Providing secure and easy-to-use authentication and login mechanisms should be one of the main goals every online service pursues.
Unfortunately, passwords, the traditional method to protect online accounts and keep intruders out, are becoming less reliable and more cumbersome to maintain, both for users as well as service providers. The industry has become desperate in needing a no-password option.
Where to go from here?
Fortunately, alternative, no-password login technologies exist that provide passwordless identity verification, and can help solve some of the perennial problems that stem from the use of passwords.
Why are passwords insecure?
There are many reasons why a password is no longer enough to protect a sensitive account. These days, a strong password is one that has a length of at least 10 characters and consists of letters, digits and symbols. Moreover, it should not be shared with any other service and should be changed every three months at the minimum.
It gets worse:
With users having dozens of email, messaging, social media, banking and other online accounts, memorizing and maintaining so many unique passwords becomes a burden. And every new account that a user creates adds to that burden.
That’s why users often neglect those requirements, choosing weak passwords, reusing passwords across accounts, and avoiding changing passwords. All of this makes them vulnerable to brute-force attacks, dictionary attacks, cross-service password breaches, and more.
Even seasoned users make such mistakes.
From a service provider perspective, passwords require a company to store secrets and burden them with the task of protecting those secrets.
Even the biggest companies have a hard time protecting password databases against data breaches.
Moreover, as users often forget their passwords, companies are required to store password hints and provide password recovery mechanisms, which opens up a Pandora’s box of vulnerabilities and attack vectors.
Get our free whitepaper about password vulnerabilities.
Password Manager Cons
When tasked with the challenge of storing passwords to dozens of applications and services, many companies turn to password managers. These applications help generate complex passwords that are more difficult to hack and protect all of your passwords in one place–but there are more cons than pros when it comes to password management.
- Single Point of Failure: One password protects all of your passwords. If that is compromised, then all of your passwords are subject to a massive data breach.
- Generated Passwords May Be Weak: While many password managers offer the ability to adjust settings on generated passwords, like character limit and type of characters, users may not be aware of these settings and make the mistake of generating a weak password that is easily hacked.
- Web-Based Application Vulnerabilities: Password managers don’t always recognize every web-based application, which means users have to call their passwords manually. Not only does this defeat the purpose of paying for a password manager, but it makes them susceptible to web vulnerabilities like bookmarklet flaws, iFrame phishing, and XSS and CSRF exploits.
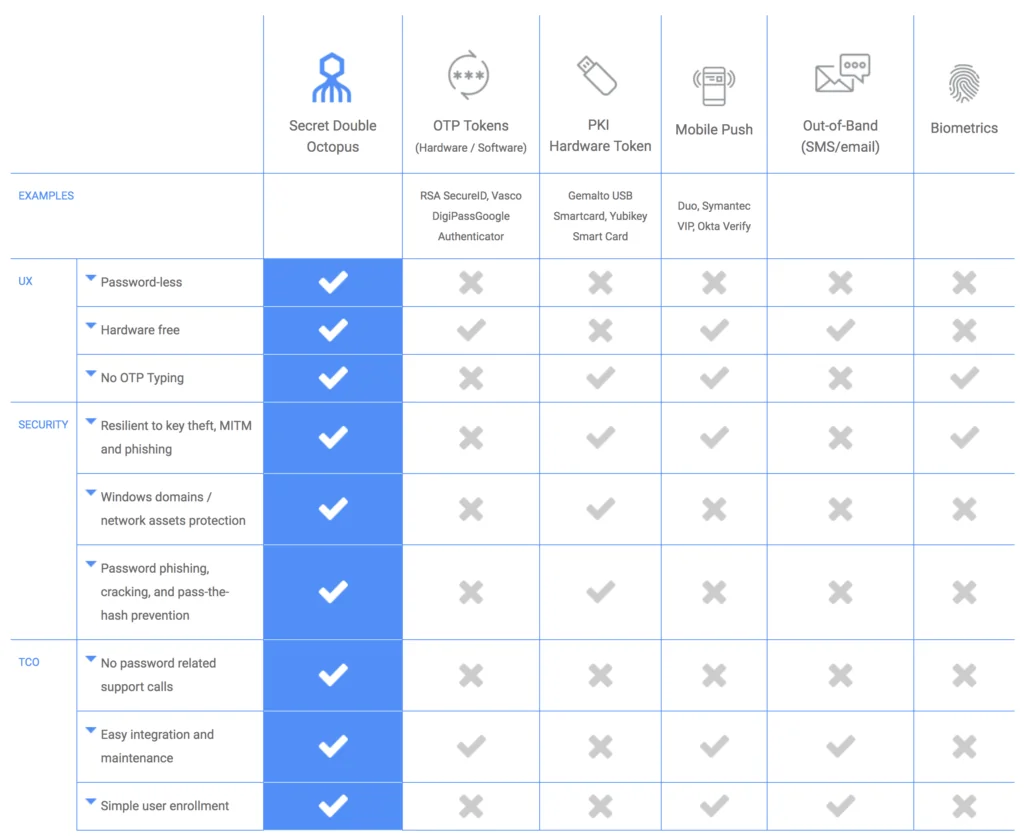
What are no-login password technologies?
The goal of passwordless authentication is to provide security that is on par with or superior to complex passwords while at the same time being as simple to use as password authentication, or simpler.
