Most enterprises deploy multi-factor authentication (MFA) to keep data from being stolen and to keep their companies out of the headlines. For industrial manufacturers, the stakes may be higher. SDO recently sat down with Jonathon Gordon, Industry Analyst at Takepoint Research, to discuss the potential for phishing-resistant MFA to help manufacturers and other suppliers of critical infrastructure (CI) improve their security posture.
Having provided research and advisory services to the industrial cybersecurity sector for years, Gordon believes manufacturers can use identity – making sure those requesting access to corporate resources are who they say they are — as a modern cyber-defence strategy within security stacks.
“Identity-based access is emerging as a credible preventative defensive layer in the industrial sector,” Gordon says, “Tools like MFA have the potential to enable a streamlined approach, not only to checking the box on compliance but actually mitigating some industrial cybersecurity risks.”
Where some early adopters have been disappointed by aspects of MFA – added complexity, user frustration, and the failure of most solutions to stop phishing — industrial manufacturers find themselves uniquely poised to leapfrog other enterprises and get MFA right the first time with passwordless MFA.
Manufacturers face unique identity management challenges
Countries worldwide continue to issue mandates to improve the cybersecurity of their nations’ critical infrastructure. While these changing regulations encompass a wide swath of businesses, industrial manufacturers face their own distinct sets of both physical and digital challenges.
Safety vs. Security
Cyberattacks have the potential to devastate any business, but the stakes are even higher in critical infrastructure, potentially including loss of life and public safety. These companies face the same IT risks as those in other industries – data theft, ransomware, account takeover – but may need to protect access to operational technology (OT) systems as well. In OT, failure to secure operations might city-wide or regional power outages, disastrous nuclear meltdowns, contaminated water supplies, and the delay of first-responder services.
Safety and keeping SCADA, DCS, and other production systems accessible and running at peak efficiency clearly takes priority for automation engineers and plant managers. Changes needed to harden facilities’ cybersecurity posture may take a backseat or even be viewed as impediments to operational goals for worker safety and plant productivity.
Third-party risk
Many complex and specialized systems operate in industrial OT/ICS environments. These systems require installation, maintenance and support from product vendors and also from a cadre of third-party technicians, operators, and contractors who provide product/system support and maintenance due to their expert skill sets and in-depth knowledge. Most industrial enterprises cannot operate without this daily and often 24/7 assistance from professionals outside the company. “Reps from major providers like Honeywell and Siemens constantly need to service or patch systems on production floors and manufacturing plants,” Gordon explains. “It’s not unusual for large industrial providers to have 100 different vendors coming onsite or logging in remotely. The sheer complexity of having that many people come and go every day means no one really knows who’s doing what or even who’s authorized to do what.”
Looming federal and industry regulations
Industrial manufacturers, particularly those with government contracts, face a wide range of added regulations. Those topping the priority lists of many industrial manufacturers include:
United States Executive Order M22-09 (Zero Trust for Critical Infrastructure Sectors)
NIST 800-63 draft 4, phishing-resistant MFA
Local versus remote access
Like their counterparts in virtually all other industries, large manufacturers may use VPNs to enable remote access for users not physically sitting on the corporate network. These connections may include basic MFA but authentication still may begin with entering passwords that cannot stop phishing, impersonation, and other modern attacks on authentication.
“Engineering workstations commonly found at Level 3 of the Purdue model often run outdated versions of Windows, use shared accounts, and are left logged in constantly,” Gordon describes the risk. “Passwordless MFA represents unique challenges but also a significant opportunity to enhance security.”
Increased integration of IT and OT
Many manufacturing and utility companies have begun modernizing, which includes integrating cutting-edge “smart” and newly connected OT devices with modern and legacy IT systems. Newly heterogeneous environments may include access to a diverse range of industrial control systems (ICS) devices such as PLCs, RTUs, valves, and gauges
Once again, the sheer complexity and lack of unified visibility add new layers of risk as companies look to extend new and existing cybersecurity controls such as MFA to OT systems and devices. “Identity provides a technology-agnostic security overlay capable of safeguarding all devices and applications within these complex systems,” Gordon explains. “Whether it’s employees, third-party contractors, or OEM vendors, existing approaches to securing remote access can be significantly improved by integrating a passwordless MFA solution.”
Could CI move directly to passwordless MFA?
With or without the pressure of changing regulations, Takepoint believes many CI providers are holding their own cybersecurity postures to higher standards than ever before and looking to move the needle on prevention and cyber-resilience. Because manufacturing tends to lag behind other sectors in implementing leading-edge cybersecurity, fewer companies have made large investments in legacy MFA to date.
Where adoption is still in the early stages, security and risk management leaders evaluating MFA solutions stand to benefit from early adopters’ lessons learned and place the emphasis where it belongs out of the gate: on avoiding risk.

