO for Phishing-Resistant MFA Across the Enterprise
Secret Double Octopus built our passwordless MFA around three basic principles:
- Removing passwords and user password management stops phishing
- To be phishing-resistant, resist social engineering and human error, all apps need to be phishing-resistant
- Enterprises need to be phishing-resistant now
Like other passwordless MFA solutions that aim to stop phishing, the Octopus platform Passwordless MFA Solution supports FIDO2 to secure web applications and access. But unlike other passwordless methods, we also extend the benefits of passwordless MFA – and a FIDO-type approach – across the rest of the enterprise.
That includes delivering phishing-resistant MFA for Macs, as well as MFA for Linux servers, VPNs (which generally use Radius protocols), and LDAP-based systems on-premises. The Octopus platform covers the full range of legacy and new applications running and being deployed on-prem as well as air-gapped environments and other physically challenging locations.
Here are two examples of authentication using the Octopus and a FIDO key to a user portal and a VPN service:
Give the people what they want – a little push
Research shows users like the convenience of receiving push notifications to their mobile phones to complete authentication:
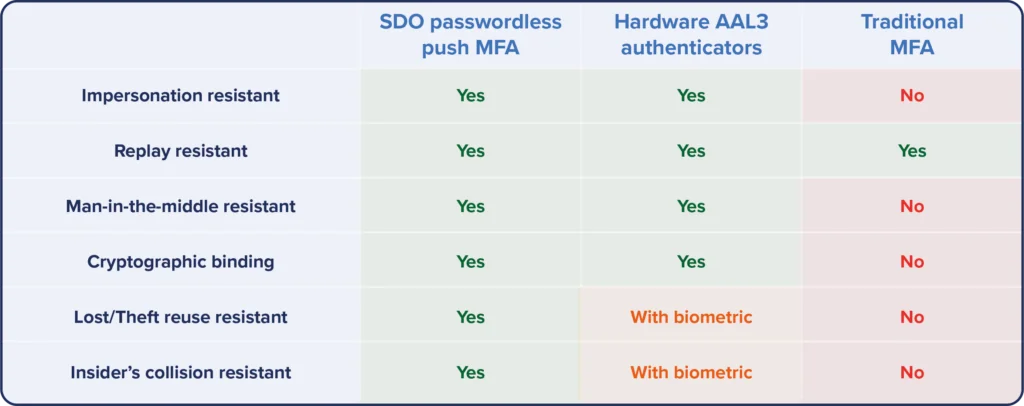
Even with push notifications, traditional MFA isn’t secure enough to be considered “high assurance” by industries facing the strictest authentication requirements. Here, Octopus elevates mobile push to the level of High Assurance using cryptographic key pairs and a first-of-its-kind new feature.
Our Proximity Assurance capability requires users to be within range of the workstations they’re attempting to sign onto and complete authentication using both a PIN sent via push and a biometric. This authentication workflow combines “what users have” and “who users are,” the two pillars of authentication deemed more secure than passwords (what users know) and regular SMS-based texts.
The takeaway: Octopus Enables FIDO-based Passwordless MFA Coverage Across the Entire IT Infrastructure
IT leaders protecting sensitive business data need 100% assurance that remote access requests are being made by authorized users from approved or managed workstations. Regular MFA that essentially piles more steps on top of passwords doesn’t resist impersonation and ‘man in the middle” (MITM) techniques used in modern phishing campaigns.
At the same time, FIDO-based Passwordless MFA, which can resist phishing, doesn’t go everywhere enterprises need strong authentication. Octopus accelerates the enterprise Passwordless journey by enabling IAM leaders to adopt FIDO2 for the web and achieve the same benefits across their entire IT infrastructures.
In September, SDO announced its selection as a 2023 SINET 16 Innovator, an award based solely on merit and the importance of the company’s vision and innovation. The award attests to the growing need for Passwordless MFA to secure the modern workforce and the unique ability of the Octopus platform to do so, on the web or on-prem, and anywhere else business might take place, Click here to get a demo of the Octopus Platform.