Shared accounts are any resource that uses a single pair of credentials to authenticate multiple users.
Shared resources can be tied to any platform or network tool, from email accounts to servers and databases, increasing the complexity of securing shared accounts.
While shared accounts are not considered best practice, an organization may end up using shared accounts for a variety of reasons. Sometimes the particular online tool leaves no other option. Email accounts, for instance, can only be accessed by one set of credentials. Regardless of the reason, shared accounts present a host of security risks to the network.
The challenges shared accounts hold for IT:
Activity Tracking and visibility:
The basic premise of identity and access management (IAM) is knowing who accessed which resource. Shared accounts create a major hole in this regard. If a shared account is breached, for instance, knowing which user was logged in at the time is a big part of mapping the attack chain of the incident.
![]()
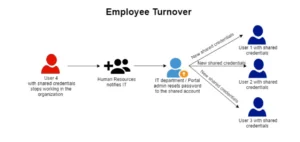
Employee Turnover:
The natural flow of business means employees move around within the organization. They switch departments or leave the company. For an organization to change credentials every time a user with shared-account access leaves or switches departments is not only unscalable, but it’s also impractical, and leaves a lot of room for human error.
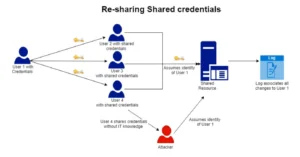
Re-Sharing Shared Credentials:
The lack of monitoring on shared accounts leaves a major missing parameter in the identity and access policy of a company — what was shared could be shared again, within the company or with unknown actors that can assume the identity of legitimate users — which can cause corporate account takeover (CATO).
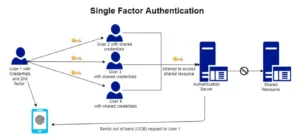
Single Factor Authentication
Today, best practice is to utilize Multi-Factor Authentication on every resource, and shared accounts are tied to one set of credentials, making MFA/2FA impossible.
See How Secret Double Octopus Solve the Shared Account Challenge