Passwordless MFA stops phishing
“MFA may be considered standard, but companies are beginning to realize the big difference between legacy and passwordless MFA is phishing resistance,” says Gordon. “If you’re not taking passwords into account, you’re not taking into account everything that’s reasonable to do to stop breaches. Passwordless MFA lets companies take entire attack paths focused on stealing credentials off table so they can mitigate and even prevent certain risks. Passwordless MFA is clearly something that should be considered as part of what’s reasonable.”
Reduces risk while “checking the box”
Noting that the term ‘phishing-resistance’ now appears in the language of numerous mandatory regulations, Takepoint expects identity to increasingly be viewed as a defensive layer with the power to augment traditional controls focused on securing endpoints or the network itself. “The right MFA solution has the power to change the outcome for security versus, or in addition to just checking the box on compliance,” the analyst observes. “For one thing, it enables organizations doing business in complex environments to use an overlay approach to address critical risk without having to make changes to the network.”
Minimizes cost and disruption
Octopus passwordless MFA represents a relatively simple-to-deploy and budget-friendly new layer of defence compared with legacy approaches like installing or upgrading to next-generation firewalls and other disruptive inline tools.
Moves security beyond detection
Security in CI largely centres on detection rather than prevention because companies hesitate to automatically block legitimate traffic that might trigger a false positive. “Some solutions show you that you may have a problem, and perhaps that you can’t ignore that anymore, but don’t actually solve the problem,” Gordon points out. “Passwordless MFA advances security operations toward mitigation by simply removing certain risks with a high level of confidence.”

Why Octopus?
Only the Octopus passwordless MFA platform significantly improves cybersecurity across IT and access to OT without creating new risks or adding undo cost, complexity, and friction. SDO offers an end-to-end solution for IT and OT that allows companies to roll out phishing-resistant MFA and progress through their passwordless journeys at their own chosen pace.
SDO offers vital advantages in terms of end-to-end use case coverage — including remote access and air-gapped environments — as well as ease of use and deployment.
Low-friction rollout
Noting that engineering and plant automation managers cannot afford to let anything impact productivity or safety, Gordon says admins have been able to keep anyone from coming into the environment, especially from IT, and making changes.
SDO’s approach does not require IT engineers to make changes to the network infrastructure or backend security and identity directories. In extreme cases where IT professionals have extremely small windows (less than an hour per year) to implement security updates, adding a layer of protection that removes certain risks without disrupting the network infrastructure makes a compelling value proposition for IT and OT alike.
Legacy app support
Hybrid IT/OT environments include highly specialized equipment and computers that may only do one thing, like open or shut down turbines. The Human Machine Interface (HMI) workstations used to configure these manufacturing environments may also be very old and based on legacy Windows environments.
By offering what Takepoint calls an “agnostic security overlay,” Octopus passwordless MFA helps to secure this environment with unrivalled support for legacy applications including Windows, MAC, and Linux.
Streamlines a phased IT/OT rollout
The manufacturing industry continues to undergo consolidation through mergers and acquisitions with phased network integrations creating a hodge-podge of technology that obscures user access and authorizations. These integrations and the related deployment of security solutions typically occur in stages.
SDO’s agnostic overlay approach allows IT and OT security admins to start with specific facilities or groups of early OT adopters and remain in control as they roll out MFA to all intended sites and departments.
End to end solution includes air-gapped facilities
Many energy, public utility, and manufacturing environments feature physically isolated or air-gapped environments that are not connected to the Internet or to company corporate networks. Air gap security includes extensive segmentation between different layers of the Purdue model and may require disconnecting Active Directory and other elements of security typically impacted by MFA.
To gain access to the depths of these environments, users must work their way through a complex maze or progression of identity verification. Those responsible for managing these facilities have traditionally relied upon “secure through obscurity,” but in reality, many service engineers leave unauthorized shadow IT access their equipment remotely inside these environments – 3G modems or remote access software for example – so they do not need to come back on-site to perform every update.
