IT security teams constantly work to strike the right balance between user experience (UX) and protecting the company’s assets. With the mass adoption of two- and multi-factor authentication (2FA, MFA), most teams rolled out SMS authentication to verify identity — it’s familiar, mostly convenient, and affordable (since users already have the smartphones) — but sadly, not very secure.
In this article, we’ll explain why that is and how companies can evolve seamlessly to a stronger and smarter approach to authentication.
What is SMS authentication?
SMS authentication or SMS-based 2FA uses one-time passwords or passcodes (OTPs) sent via text to verify a user’s identity as they log into company accounts, databases, networks, and applications. OTPs have become quite common, so much so that, while they often require more typing and juggling of devices, most users don’t really mind them anymore.
Secret Double Octopus (SDO) estimates 70% of today’s MFA deployments use SMS messages sent to mobile phones to complete the second factor of authentication. Much of an enterprise’s workforce, many transacting from personal devices, use SMS all day long as they access Twitter, LinkedIn, Amazon, Instacart, DoorDash, and other services.
How it works
After entering their username and password to log into resources, an employee receives a text/SMS message with a 4- or 6-digit authentication code. They retype the code into the PC (or whatever device they’re logging in from) to access the app or website in question. SMS usually works well and provides instant access.
The easy choice may be the least secure
Where passwords represent “something users know” — the weakest possible pillar of identity verification — OTPs extend into the realm of “something users have” because presumably the user must have the right phone in their possession in order to get OTPs via text. Doing so creates true two-factor authentication that’s exponentially stronger than passwords alone.
SMS keeps things simple and affordable since no additional hardware or software is typically required beyond users’ own phones. But, SMS proves highly vulnerable to phishing, man-in-the-middle (MITM), and SIM swapping attacks which may present unacceptable trade-offs in terms of risk.
What makes OTPs so vulnerable?
Mobile phones come and go
In theory, a threat actor now needs to obtain both working credentials and have access to the associated mobile phone in order to compromise SMS authentication. In reality, our phones, like passwords, phones can be lost, stolen.
Data from Kensington suggests users lose some 70 million smartphones every year, only 7% of which get recovered. And, making matters worse, they can also get hijacked by diabolical modern SIM swapping attacks with relative ease.
Additional risk stems from the fact that users might receive 2FA messages on multiple devices, increasing the number of inflection points where bad actors can intercept OTPs without arousing suspicion. Wireless service providers might also let customers view text messages online where, if operators don’t adequately secure portals with MFA, data can become vulnerable. Bots, or patient threat actors can monitor these sites and read OTPs as they come across.
Password reuse
Despite the deluge of warnings, users continue to reuse the same passwords over and over. This persistent problem makes attackers’ job easier in launching a variety of automated attacks targeting passwords and MFA itself.
Obviously, users have their hands full trying to manage and keep track of 10 or more passwords a day. SMS does at least make sure that each OTP only gets used once.
UDP as the delivery mechanism
By default, SMS communications take place using UDP, a stateless protocol that’s significantly less secure – more easily spoofed and intercepted — than communicating via TCP. Because users register their phone numbers with an account versus pinning a messaging application to the physical device itself, there’s no way to ensure a text sent via UDP is actually reaching the intended physical device.
The use of UDP, by extension, renders SMS extremely vulnerable to modern attacks on authentication itself.
Social engineering
By nature people are trusting. Attackers exploit this human response to steal SMS codes, simply by asking for them. This is typically done by triggering a sympathetic response with a fake IT call asking for help in verifying that second-factor issuing is working correctly.
SMS simplifies SIM swapping
Sophisticated bad guys, and the bots they employ, can intercept SMS messages by taking control of users’ phone numbers without physical access to the phones themselves. SIM swapping attacks generally begin with social engineering. Threat actors monitor social media feeds to glean enough background information on someone to answer their security questions.
They then call mobile service providers and convince them to transfer all the data associated with a phone number to a new SIM card controlled by the hacker. Along with providing the bad actor with access to accounts accessed via the user’s phone itself, SIM swapping allows cyber criminals to intercept and use SMS authentication codes sent to that phone number as well.
Authorities warn SMS does not stop phishing
Industry guidelines for improving security now routinely call for MFA. But, the most progressive, like the Biden Administration’s Executive Order on Improving the Nation’s Cybersecurity, take a crucial next step by specifying phishing-resistant MFA for critical infrastructure and government ecosystems.