Some promising alternatives:
Biometric authentication
Biometric authentication uses biological input to verify the identity of a user. The implementation of biometric authentication used to be a complicated and costly process, but has become more accessible thanks to advances in smartphone technology.
Popular forms of biometric authentication include facial scanning, fingerprint scanning, retina scans and voice authentication.
One of the biggest hurdles to implementing biometric authentication is still the hardware requirements. Fingerprint scanners are only available on high-end, expensive devices that not all users can afford. This makes them less ideal for public applications that will be used by all kinds of users.
Also, there are many settings where biometric authentication can go wrong, which always makes it necessary to couple it with some other form of authentication.
One-time passwords (OTP)
One-time password is an authentication mechanism that uses a non-persistent secret, usually a short passcode that is valid for one session. Upon every login attempt, a passcode is generated and sent to an associated phone number or email address, which the user has to enter in the login page in order to access the account.
The passcode is only valid for the duration of the one session. Any subsequent logins will require a new passcode.
OTPs have the benefit that they do not require the service provider to store permanent passwords on its servers, making them considerably safer than normal passwords.
However, an insecure implementation can open up its own set of vulnerabilities. For instance, sending OTPs through SMS is no longer considered secure due to the risk the channel through which the message is generated becoming compromised.
The complexity of the process in comparison to entering passwords is one of the factors that has resulted in OTPs not being very popular among users and leading to their adoption as a secondary authentication mechanism rather than the main way to verify user identity.
Authenticator apps
Authenticator apps use a mobile application to verify user identity. When signing up with a service, users install the authenticator app on their mobile device and associate it with their account.
When users attempt to access their account, instead of prompting for a password, the service sends an access request to the associated device through the authenticator app. After the user approves the app request, access to the account is granted.
Authenticator apps are rising in popularity because of their added security, frictionless experience and the fact that mobile devices are becoming ubiquitous. Google and Microsoft provide authenticator apps for their own services as well as an extension that you can add to your own website.
Multi-Factor Authentication
Alternatives to passwords must include multiple factors to maximize security. Any combination of the above factors–plus a litany of others–applied at the enterprise level make your information more secure and provide your employees with a seamless user experience that optimizes productivity.
The Double Octopus authentication solution provides the ease of use attributed to authenticator apps and uses the secret-sharing mechanism to eliminate the vulnerabilities that other solutions suffer from.
Find out more about Double Octopus authentication solution here.