What is “credential stuffing”?
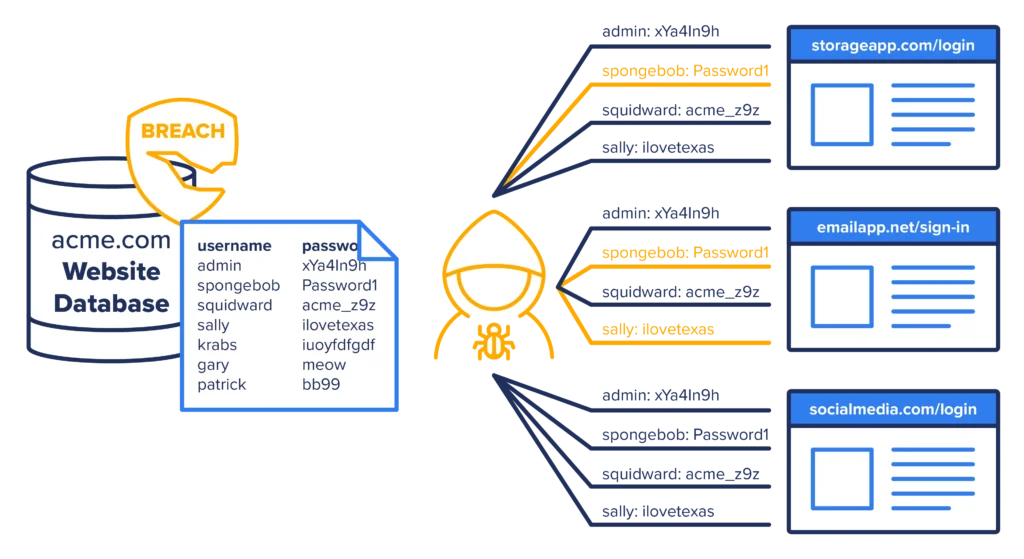
The term “credential stuffing” refers to the automated injection of stolen username and password pairs in order to gain unauthorized access to user accounts. Threat actors take ill-gotten credentials used to access one service and then use them to try logging into others. The two services do not need to be, and often are not related, meaning credential stuffing doesn’t only happen within a single organization.
An important enabler for credential stuffing is the tendency of users to reuse passwords across more than one application. As a result, compromised credentials from one application can be used to access other applications.
How credential stuffing works
Using automation tools, e.g., OpenBullet, large numbers of compromised credentials are automatically entered into an application (typically a Web application) until success is achieved. For example, a threat actor might obtain a username/password (UN/PW) combination from data exposed during a breach of a retail giant like Walmart or Target, take those same credentials, and use bots to attempt to log into Facebook, Instagram, Etsy, etc.
If they get a match, they then take the same compromised credentials and try accessing more sensitive, higher-security venues like crypto exchanges and trading sites. Once account takeover takes place, account data can be stolen, fraudulent transactions initiated, or the account can be used for other nefarious activities. Billing information, SSNs, balances, and other data can all be stolen.
Source: OWASP Foundation
Is credential stuffing an advanced form of brute force attack?
Yes, and no. Many discussions liken credential stuffing to brute force attacks. While both can be considered volumetric in nature (“if at first you don’t succeed . . .”), brute force attacks use automation to guess and cycle through random or statistically probable passwords.
In contrast, credential stuffing attacks start out with passwords already in hand. Brute force attacks try multiple passwords against the same target, credential stuffing tries the same UN/PW pair against multiple targets.
And from a defense standpoint, selecting challenging, hard-to-guess passwords helps stave off brute force campaigns, but makes little to no difference in deflecting credential stuffing since, however intricate users make their passwords, threat actors already have them, or a very close approximation, going in.
How do threat actors come by credentials in the first place?
Often, and in both typical and innovative new ways. The 2022 Verizon Data Breach Investigations Report (DBIR) cited credentials as the leading overall attack vector with stolen credentials factoring into nearly half of all successful breaches.
Along with tried-and-true phishing campaigns, research shows that, for all our investments in multi-factor authentication (MFA) and other defenses aimed at safeguarding the login processes, more compromised credentials are readily available for hackers to buy or barter than ever.