In its NIST Update: Multi-Factor Authentication and SP 800-63 Digital Identity Guidelines released in 2022, National Institute of Standards and Technology (NIST) writes:
All MFA processes using shared secrets are vulnerable to phishing attacks. MFA using (unencrypted) SMS/PSTN is recognized to be vulnerable to attacks. SP 800-63-3 cites these vulnerabilities and has RESTRICTED the use of SMS/PSTN.
CISA also stresses the need for phishing-resistant MFA leveraging FIDO and public key infrastructure (PKI) to secure government and critical infrastructure ecosystems. In general, the writing is on the wall for MFA that relies on passwords and SMS
Safer options emerge
Evolving standards and guidelines endorse FIDO2 and the use of public key cryptography, a far more secure approach that, to date, is available only for web-based services. Down the road, solutions based on PKI technology are expected to deliver more pervasive coverage.
In the meantime, mobile authenticator apps and non-SMS push notifications offer viable solutions. Apps such as SDO’s Octopus authenticator feel similar to SMS authentication but eliminate the risk. As users attempt to log in, the app can either generate an OTP locally — without a message going over UDP — or send a push notification asking a user to simply approve (or deny) the request.
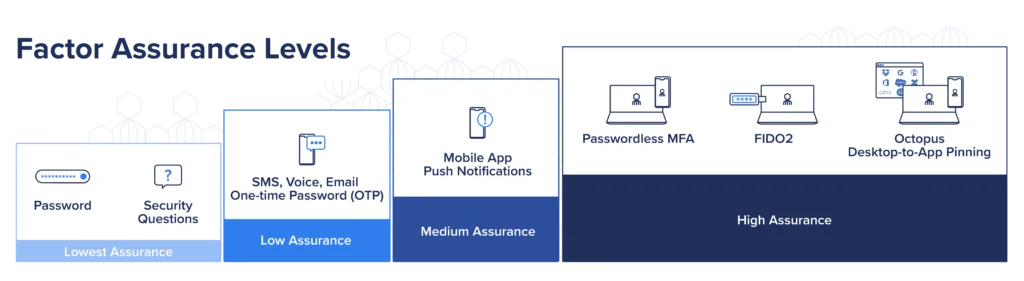
Passwordless MFA creates stronger authentication and a better, safer UX
When SMS first came out, users hated it. Who needed another step that took (read: wasted) time and meant having to keep your phone within reach at all times. Now, most of us do that anyway, and don’t think twice about SMS prompts.
The same thing is happening with push notifications and biometrics, and carrying hardware tokens or USB drives with us everywhere we go. Using our phones to authenticate has become familiar, but users still vastly prefer the simplicity of Passwordless, SMS-less logins. Fewer steps, and a faster overall process that doesn’t involve typing is ideal. Tapping an icon with your thumb, for example, is simple and much faster than going back and forth between login pages and SMS messages.
Other benefits of a Passwordless approach
Passwordless MFA:
Reduces risk by removing vulnerable passwords: Every year, research shows credentials play in a role in the vast majority of breaches. Taking passwords out of the mix cuts off the usual flow from phishing texts and emails to gaining initial access, depositing malware, and progressing laterally toward crown-jewel assets.
Alerts users to phishing and bogus prompts: With a passwordless approach, any SMS message or email that prompts users to enter passwords stands out, erasing any doubt that users should contact their organization’s administrator to shut down access.
Paves the way to Zero Trust, compliance, and lower cyber liability insurance premiums: By effectively shutting down phishing and requiring multiple reliable methods of identity verification, Passwordless MFA satisfies industry standards and security best practices such as the CISA Guidance on the Essential Critical Infrastructure Workforce. Doing so in turn aligns with Zero Trust and MITRE ATT&CK knowledge base recommendations for securing access and identity.
Gives IT fewer headaches: Eliminating passwords typically eliminates 40% or more of all calls to the Help Desk. The right approach – one that decouples the user login process from backend directory infrastructures — lets IT roll out passwordless MFA in about an hour without having to retool apps and directories. Then, IT can move to FIDO2 and PKI when and where they choose, without disrupting users.
Learn More
Ultimately, it’s better to simply get rid of vulnerable user passwords and SMS-based authentication factors and to remove “what users know” from the login workflow entirely. To learn more about replacing the tried and true—but inherently insecure—approach to MFA with stronger Passwordless authentication, learn more about the Octopus platform or contact us to see a demo.