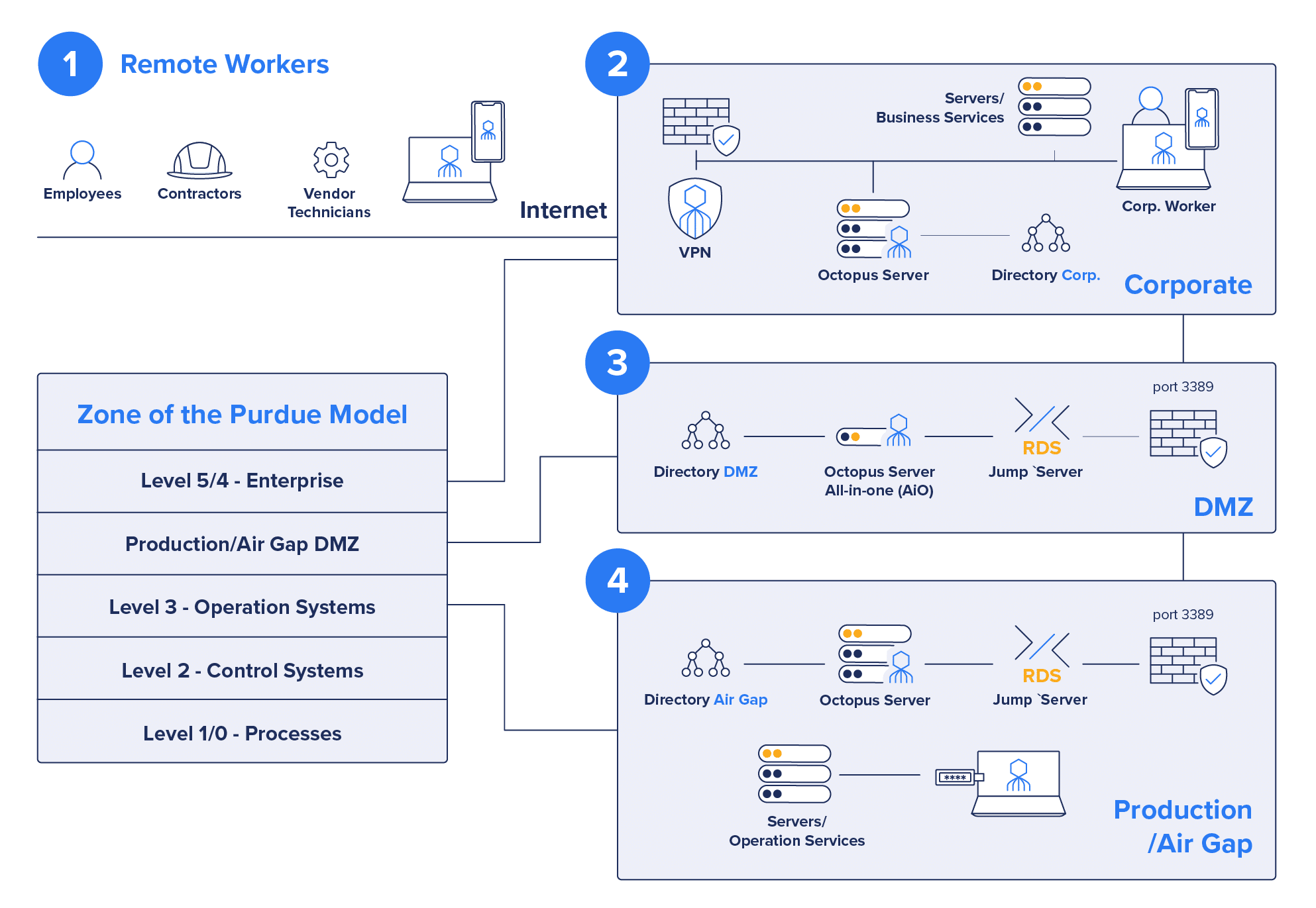
(1) Desktop MFA
(2) Corporate Level 4/5 access over VPN
(3) DMZ Jump Server
(4) Level 3, Air Gap Jump Server
SDO’s architecture makes it possible to extend secure identity verification with very granular control across the entire environment, including legacy systems in physically challenging locations, without impacting Active Directory and other back-end infrastructure components. The solution works for IT and OT, and local and remote access by employees and non-employees alike.
“And when something goes wrong?”
With traditional MFA, the loss of communications or too many failed attempts to enter valid credentials could result in a “lockout scenario” that causes an engineering workstation to go offline and bring production to a halt—something companies can’t afford to have happen. Taking user passwords out of the equation goes a long way toward avoiding disaster, and SDO also offers the option to revert to the use of passwords in extreme scenarios where lost time might mean millions of dollars or grave consequences for society.
Ready or not . . .
Regulators and governments will continue to turn up the heat around stopping phishing and evolving to least privilege, Zero Trust security postures. Enterprises in every sector will continue to invest in securing identity and achieving a deeper understanding of who can do what within their extended hybrid network environments.
Noting that the discussion should not be about MFA per se but rather about adopting a sound, proactive strategy for achieving phishing resistance, Gordon concludes:
“Industrial enterprises can use passwordless MFA to shorten that journey and actually leapfrog the security discussion from compliance to reducing risk. Based on our discussions with customers, we anticipate substantial growth in this opportunity to use identity as a defence strategy in the coming 2-3 years.”
As the goals and charter of MFA expand beyond checking the box on compliance to measurably reducing risk, the Octopus platform offers an OT- and engineering-friendly solution. SDO’s overlay approach makes it easy for critical manufacturing companies to move to the front of the line and adopt phishing-resistant, budget-friendly MFA that will meet their needs and satisfy changing security mandates for the foreseeable future.
For more information
Read the SDO whitepaper, Secure Access to Industrial Critical Infrastructure or visit the Takepoint site.