The endurance of credential stuffing suggests cybersecurity stacks should shift more focus from detection and response to prevention.

The real reasons credential stuffing attacks still succeed
It’s worth noting that CloudFlare estimates that only 0.1% of credential stuffing attacks actually do succeed, a relatively low rate as threat vectors go, but launching automated high-scale campaigns is still relatively cheap and painless. And as we’ve heard a million times, attackers only need one set of credentials to work once to ensure a profit or a good payday.

Technically speaking, credential stuffing attacks succeed because the credentials themselves are legitimate — they don’t trigger alerts within EDR, XDR, or MFA — and the initial breach of credentials might take weeks or months to discover. Not knowing that their data has been made public on the Internet or dark web, unsuspecting users see no reason to rush to change all their login information everywhere.
But the “real reasons” credential stuffing remains a popular threat vector are:
- Users still reuse passwords over and over
- Automated tactics, techniques, and procedures (TTPs) elude traditional defenses
- MFA doesn’t mean phishing-resistant
Let’s take these one at a time.
Users still reuse passwords
For all the investments enterprises make in educating users about security best practices and credential hygiene — not to mention in single sign-on apps — users still use the same passwords in multiple places. Inundated with requirements to supply complex passwords to different systems, users resort to reusing the same password across multiple accounts so that they can easily manage their credentials. This can cause major security issues when those credentials are compromised.
SecurityIntelligence data claims 85% of respondents surveyed admitted to reusing passwords on multiple sites. Even harder to believe, research shows users don’t even necessarily change passwords following a known breach. A 2022 SpyCloud survey based on 1.7 billion username and password combinations leaked in 2021 estimates that 64% of users kept using the same passwords exposed in one breach to log into other services.
Attacks elude traditional defenses
Login forms may automatically lock down a user’s account after X number of failed attempts from a single device. To get around this, bots used in modern credential stuffing may attempt to login from multiple devices with different IP addresses which is less likely to raise suspicion.
MFA can’t fully protect credentials
Now commonly found in both enterprise and consumer applications, multi-factor authentication or MFA represents a front line of defense against login-based attacks. Unfortunately, most MFA still uses passwords as its foundation or first factor in verifying identity..
If the would-be attacker already has the basic credentials, the second, third, or fourth factors (2FA, MFA) do indeed add more steps and hurdles for bad actors to jump through. That said, they’re getting much better at that.
Modern MFA fatigue, push bombing, and man-in-the-middle (MITM) attacks all succeed more easily when adversaries have a head-start in the form of credentials.
To summarize . . .
Credential stuffing still works because:
- We still use credentials
- Traditional defenses can’t protect them
This realization brings us to the heart of the matter.
How to stop credential stuffing
OWASP outlines 5 defense options to prevent credential stuffing attacks:
- Use multi-factor authentication (MFA)
- Create a multi-step login process that makes it harder for attackers to know whether credentials are valid or not
- Maintain IP blacklists that force attackers to constantly change IP addresses
- Use device fingerprinting to track the identity of connecting devices
- Disallow email addresses as user IDs making it harder to guess valid credential pairs.
In addition, companies can implement three common-sense strategies:
Defense Strategy #1: Keep working to stop password reuse
Password managers can be very helpful here. Password rotation helps but still leaves risky windows of time in which compromised credentials can be effective-Make each password unique and make them strong!
Defense Strategy #2: Improve detection
Another option is to define policies that prove more sensitive to upticks in login attempts through adaptive techniques. These methods include testing for geolocation of the requester and the authenticator, testing for cadence of access failures, or injecting additional verification to push cycles that deviate from normal access patterns.
Speeding detection helps with damage control and in preventing worst-case scenarios, but the smartest possible approach is one that aligns more closely with a Zero Trust cybersecurity posture.
Which brings us to Defense Strategy #3:
The ultimate solution to credential stuffing attacks: Do away with user passwords completely
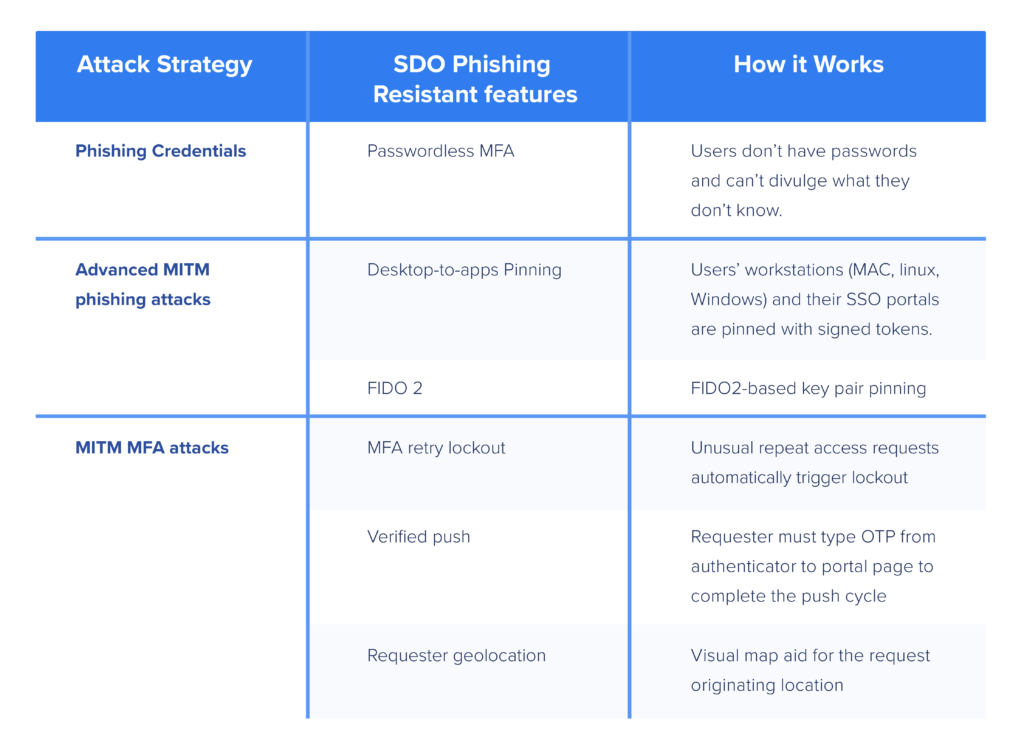
With governments worldwide issuing mandates for Zero Trust, phishing-resistant MFA, the idea of making MFA passwordless is getting more attention. The basic idea is to stop relying on passwords and other “things users know” that can be written down, stolen, shared, and overused in favor of secure, phishing-resistant combinations of “things users have” – the right device, key, or token — and “things users are,” verifiable with face, voice, fingerprint recognition and other biometrics scanning.
Passwordless MFA implementation models are nuanced and many prove far from complete in practice. To avoid going down the road and having to manage multiple solutions, or worse yet, rip and replace, look for a passwordless MFA solution that:
Works for all enterprise use cases: Completely needs to mean completely or your organization will still be susceptible to both phishing and credential stuffing attacks. Not to mention password attacks, MFA fatigue and MITM.
Works with passwords — behind the scenes: Passwords represent no danger if users never know them and they never appear anywhere. That can happen if you remove them from and decouple user authentication from backend directory infrastructure authentication.
Works with mobile push: Users hate MFA but they love the simplicity of getting a request to approve authentication sent to their mobile devices.
And above all:
Stops phishing: Any way you do it, getting rid of user passwords goes a long way toward stopping their credentials from getting phished — a long way, not all the way. Here’s where the nuances come in.
Some Passwordless MFA approaches do a better job than other of resisting modern, sophisticated MITM attacks designed to circumvent traditional MFA. To learn more about that, check out the blog.
Don’t get complacent
Credential stuffing, phishing, and other attacks that “still” succeed after 5, 10, 20 years or longer because we never learn Lesson No. 1: never underestimate risk from the human element. Password managers, MFA with mobile push, and passwordless user MFA all help to assuage the risk from the human element to varying degrees.
If we are imaging that getting rid of credentials altogether removes the attack vector still used in more than 80% of attacks, passwordless MFA warrants a serious look.
And, depending on how you go about it, you can start eliminating risk from the human element in about an hour- Don’t believe it? Watch now.